A Single, Intuitive Platform For Fully Managed Cybersecurity
Say goodbye to multiple security tools that don’t give you a clear picture of strategy, execution, and continuous resolution. Say hello to the Cyvatar Platform.
A Reinvented Way to Manage Cybersecurity Operations.
The Cyvatar Platform is a hub for your entire security tech stack; ingesting data from your tools, then translating it into beautiful dashboards that are automated, easy to understand, and mapped to your business goals. Whether you need executive-level metrics for your board meeting, want to see how our team is remediating your issues, or are working towards compliance — the Cyvatar Platform has it all!
What’s New on the Cyvatar Platform?
What’s CyValue?
Cybersecurity Installation to Remediation in 90 days or less.
Proof of Concepts are a Waste of Time. Get Smarter and Faster Security ROI with The Cyvatar Platform.
<90 DAYS
TO REMEDIATION
Our team ensures your strategy goes from Installation to Remediation in 90 days or less. (That’s what we promise with CyValue.)
<60 DAYS
TO CYVALUE
On average, our customers are reaching CyValue in just 60 days or less!
<24 HOURS
TIME TO ISSUE RESOLUTION
Cyvatar Cydekicks are speedy, resolving an individual issue in one day or less!
A Single Pane Of Glass into Your Cybersecurity and Remediation.
Executive Dashboard
See your cybersecurity strategy, execution, and results in a single dashboard. View Cydekick results, CyValue scoring, compliance assessment, and much more.
Issues Management
See vulnerabilities being remediated and tasks completed in real time.
MyCySO
MyCySO powers is a one-stop shop for managing your company’s cybersecurity policies, trust-building, and business risk assessment.
Trust Builder: Documents customized to your organization to allow stakeholders and customers to have trust in your cybersecurity posture and program.
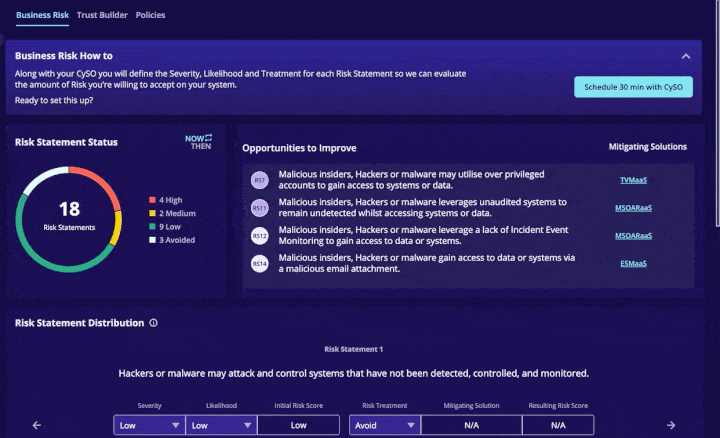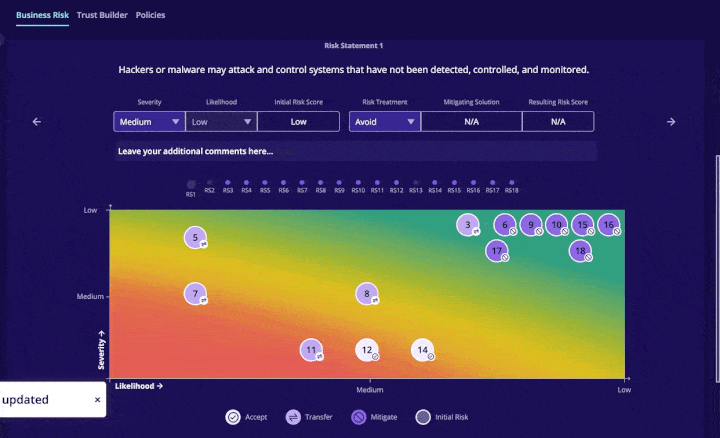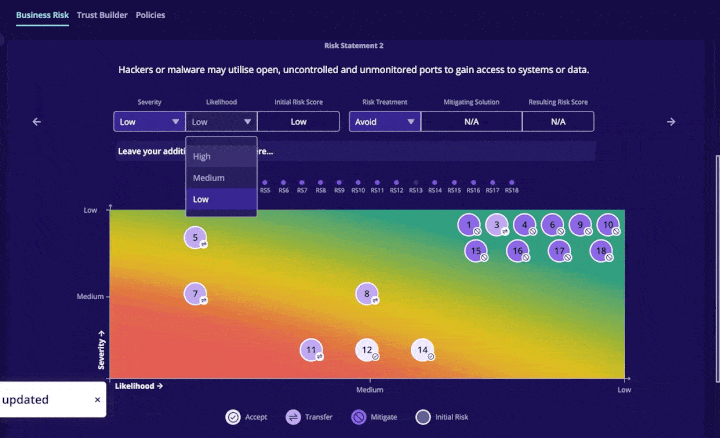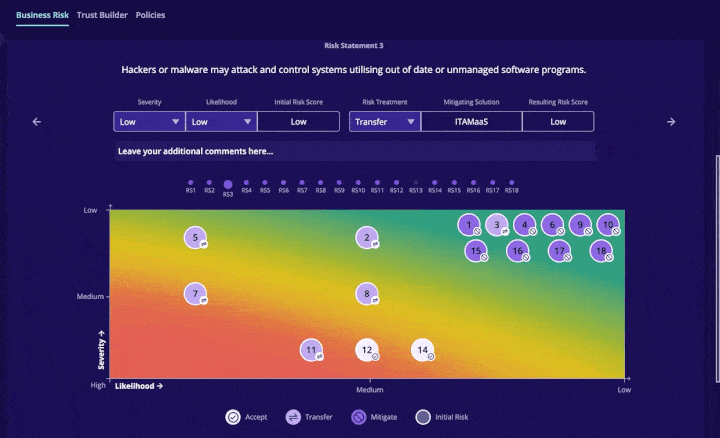
Business Risk: This tool is an interactive heat map that plots common risk, so you can concentrate on remediating your highest cyber risks in order of priority with your CySO. You can decide to accept, transfer, mitigate or ignore cybersecurity risks and see where they fall on the heat map scale: including impact and likelihood.
Your All-in-One Operating System for Cybersecurity.
The Old Age
Multiple point solutions with no meaningful data that maps to business outcomes with no single repository for your solutions, compliance, and ROI reporting
Reports and tests without any remediation, and certainly no continuous remediation
Cumbersome security questionnaires that extend the sale lifecycle
The Cyvatar Age
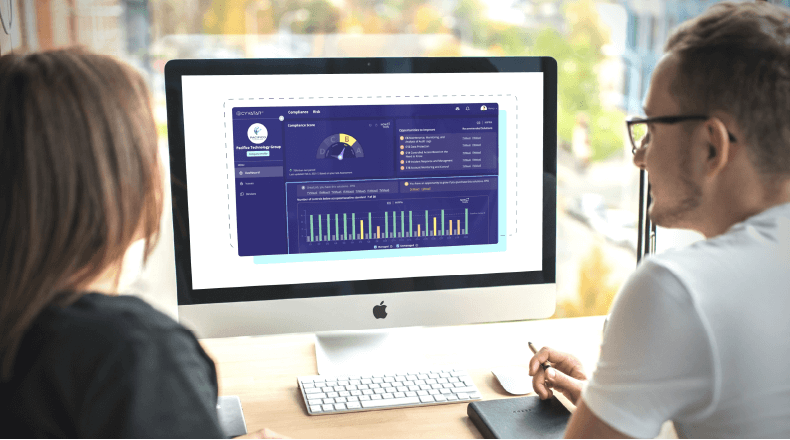
One single pane of glass in a dashboard with insights that show cybersecurity value
CyValue scores | Cydekick remediation results | Compliance score
DIY Assessment and transparency into remediation
Proactive Trust Builder that informs your customers and stakeholders on the business’ security posture to support security questionnaires
Effortless cybersecurity is at your fingertips.
Resources, Tips,
& Tricks
Get access to Cyvatar’s security expertise, proven solutions, and the services to make it all happen.
