Proactive VS Reactive security – Not an ambulance-chasing approach

Proactive VS Reactive security – Not an ambulance-chasing approach
Cyvatar | 02/24/2022Proactive VS Reactive cybersecurity
In today’s modern age of technology, it is paramount that businesses have the latest protective measures in place for all their assets. As most business practices are now automated and run digitally, cybersecurity is one of the most important measures to take. Neglect of cybersecurity can lead to vulnerability online and exposure to critical information.
Now there are two ways of setting up how your cybersecurity works, they are proactive cybersecurity and reactive cybersecurity.
Which one should you go after? Proactive Cybersecurity or Reactive Cybersecurity? Well, the best decision is always a well-informed decision!
What is reactive security?
The standard method of cybersecurity. Whenever there is an attack, a direct denial of service, or a breach of data, your cybersecurity team mobilizes and repels the attacker.
Once that is done, damage control is initiated, assessment begins and the clean process is initialized.
While there isn’t anything particularly wrong with having reactive cybersecurity, it’s always better to have security that’s constantly updated and regularly maintained, which is something proactive cybersecurity provides.
What is proactive security?
Proactive cybersecurity involves taking steps and precautions before an attack.
A cybersecurity team with a mindset to prevent a threat than to react to one is always better to have. After all, the phrase ‘prevention better than cure” holds true, even in cybersecurity.
Steps like ensuring employees have good cyber hygiene, research, and planning for potential risks always benefit your company.
Even stress tests and penetration tests conducted by hiring cybersecurity experts to check your defenses are good practices to be up to date.
| GET IN TOUCH WITH CYVATAR EXPERTS TO GET THE PENTEST DONE. TAKE THE PROACTIVE PATH |
Essentially, understanding that your team is constantly learning and evolving to encounter unknown threats will always keep your security a step ahead of potential threats.
What is the relationship between proactive and reactive approaches to security in cyberspace?
The proactive security approach helps with preparation against cyberattacks in advance whereas the reactive security approach deals with mitigating the damage caused by cybersecurity threats and fixing the vulnerabilities.
Kinds of Cybersecurity Threats
Hackers can breach and use your data in many different ways, disable your services and cause inconvenience to your and your consumers.
This infographic will show you the latest ways hackers can cause problems for your business with faulty cybersecurity.
What is the advantage of a more reactive cyber defense?
A more reactive cyber defense helps in controlling the damage and preventing further loss due to new vulnerabilities.
An example of a reactive approach would be a signature-based antivirus system that scans and keeps track of known virus signatures to keep them from the network.
Now you understand that the reactive approach is only used when something happens and to clean up the mess, henceforth. Let’s learn about the benefits of proactive cybersecurity.
Benefits of proactive cybersecurity
- Faster Reaction Times
With a proactive cybersecurity team, you aren’t always being forced to react to imminent threats (which can be very exhausting and stressful to your team).
By being proactive, your teams aren’t unprepared and won’t have to put out fires and handle crises one after another.
Being proactive ensures added vigilance and having a plan in place for any and every threat that might try to threaten your business.
This preparedness also ensures lesser stress and panic to your teams, which greatly benefits their efficiency.
- Realtime Breach Prevention
When committing to the proactive model of cybersecurity, you greatly reduce the time taken from a breach occurrence to reacting and combating the attackers/ closing the breach.
The combination of threat prevention and reactive mobilization when a breach occurs is greatly effective in minimizing damage, identifying the threat, and securing data.
By having a team dedicated to constantly monitoring and probing your defenses, you ensure that breaches don’t occur in the first place as opposed to quickly reacting to a threat.
- Have A Level Playing Field
Criminals and hackers are always thinking of innovative ways to circumvent your defenses and steal your data or worse shut down your services.
They also communicate with each other and develop sneakier and undetectable malware and other tools to infect your systems.
With hackers and crooks always thinking up new ways to attack, it only makes sense that your defenses are always constantly updated as well.
Your cybersecurity with a proactive approach can learn about these new methods and think of better defensive strategies to keep you and your business safe.
By adding security measures like threat intelligence to your security stack, you will always be able to catch up to the criminals and minimize your threat.
- Prevent An Inside Job
While one might think that all the threats that can affect your business are external, there are many instances of a malicious insider who could potentially cause damage or steal data from within your organization and systems.
Such threats can be hiding in plain sight and can be the most dangerous of them all if not weeded out sooner.
As reactive cybersecurity deals with threats only when there’s an attack, your systems can already be compromised but will never be detected from within.
This is another reason to go for a proactive cybersecurity approach.
Malicious insiders know how to breach and secure the data of companies they are employed by.
A proactive approach to security can ensure that you sniff out such suspicious activity before it becomes a dangerous threat later on.
The stealing and selling of your company’s insider information can greatly affect your business, so it’s always best to have the latest security protocols in place and employees regularly screened by your cybersecurity teams.
The other method to ensure data isn’t breached is by giving your employees the lowest level of access to confidential information in your organization.
- Figure Out Errors Within Your Defenses
Sometimes threats can occur purely out of errors or exploits within your own safety measures, firewalls, and protective software.
Having a proactive cybersecurity team in place which constantly monitors and probes for errors can make sure threats and hackers cannot spot these vulnerabilities and use them as a backdoor into your organization and precious data!
Not only that, proactive cybersecurity can ensure that these safety measures are constantly improved and strengthened, making sure there are no sneaky ways for hackers to enter and exit your networks.
- Improve Compliance Measures
With a proactive cybersecurity measure, you have multiple defense layers in place to protect you and your consumer’s data.
Legal and governing bodies like the PCI, for example, require that your business have the highest security measures in place for the protection of critical data.
Non-compliance leads to hefty fines and charges, let alone vulnerabilities to external threats.
As a rule of thumb, proactive cybersecurity measures will most likely match the compliance guidelines of these compliance bodies and are always the best option to take, compared to reactive cybersecurity.
Real-life examples of how the proactive approach was undermined, resulting in loss of money and defamation.
Example #1: Sony PSN Hack 2011, 2014
You might be thinking, would proactive cybersecurity really be necessary for your business? Well, Sony had the same idea until 2011, when their systems were hacked due to outdated security protocols.
This hack and breach led to the leak of the private and card details of 77 million customers who use their PlayStation network services.
Moreover, the hackers created a DDOS attack (Distributed Denial of Service) that prevented users from accessing any of the digital services provided by Sony.

Furthermore, Sony had another breach regarding more cybersecurity loopholes that led to important emails and insider information leaked onto the internet including final copies of many of their motion pictures.
Sony had to finally issue a public apology for the same and had to incur around $250 million dollars in damages and rebuilding of its cybersecurity protocols.
Example #2: Yahoo, 2013/2016
Clearly the biggest cybersecurity breach in the 21st century. Yahoo initially addressed their cybersecurity breach in 2013 claiming that they had information of their users’ accounts leaked by a hacker group in the millions in 2013.
However, in 2016, Yahoo did clarify that the final number of accounts that were compromised was a whopping 3 billion in number.
While they did claim that the eventual damage was minimal to users, it did impact the company as a whole.
This is because at that time Yahoo was negotiating to be sold to telecommunication company Verizon.
Because of the compromised accounts and weak cybersecurity, it caused a lot of damage to Yahoo’s public image, forcing them to sell the company for a lesser price compared to their initial estimate.
Verizon after the purchase did make a statement that after the acquisition of Yahoo they will upgrade all their cybersecurity protocols and have the highest defensive measures.
In 2017, Yahoo was absorbed by Verizon and went by the name of Oath Inc, which was later renamed Verizon Media in 2021, and 90% of it was acquired by Apollo Global Management. What a downfall, isn’t it?
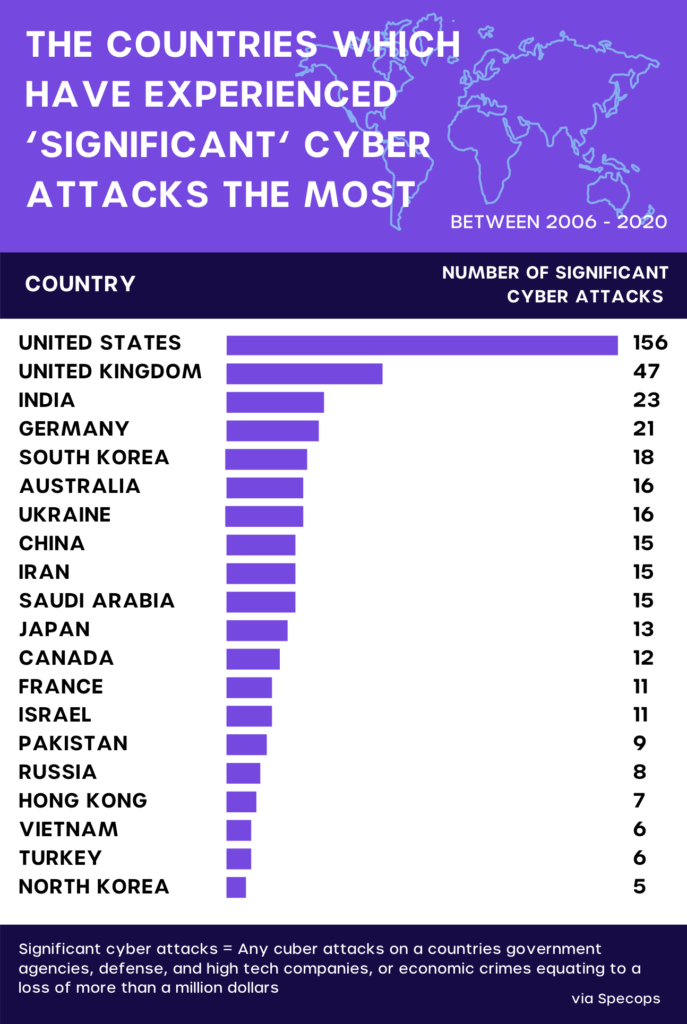
Most targeted countries for cyberattacks
Being the hub for technology and engineering, the US is the most sought-after place for students studying tech. It should come as no surprise that it is the most attacked country in the world.
Proactive security is the future
According to data collected by a 2020 report from the Cyber Risk Alliance, businesses and organizations that preferred a proactive approach felt more secure over their data and services.
This data was corroborated and backed up by the findings of the Intelligence Unit of the Economist, which states that businesses with a proactive approach have 53% fewer cyber-attacks compared to ones that didn’t.
So when are you upgrading to a proactive cybersecurity approach?
| TAKE THE PROACTIVE PATH with Cyvatar. |
