Threat & Vulnerability Management (TVM) for Your Business
across your organization

Your Network is Under Continuous Attack
You need continuous monitoring, scanning, and remediating; not to mention penetration testing and meeting compliance requirements.
Assessing and remediating vulnerabilities present in your network can detract focus from your growing business and can be time consuming for your team to manage.

Are You at Risk of a Breach?
Managing vulnerabilities in-house is rarely done comprehensively, exposing you to attacks. To ensure remediation is occurring consistently will only detract your valuable resources and time from what’s really important.
That’s why it’s time to work with a partner who can take care of both identifying and remediating your risks continuously. Then, you can get back to focusing on your business.
You Need a Digitized Solution for a Digital Age
The Old Age
| Task | Estimated Time |
|---|---|
| Evaluate vulnerability scanners and purchase | Several months |
| Set up and compare internal/external environments | Several months |
| Random scanning and assessing | Several weeks |
| Determine critical risk priorities | Several weeks |
| Remediation: patching and annual review | Sporadically |
| Patch management | Sporadically |
| Complete pen test | Several months |
The Digital Age
Purchase a threat and vulnerability membership that takes care of this entire process for you, and be set up in less than a week.
Time estimate: CyValue means you will get from Installation to Remediation in 90 days or less.
Learn how Cyvatar provides game changing cybersecurity by remediating your vulnerabilities ›

Your Threat & Vulnerability Problem
Digital assets change constantly.
Are you on top of the change?
If your company is like most, you’re responsible for a threat and vulnerability cycle that not only takes months to complete, but rarely ends in remediation. Or you’re paying a company to identify threats, but at the end of the day, you’re the one responsible for remediating them.
You’re also responsible for a process that could take upwards of a year:
- Choosing scanning tools
- Installing software
- Configuring software
- Scanning continuously
- Patching continuously
- Project managing remediation
- Remediating any new threats
You don’t have the time or energy to deal with ongoing threat and vulnerability management, penetration testing, patching, and remediation.

Your Cyvatar Solution
Here’s the awesome news: we’ve effectively solved the threat and vulnerability management conundrum.
People. Process. Technology.
When you work with Cyvatar, you get cybersecurity-as-a-service with more robust people, process, and technology than you get anywhere else.
That means not only best-of-breed technology, but the best people to put it in place and the right process to keep your cybersecurity solution running smoothly.
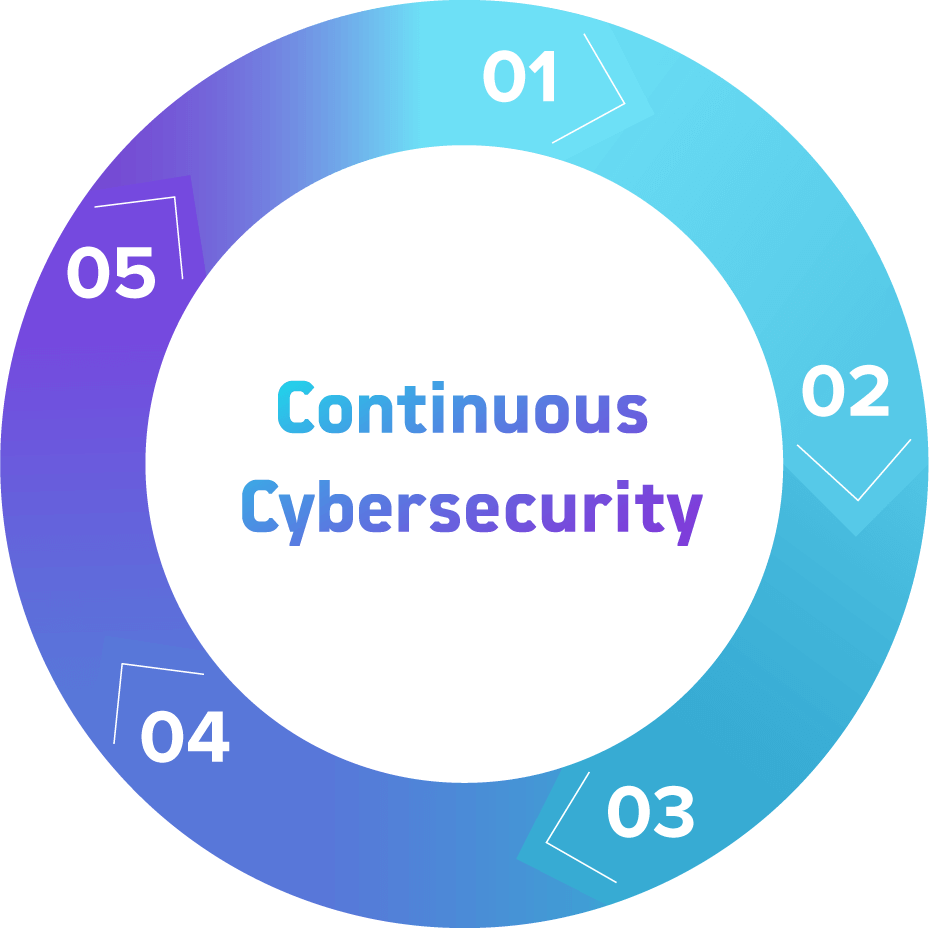
Cyvatar’s ICARM Methodology
1. Installation
The solution is implemented and installed.
2. Configuration
The technology is configured properly.
3. Assessment
An assessment is performed to identify risks.
4. Remediation
Remediation of the risks that were identified is performed.
5. Maintenance
Continuous maintenance and monitoring with monthly exclusive reporting. Repeat.