Vulnerability Management System: The Definitive Guide (2022)

Vulnerability Management System: The Definitive Guide (2022)
Cyvatar | 04/21/2022May 2017, a significant time in the world of cybersecurity, is upon us. Have you heard of the infamous WannaCry ransomware attack? This is when it happened.
The ransomware crypto worm targeted computers that ran the Microsoft Windows operating system, encrypted their data, and demanded ransom payments in Bitcoins.
It is said that a Server Message Block (SMB) port was exposed and vulnerable, which led to the first infection.
It affected more than 200,000 computers across 150 countries within a day. More than 50 organizations across the globe have confirmed that they have been victims of it. The losses are estimated at $4 billion by cyber risk modeling firm Cyence.
Could the companies have avoided such losses?
The news article states that Microsoft Windows previously released a fix, but most organizations had not updated their systems. That’s the problem.
This is where having a vulnerability management system becomes pivotal. In this definitive guide on the vulnerability management system, we focus on everything surrounding this topic.
What is vulnerability management?
The vulnerability management lifecycle is a well-known cybersecurity practice that helps an organization anticipate and respond to threats better.
By adopting and implementing a robust vulnerability management program, businesses can continually improve their security prospects and ensure security of their critical systems.
What should be the goal of an effective vulnerability management system?
It needs to have the following goals:
- Providing a platform to identify internal and external vulnerabilities on time.
- Understanding in real-time, the security position of the organization.
- Reducing the security threat profile of the organization and bringing it to a level that is deemed acceptable.
- Mitigating the time taken to respond to security threats.
ASK THE FOLLOWING questions before going through the vulnerability management process
- Do you have a vulnerability management system in place already?
- What is the formal patching process that you follow?
- Does the organization have any processes or policies for vulnerability management?
- What are the internal system components in the IT department?
- What are the different types of data stored in the organization?
- Do you have the systems and data segregated based on their business value?
- What are the existing controls in place to support data and systems integrity?
- What are the existing controls in place to support data and systems availability?
- Do you have any intellectual property assets that would require more layers of protection?
Answering these questions will help you identify the most critical assets and give you an idea of what needs more focus and effort.
DO THE FOLLOWING for effective implementation of the vulnerability management system
- Have a clear understanding of business objectives and requirements.
- Understand the various vulnerabilities that they could face and how they will impact the organization.
- Identify assets that support business-critical processes and segregate them based on their value in conducting day-to-day operations.
- Have a complete understanding of where the assets are and who owns them in your company.
- Create policies and processes to support the vulnerability management system.
Challenges to overcome for organizations that plan to set up a vulnerability management system
Vulnerability management is no easy joke, and it involves a lot of complexity, not only in terms of choosing the features required but also with respect to what organizations should do and how employees should take responsibility for it.
Let us look at some of the challenges that businesses need to navigate through.
1. Understanding the risks associated
Organizations should be aware of the risks associated with not understanding the threats because it will result in delayed responses to technical vulnerabilities and flaws.
Some of the technical vulnerabilities can include loss of data due to control failure or a breach, reputational damage, systems compromised because of denial-of-service attacks, inability to recover on time, and so on.
Your IT systems’ being vulnerable can have negative impacts on your business and will have an effect on your day-to-day operations.
Having effective vulnerability management procedures is crucial towards protecting your critical systems and the business processes they support.
Having a vulnerability management system in place helps you make informed decisions about your technical vulnerabilities.
By proactively managing your risks, you can budget spending and allocate resources to take care of vulnerabilities.
2. Identifying assets
An effective vulnerability response would be to have an accurate update of all your assets. If you do not have a clear understanding of where your assets are, you might miss out on monitoring important ones that could be highly vulnerable to risks.
In such cases, the business will be unable to calculate the organization’s threat profile. The unknown assets might be how attackers make their way into your systems to access sensitive information or to create mayhem in your internal systems.
Conduct a discovery scan against all the systems to build an accurate asset inventory. Once all the assets have been mapped, they can be noted down on a register where management will have clear visibility.
| Prevent Plan subscription provides fully managed asset management |
3. Figuring out asset ownership
One of the challenges that most businesses face is defining IT asset ownership. When ownership is not allocated, it becomes difficult to resolve issues in a timely manner.
In large organizations, vulnerabilities are identified and escalated through different channels. It is imperative that you have a clear, transparent, and accountable approach to vulnerability remediation.
For the above to happen properly, management should allocate ownership of IT assets so that its responsibility is clearly defined. After the assets are allocated, the owners of these assets should be held accountable for remediation activities.
4. Remediation based on the criticality of the assets
A common mistake made by organizations is to remediate based on the criticality score of the vulnerability alone.
Instead, organizations should use vulnerability scoring and asset criticality to rank remediation efforts. It will reduce the chances of increasing risks.
To achieve this, the management should identify criticality scores for all IT assets. The valuation of an asset should be agreed upon at a strategic level.
The organization should also define the time frame within which remediation efforts should be completed. They should not only meet industry best practice guidelines but also keep the risk appetite of the organization in mind.
If critical problems are found in important IT assets, then they should be fixed right away.
5. Not being clear about a vulnerability management system
There are times when the management is complacent with an automated vulnerability management program in place.
While an automated vulnerability management solution offers insights, it offers limited value. For the program to be successful, it should follow well-tested and recommended policies and procedures.
Strict policies and procedures will ensure that employees are aware of the steps that they should follow and the responsibilities they should be shouldered with. Following them will ensure a structured and easily repeatable process that yields results.
By doing so, vulnerability resolution is handled in a consistent and highly effective manner.
By implementing processes and policies for your vulnerability management program, the organization will be able to effectively conduct activities like false-positive identification, asset inventory management, timely remediation, issue prioritization, and assignment of ownership.
6. Not having an escalation process
You will find that a business unit or a random team is not remedying the issues identified within an acceptable time frame.
If the business process that needs remediation is a service that cannot be down, then there should be an escalation process where concerns can be raised with the management.
The objective is to make the management realize the risks of not remediating the vulnerability. Following such an escalation process will allow the organization to make informed decisions.
Stages of Vulnerability Assessment Cycle
Vulnerability management is a complex process that has to go through a myriad of steps to succeed.
Let us look at the various stages of the vulnerability assessment cycle.
1. Assets Discovery
Being aware of all the assets within your network is the first step towards keeping yourself safe.
Taking an account of your entire inventory will help find vulnerabilities. Finding the baseline will help you identify anomalies. Scan entire systems through vulnerability tests.
Include every single company asset, such as business processes, applications, services, network infrastructure map, critical assets, information protection process, and previous control systems.
Once you have all your assets in one place, you should rank them according to how important they are to the organization, find out who has access to them, and who manages them.
Doing this consistently will help you stay on top of your network vulnerabilities.
2. Asset Prioritization
Locate the most critical assets in the organization based on how important they are for day-to-day business operations.
There will be assets that are more valuable than others. So, you need to put a business value on each of the assets to prioritize them.
There would be some assets that are more critical than others, even if they don’t offer a high monetary value. Ensure that you prioritize the assets that are highly risky when neglected. Create a process where any issues with these assets are immediately remediated.
3. Proper Assessment
Once the assets are organized and prioritized, the next step is to do a proper assessment of your assets.
Create a risk profile for each of them. Use a baseline risk profile and eliminate the risks according to the threats.
You need to perform vulnerability scans during this phase. The business should do it on the web servers, operating systems, web applications, and so on.
You need to examine the physical security that you offer the assets. Is there a case of a wrong configuration of your physical assets? Find out every single vulnerability possible and de-risk the asset.
4. Reporting
The data that has been collected about the vulnerabilities should be compiled into a report which outlines the vulnerabilities and priorities, including details on how to address them.
It is useful for personnel to provide adequate recommendations. It should include step-by-step instructions that should be followed to troubleshoot the vulnerabilities.
By doing so, you will effectively reduce the security risks that these assets pose.
You can measure business risk based on the importance of the asset to the organization and the internal security policy.
To ensure safety of these assets, document the security plan and monitor any anomalies that emerge.
When reporting the vulnerabilities, classify them based on how impactful they are to the organization.
5. Remediation
Once you have prioritized the assets, you should start by troubleshooting the riskiest. Ensure total control over the process so there aren’t any inconsistencies in following the due process.
The right steps to follow here are: monitoring the risky assets, assigning tickets to vulnerabilities, and managing any exceptions. Correcting the vulnerabilities is of prime importance at this stage.
Outline the steps that you should follow to collect the vulnerabilities, including how to update relevant patches.
The steps should be followed every time you encounter a vulnerability. There are times when simply patching the software is more than enough to address a vulnerability.
To ensure that you are in a position to handle threats, make sure to monitor the network devices regularly.
When you are troubleshooting a device: check how easy it is to fix, what the severity of the vulnerability is, and how critical the device is to your day-to-day operations.
It is imperative that you have a plan of action document in place to follow a standardized procedure.
6. Verification
Once you have resolved the vulnerabilities, ensure that there are constant audits to see that the risks don’t surface again.
Follow a standardized procedure that is transparent and accountable to other stakeholders.
By following a thorough verification process, you will be able to reduce the attack surface of a company and possibly minimize attacks by cyberterrorists.
The verification process also lets you check whether the previous phases have been successfully implemented.
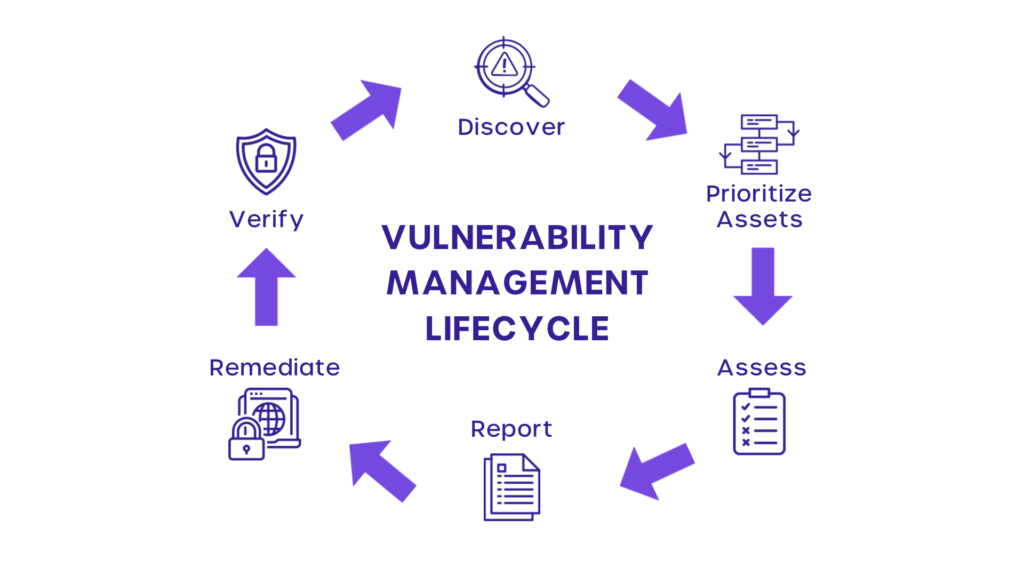
The above is a visual representation of a vulnerability management process flow chart. It shows each of the steps that we have explained in detail.
Benefits of effective vulnerability remediation
There are a myriad of systems and networks that keep organizations running. It is pivotal for day-to-day operations, and even if one of them stops working the way it should, it can negatively impact the organization.
Having a powerful vulnerability management system in place will protect you against cyberattacks, but if you neglect a vulnerability, even a tiny one, it can balloon into something significant and terrifying.
Let us look at some of the benefits of a vulnerability management system:
1. Better security and control
When you run vulnerability scans occasionally, they will only give you the status of the asset during that point in time.
This makes it difficult to monitor the vulnerability resolution’s progress.
The grave question to ask is what will you do if the vulnerabilities occur between scans? When will they get fixed? Will it be during the next vulnerability scanning that may take a month or more? If that’s the case, then your security process is in shambles.
If you don’t have a robust vulnerability management system in place, the chances of your website or applications being susceptible to attacks are always high.
Attackers need only a small point of entry to cause a breach. You cannot afford sloppy security processes.
A long-term vulnerability management program will give you an updated status of your security and you will find it easier to identify priority areas to prevent specific vulnerability types.
2. Greater Visibility and Reporting
When there is centralized monitoring, it allows for operational efficiency which also helps with visibility.
Compiling reports of the vulnerabilities of each IT asset manually will just result in a lot of information that will become obsolete by the time you share it with the organization.
If your organization relies on vulnerability scanning on an ad-hoc basis, the above scenario is exactly what happens.
With a vulnerability management system in place, you will get clear and highly rich dashboards with actionable insights.
It will show the real-time vulnerability status that will help you make important decisions. The updated reports can be generated by personnel in various capacities.
Using the reports, you can make changes to your incumbent security processes. You don’t have to rely on your gut or intuition to make security decisions that will affect your entire organization.
3. ROI in Security
The return on investment for security solutions is almost impossible to calculate without solid facts to back it up.
Having a dedicated vulnerability management system makes tracking incidents much easier. It will help you identify the improvements that have taken place across assets, time periods, and teams.
One of the biggest advantages of such a system is that it offers an extremely short time-to-value when you compare it with other approaches.
The vulnerabilities that are identified and classified are almost always ready to be fixed, eliminating the requirement for verifying them manually, thereby reducing the overhead costs by a huge margin.
Thanks to the reporting and visibility that it offers, organizations get the maximum possible security with the least amount of effort.
4. Manages your cybersecurity weaknesses
One of the most common cybersecurity vulnerabilities resides in technologies and user behavior.
The breaches could be due to insiders who accidentally leak information or do it intentionally, lost or stolen devices that contain unencrypted information, and cyber terrorists who install malware on your systems.
A vulnerability management system helps avoid data breaches. The best part about it is that you never stop doing vulnerability scans at all, when one gets over, the next one starts.
You will identify, evaluate, remediate, and report your security vulnerabilities in user applications, servers, operating systems, enterprise applications, and browsers.
5. Better patch management
Cybersecurity vulnerabilities keep popping up by the thousands, and organizations are forced to patch their operating systems and applications regularly to reconfigure their network settings.
Unfortunately, most businesses do not have a patch management program in place and fail to apply the patches on time.
According to the Ponemon Institute, more than 60% of cybersecurity breaches in 2019 could have been entirely avoided if companies had patched their known vulnerabilities on time.
The average corporate network has thousands of vulnerabilities, and ensuring that everything is patched is almost an impossible task.
However, with a vulnerability management system in place, you do not have to worry about patching on time at all as the most high-risk vulnerabilities will be addressed.
6. Reduces operational vulnerability
The first step to nullifying the vulnerability is scanning them. After the scanning, you have to verify, assign urgency, and solve them.
With a vulnerability management system in place, identifying sensitive data, identifying possible threats, and analyzing security holes and vulnerabilities becomes easier. This helps reduce operational vulnerabilities.
7. Saves time
Thanks to regular vulnerability monitoring, organizations will be well-prepared to face any kind of security threat in real-time. They will fall victim to cyber-attacks pretty rarely.
Working on solving a data breach is more time-consuming than indulging in a vulnerability management system that checks for vulnerabilities every now and then.
| For any midsize organization, there are some 4,000 IPs out there to monitor, for example. With your vulnerability scanning, you found some 1000 vulnerabilities. Applying the high-low scoring industry methodology, you may find some 300 high-priority vulnerabilities out there. That’s a huge task to do. If you look at maybe 5 minutes for investigation and 25 minutes for remediation, you invest 30 minutes for each vulnerability. That’s 150 hours to go through the full vulnerability assessment and remediation process! Using a more granular scoring approach, you can further narrow down the high-priority vulnerabilities to 200 with a fully managed vulnerability management system. Using options such as pentesting and vulnerability validation tools, one can check out those 200 vulnerabilities and see in the marketplace what types of malware, exploits, or kits are out there that people can buy to attack your organization. Using a comprehensive vulnerability management tool, you could take those 200 vulnerabilities and bring them down to 50 vulnerabilities. This is a much easier task for your organization to manage. |
8. Minimizes IT workforce
The presence of an integrated vulnerability management cycle reduces the burden of the IT workforce to a huge extent.
The IT workforce required to reduce vulnerabilities, data breaches, and strengthen the cybersecurity system will be smaller in number.
Thanks to this, you will be able to prioritize the threats that need immediate remediation based on the risk factor that they pose. It will reduce the confusion in the remediation process.
How to choose a vulnerability management solution?
Vulnerability management is more than just a vulnerability scanning tool. Using the right tool can make your vulnerability management successful.
There are a number of tools available on the market that claim a litany of features and functionalities.
Let us look at how you should evaluate a vulnerability management solution tool while choosing one for your organization.
1. End performance is important
Most of the vulnerability scanning tools claim to offer agent-based solutions. Most of the agents are bulky in nature, thereby affecting their endpoint performance.
When you are searching for a vulnerability management tool, ensure that it is a lightweight one. A tool that is light in weight will consume less space and won’t affect productivity.
2. Provides real-time visibility
The vulnerable assets in your systems should be immediately visible. Using legacy vulnerability tools can be a great hindrance as the network scanning process might consume more time and give you results that aren’t real-time.
The outdated results will be of no use at a time when cyber terrorists are looking for the smallest of vulnerabilities to breach and enter. Your vulnerabilities should be addressed in as little time as possible.
The vulnerability management system you choose should allow your team to see and interact with the data in real-time.
It should offer a dashboard that has search and filtering options to identify high-risk vulnerabilities. It should be on the lookout for vulnerabilities constantly.
3. Detects vulnerabilities in a timely fashion
If the vulnerability lifecycle doesn’t identify vulnerabilities in a timely manner, then the tool isn’t going to be really helpful as you will not be able to act at the right time.
Network-based scanners fail when it comes to timeliness, consume a lot of time to complete the scanning, and take up most of the organization’s bandwidth- all of this to give you obsolete data.
4. Provides contextual insights
Determining the level of risk of the asset requires a lot of data. The data points must be correlated and analyzed to provide the necessary context to understand the real risk faced by an asset.
The vulnerability management platform should be able to predict the impact of events if the vulnerability is exploited by cyber terrorists.
5. Risk scoring system
The vulnerability remediation process should have a risk scoring system that communicates risk in a way that all stakeholders can understand.
A highly advanced enterprise vulnerability management solution will allow you to assign a risk score to any asset group, and the vulnerability manager will take over from there.
6. Interoperability with the existing IT systems
Any IT executive will be wary of getting locked into an IT infrastructure that doesn’t allow them to operate in tandem with other systems.
When looking for application vulnerability management, choose something that is easy to connect with 3rd-party scanners, asset management databases, and so on.
7. Centralized Risk Management
Having a centralized risk management solution will allow you to handle any type of system vulnerability effectively. How?
They provide a single consistent view for vulnerability management reporting as your team has full control and visibility of your on-site and remote assets, applications, and cloud services.
All-in-one centralized dashboard by Cyvatar
8. Enterprise features
Since the network size of enterprises is too big, the infrastructure required for them to fight is also completely different from working with small and medium-sized businesses.
Here are the following questions that you need to ask while choosing a vulnerability management system:
- Does the product assess workflows?
- Is the product scalable?
- Does it track impact analysis and risk analysis?
- Does it integrate easily with other security systems?
- Is the tool able provide automated trouble-ticketing tracking and status reporting?
A tool for enterprises should prepare several reports when testing tools for vulnerability management so that relevant information can be passed to the stakeholders.
Vulnerability Management Tools
Your security solution should not be based on reactive MDR and XDR but rather a proactive, preventive approach. The vulnerability management tool should be part of a comprehensive preventive security tool.
Cyvatar’s fully managed solution is one of its kind to provide preventive solutions. Cyvatar is not only customizable based on your organization’s specific needs but also scalable as you expand without making a hole in your digital wallet.
Cyvatar offers an executive dashboard that helps you view your strategy, execution, and results on a single dashboard. It even lets you see the vulnerabilities that are being remediated and tasks completed in real-time.
The dashboard is easy to understand and you can map it to your business goals. Cyvatar promises less than 90 days for your team to go from installation to remediation.
However, on average, Cyvatar has been able to reach value for customers in less than 60 days.
The vulnerability management system also comes with an interactive heatmap that shows the common risks so that you can invest in remediating the cyber risks that need to be immediately addressed.
The heatmap also shows the impact and likelihood of the risk that it poses to your day-to-day business operations.
Cyvatar’s ICARM methodology ensures continuous cybersecurity.
- Installation
- Configuration
- Assessment
- Remediation
- Maintenance
Learn more about effortless, and continuous cybersecurity. Connect with one of our cybersecurity experts.
