What can the cybersecurity industry do for startups?

What can the cybersecurity industry do for startups?
Cyvatar | 02/21/2022How can cybersecurity help startups?
Cybersecurity is necessary for a business, regardless of its size. Be it a small business, an early-stage startup, or a mega-corporation, data breaches and threats can be crippling and can lead to losses that can run in the millions.
The most common misconception for new business founders is that no one would aim to target a small or emerging business until it does.
According to a 2019 Hiscox Cyber Readiness Report, 65% of all businesses in the US experienced a form of cyberattack.
Furthermore, the report states that 60% of those attacked businesses had to shut down within 6 months after the breach.
Another factor to remember is that cyberattacks can cost a lot of money – upwards of $100,000 for small businesses and millions for larger corporations. And when ransomware is in the picture, clean up and costs are much steeper.
From the same report by Hiscox, losses and recovery from cyberattacks can cost a business around $200,000! For a new business, such losses can be crippling.
Did you know that it takes a business an average of around 280 days to recover from a data breach?
According to Security Intelligence’s 2020 Cost of a Data breach report, 280 days is the average time it took for companies to recover and 76% of those companies surveyed expect the recovery time to be longer if they had to shift to a remote working model.
That’s a lot of time and money spent away from growing a business, isn’t it? Operational downtime is also a consequence of a data breach and can last up to days.
One of the scariest outcomes of ignoring cybersecurity for your business is the loss of trust with your customers.
Imagine a data breach, and the private and banking information of your customer base has been exposed and is now vulnerable. It’s a public relations nightmare, and corporate embarrassment travels faster than fire in the woods and your business would be labeled untrustworthy and unreliable.
It would be a painstaking ordeal to earn back the trust of your customers, and even harder if you have a new business or startup.
Why would hackers want your startups’ data?
You must be still wondering, why would hackers and cybercriminals be interested in your data?
Hackers could be hired from rival companies to steal your Intellectual Property, your innovations, and business ideas before they can come to life!
Hackers could steal your customers’ private information, social security numbers, credit card information, any data that allows them access to your customers’ money or assets.
They can even use your business as a stepping stone. Hackers can hack and gain access to information on your investors, clients, and partners. They could be aiming to steal from bigger fish that are helping your business, eventually.
What kind of cyberattacks can your business expect?
Hackers are always looking for innovative ways to breach and access your data. Here are some of the more common ways a hacker can gain access to your data:
Phishing Attempts
Phishing is a tactic used by hackers to lure unsuspecting or non-tech-savvy users into clicking a suspicious URL from an email.
If you’ve ever noticed a suspicious email from an unknown source in your inbox with an attachment or link, that’s most likely a phishing attempt.
However, as the internet gets more and more complex, hackers have evolved to make their phishing attempts look as legitimate and unsuspecting as possible.
The consequences of clicking or opening these suspicious links or attachments could lead to malware being installed on your computer or mobile device.
Ransomware Attacks
Ransomware is just what it sounds like, ransom. These forms of attacks are apps and programs that claim to scan for a virus or provide a free service but then lock the user out of access.
Users when rebooting their systems are greeted with a virtual ransom note that prevents them from accessing their files and computer until they pay a fee to a random individual (most likely the hacker).
There have been many cases where such programs have disabled millions of computer systems and rendered systems useless or in the worst cases, crippling businesses.
One of the infamous cases is the Wannacry Ransomware that demanded users to pay in bitcoin in the year 2017.
Data Breaches and Data Leaks
Most of the data breaches occur from planned cyber-attacks on an organization’s database. Whereas the data leaks are caused by human errors like fragile internal cybersecurity that results in record vulnerability.
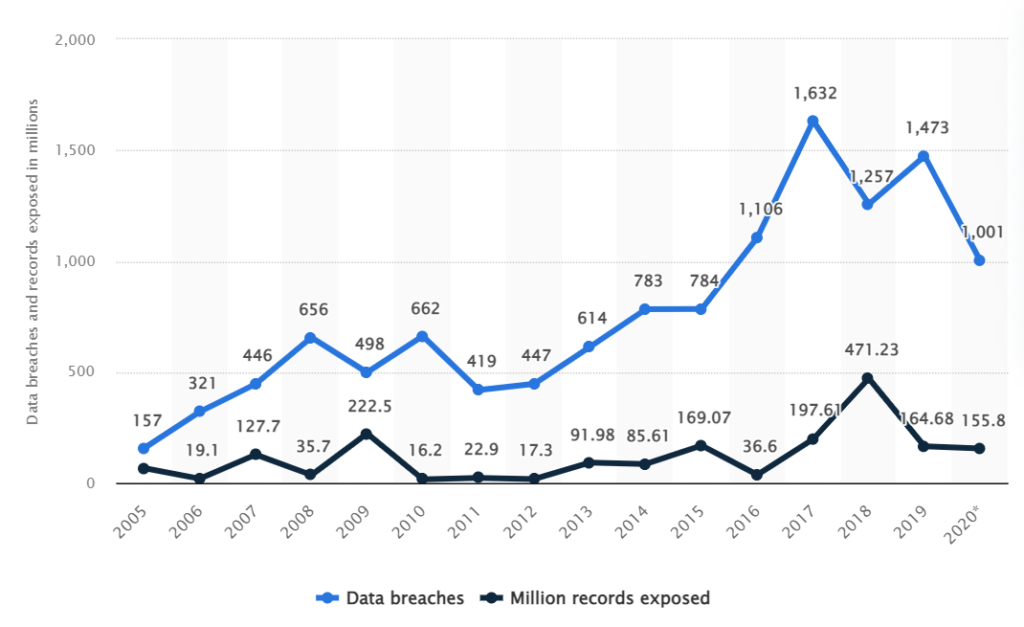
The number of data breaches has shot up in the past decade from 662 to over 1000 breaches, since 2010.
Although, the number of data leaks has not seen any significant change. This peaked in 2009 and 2018 leaking over a whopping 223 and 471 million sensitive records, respectively.
The year 2020 reported about 156 million leaked sensitive records.
Per the recent report, the two biggest factors causing the maximum financial loss in a single data breach are:
- Lack of in-house cybersecurity experts
- Cloud migration
Whereas, incidence response plan testing and business continuity management kept the potential damage from the attack in check.
Cybersecurity best practices for your startup
Now that you know the potential risks of having a business without cybersecurity, here are some of the best practices you can follow when starting out with a cybersecurity team.
1. Assign an administrator account and role-based users
Having a small employee base would have you granting administrator access to most of your employees so as to increase productivity and provide freedom to your team.
However, there’s a catch. It leaves your systems more vulnerable and makes it harder to figure out where your cybersecurity breach is occurring.
So the best practice when starting out is to ensure administrator access only to one account/member of your organization.
This member will be the individual who will manage all the confidential information of the company, customer data, employee data, and financial records.
You should also set up specific roles and responsibilities for each of your employees’ accounts.
By limiting the access to information solely on a need-to-know basis, we are minimizing the risk of data breach by a phishing attempt.
Furthermore, incidents like former employees gaining access to the system because access levels were not updated, have led to many mishaps and data breaches.
2. Strong and regularly-updated passwords
While this may come as a no-brainer, many businesses keep very generic and easy passwords to crack to maintain ease of access.
Regularly changing passwords and keeping them complex strengthens your security.
You can also use many strong password managers like Keeper or LastPass to help maintain passwords among all your systems, browsers, and apps.
3. Secure apps and software
Did you know that using older or outdated software can lead to a software breach?
Hackers and cybercriminals could use exploits from outdated software to gain unauthorized access to your systems.
Also, using outdated software versions of antivirus or antimalware can severely leave your system vulnerable.
This is because as the internet grows so does the threat. The newer viruses and hacking tools emerge. So having the latest software with an up-to-date virus database can only bolster your security.
4. Multi-factor Authentication
Multi-factor authentication is a must for cybersecurity in general, for your personal and business accounts.
By having more than one step to authenticate the user using OTP and email authentication, users can protect their accounts and data and not have a hacker impersonate them.
By installing multi-step authentications and sign-in via authentication apps, you reduce the risk of hackers logging into your company accounts.
5. Firewall
While you might think the internal firewall available in your operating system is all you need to keep the prying eyes away, this complacency often leads to serious security breaches.
It’s a good habit to do some research and find a better responsive firewall for your organization.
Your small business needs a firewall to maintain security. Here’s why-
- Setting access control with open or closed access for IP addresses
- Mitigating cloud implication with shared data centers
- Securing databases to thwart SQL injection attacks
- Virus protection to detect and block malicious network requests
- Enabling local network protection with encrypted ports
- Verifying remote connections with a VPN tool
- Setting up basic monitoring and alerts in place
What can cybersecurity do for your startup?
The cybersecurity industry has a plethora of security products and services. However, your startup doesn’t need all the bells and whistles that are costly and cumbersome to deploy and manage.
This calls for a unique solution that is tailored for your specific business needs yet affordable.
The security industry by design caters to the business needs of bigger companies. And it often overlooks the needs of early-stage well-funded startups.
This leads to a new-age solution that listens to the demands of the startup ecosystem.
What should you do as your business scales?
Many businesses stay at a very basic level of security when growing from a small startup to a medium to larger size company.
One needs to expand cybersecurity hygiene as and when companies grow. You don’t want to keep using cybersecurity practices meant for small businesses since your business is growing and is opening itself up to unseen and unknown threats.
A quick look at the important steps to secure your startup:
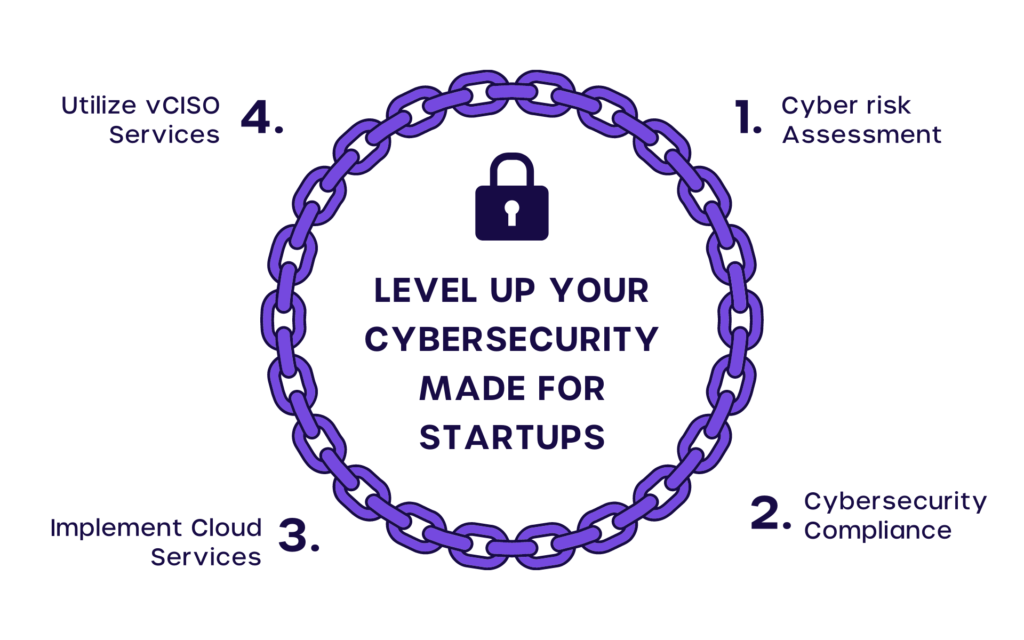
- Cyber Risk Assessment
First things first, understand that bigger companies will have much more dangerous threats. In order to know where your business stands, you need to do a Cyber Risk Assessment. Based on the results you will know where to improve your cybersecurity teams. - Cybersecurity Compliance
After completing your Cyber Risk Assessment, you will need to implement cyber security controls. And be compliant with the necessary regulatory bodies that require updating cybersecurity protocols. - Implement Cloud Services
To bolster security, you can utilize the services of a cloud computing provider to ensure all your data protection on the cloud and is not onsite and physically accessible.
Do make sure that the provider is using the best practices. And it is up to date as mishaps can occur on the cloud as well. - Utilize vCISO Services
Using Virtual CISO services, you can upgrade your cybersecurity to more professional levels in your organization. This ensures better security and protection.
What can Cyvatar’s cybersecurity as a service do for your startup?
Cyvatar was built on an idea and mission to make cybersecurity effortless, meaning it is accessible and achievable for all. We believe that cybersecurity should be accessible and affordable to every startup and SMB, no matter the size, budget, age, or industry of the company.
We take on the heavy lifting (solution identification, implementation, configuration, remediation). So you can focus on growing your business, rest assured your cybersecurity prevention strategy is working around the clock.
On top of that, we always believe that you should not worry about the security and compliance overhead for your organization. This is where Managed Security Services come into the picture. Compliance is a byproduct of a strong security strategy.
As a leading evolved Managed Security Service Provider (MSSP), Cyvatar provides fully managed security solutions with remediation to startups and other SMBs.
Check our competitive pricing or start for FREE for a risk-free one month.
