Kaseya Ransomware Attack: Top MSPs affected, its impact & lessons learnt

Kaseya Ransomware Attack: Top MSPs affected, its impact & lessons learnt
Cyvatar | 06/20/2022What is Kaseya? What is it used for?
Kaseya VSA is a platform for remote monitoring and management (RMM). It’s used by MSPs, or managed service providers, who handle IT tasks like email, phone systems, firewalls, switches, and other networking equipment.
The RMM agent is installed on client workstations and servers’ endpoints. The goal, as with most software, is to simplify IT operations for MSPs by centralizing all platform management and monitoring.
This includes asset tracking, software monitoring, and warranties on specific PCs.
What is the Kaseya Breach?
The Kaseya Breach, or the Kaseya VSA Ransomware attack, is regarded as one of the largest security breaches to occur in recent history.
In July 2021, over 50 MSPs and between 800 and 1500 businesses were affected, leading to one of the major kaseya attacks in SaaS ever. This equates to 37,000 Kaseya customers, or 0.001% of their total customer base.
An MSP services a number of companies, and if one MSP is breached, it has a domino effect on all of their clients. Kaseya VSA is a popular piece of remote network management software that is used by many managed security providers, or MSPs, which are businesses that provide IT services to other businesses.
Network management software is an ideal place to conceal a back door because these systems typically have broad access and perform numerous tasks, making them difficult to monitor.
How did the Kaseya VSA Ransomware occur?
On July 2nd, 2021, a malicious hotfix was released and pushed by Kaseya VSA servers, which propagated to Kaseya-managed servers, compromising and encrypting thousands of nodes across hundreds of different businesses.
This malicious hotfix included a ransomware payload known as Sodinokibi, which was distributed by the notorious group REvil and resulted in the encryption of the server and shared folders.
The exploit that caused it all
REvil operators used an authentication bypass in the Kaseya VSA server’s web interface to gain an authenticated session for the initial attack vector. The attackers then uploaded the payload and used SQL injection to execute a command that deployed the malicious updates.
The attackers took advantage of a zero-day vulnerability identified as CVE-2021-30116 by the Dutch Institute for Vulnerability Disclosure (DIVD). Kaseya was informed of the flaw by DIVD.
The company was validating the patch before releasing it to customers, but the flaw in the massive supply chain ransomware attack was exploited by REvil ransomware operators.
Who was responsible for the attack?
On their blog, REvil, the malicious and infamous hacker group, announced that they were the group responsible for this Kaseya VSA supply chain attack.
The attackers used vulnerable, internet-facing VSA servers commonly found in MSP networks upstream of many victims as backdoors, ensuring it was impossible for victims to detect or prevent infection as the ransomware trickled downstream.
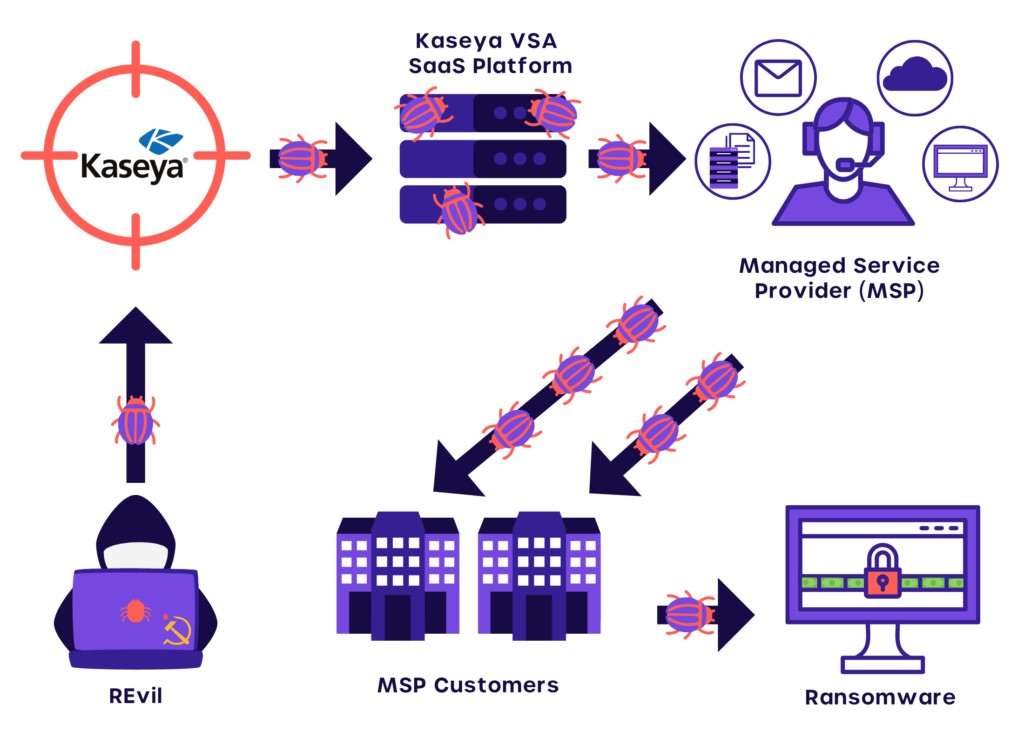
REvil used zero-day exploits to gain access to and distribute malicious software to Kaseya’s VSA SaaS platform’s customers and systems.
The ransomware gang then began encrypting everything by exploiting vulnerabilities in those systems.
Kaseya’s VSA agent (C:PROGRAM FILES (X86)KASEYAID>AGENTMON.EXE) was distributed to Kaseya’s customers (MSPs) and then distributed to the MSP customers’ systems. This agent was in charge of pulling data from Kaseya servers that were hosted in the cloud.
Kaseya’s platform signed the malware because it was already wrapped in the platform. As a result, the malware was able to bypass all security measures on these clients’ systems. To untrained eyes, it appeared to be legitimate Kaseya traffic, but it was malware installers.
The consequences of having malware signed
Malware signing is an evasion technique used by cybercriminals to circumvent security controls.
Drivers from Microsoft, for example, are digitally signed and are assumed to be trustworthy software.
When you go to install software, you may have seen warnings on your computer that it is not from a trusted publisher in the past. In this case, it is the user’s responsibility to ensure that the software is genuine.
A signed publisher executable is also looked for by endpoint protection response and other security monitoring tools. If the tool believes the software is legitimate, or if it has been configured to allow the activity by a security analyst, it will allow the software to execute and install.
REvil, after the implementation of the attack, held a ransom of around $50,000 to $5 million to each customer affected. They also offered a master key at the price of $70 million, which could be paid via bitcoin.
REvil even had a ransom note to boot:
“Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities – nobody will not cooperate with us. Its not in our interests. If you will not cooperate with our service –for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practice – time is much more valuable than money.”
How did Kaseya respond?
Kaseya disabled its Virtual System Administrator (VSA) SaaS platform to prevent malware from reaching its customers.
They then contacted the FBI and the CISA, as well as third-party vendors such as Huntress and Sophos, to assist in resolving the incident. Also, the company took on the responsibility of disseminating information to all of its customers.
The MSPs also did their proper checks in informing their customers about the attack. This also includes active threat hunting for Kaseya’s newly released indicators of compromise.
Guidelines for MSPs when under attack by ransomware
An attack from ransomware groups similar to the Kaseya VSA Ransomware can happen again. It’s for this reason that organizations need to follow a set of guidelines on how to act and prepare for a ransomware attack.
What should MSPs affected by ransomware do?
CISA advises MSP customers affected by this attack to take immediate action to implement the cybersecurity best practices listed below.
It should be noted that these actions are especially important for MSP customers who do not currently have their RMM (remote monitoring and management) service running as a result of the Kaseya attack.
- Ensure that data backups are up to date and stored in an easily accessible location that is isolated from the organization’s network
- Switch back to a manual patch management process that follows vendor remediation guidance, including the installation of new updates as soon as they become available
- Ensure that customers have fully implemented all available mitigation measures to protect against this threat
- Implement multi-factor authentication on all accounts under the organization’s control, as well as the principle of least privilege on key network resources’ admin accounts
Lessons learnt from the Kaseya attack
Many observations can be made when looking at the behavior of ransomware groups and how they operate. In this one instance, we can learn that:
- Chained exploits, such as CVE 2021-30116, will be used, which is more in the style of nation-states and the military
CVE 2021-30116 was a software vulnerability in Kaseya VSA servers that hackers exploited. This enabled them to launch a large-scale attack against several Kaseya MSP clients
- These chained attacks are extremely effective, allowing hackers to infect a large number of victims. In the case of Kaseya, they infected victims with the REvil ransomware via an automatic software update
- Previous ransomware activities will continue to fund ransomware groups. Ransomware groups are wealthier than ever before as a result of the high number of attacks, ensuring that they will continue to operate and carry out new attacks in the future
- Crypto laundering services are on the rise, which means that hackers will have a lot of money soon. Hackers can now secure their earnings on a much larger scale than in the past thanks to the use of crypto laundering, which will incentivize even more ransomware cyberattacks
How to avoid falling for ransomware attacks
Be it as an individual, a small business, or a large corporation, here are a few basic steps one can follow to ensure that they don’t fall victim to a ransomware attempt.
- Keep your OS updated
There’s a reason why companies like Microsoft and Apple are constantly providing updates for all their devices and software. These updates are essential to patching out various bugs and vulnerabilities within the operating system.
Just as Kaseya was breached via an exploit, cybercriminals can gain access to your data via an exploit or vulnerability presented in outdated software.
The more outdated your system is, the more you are under threat from cybercriminals who have devised ways to access your system. So in short, always be ahead of the game by keeping your systems updated.
- Always keep a backup
While it may seem self-evident, it is critical to keep backups of your data. The ransomware becomes a critical threat If you have a single copy of your data. The trap is ensnared by locking you out of the data.
By backing up your data on the cloud or an external hard drive you would essentially be one step ahead of the cybercriminals and prevent it from being hostage.
That said, it’s preferred that you have backups both on the cloud and remotely on a hard disk, just in case.
Also, make sure you do backups of your data regularly. An older backup will still prove to be useless if a ransomware attack has control of all your latest data.
- Use the latest protection software
Consider installing the best and latest antivirus and antimalware software on all the systems within your organization.
Modern antivirus software has the capability of scouring and monitoring your internet browsers, emails, etc and can detect malware, ransomware, and phishing attempts in real time.
Cybercriminals are only getting craftier, so it’s a good practice to have an antivirus software updated with the latest threat signatures of viruses and malware programs to prevent hacking attempts.
An updated antivirus can be your bolstered first line of defense against any cyber threat, so it’s better to have one installed.
- Bolster your cybersecurity teams
Most ransomware attacks occur mainly because of human error or a lack of oversight. So its best to educate your employees on the importance of security awareness and the consequences of being unaware.
You can also restrict access to pivotal information to only a few administrators. Doing so reduces the number of accounts that could be exploited by cybercriminals via phishing attempts and malware attacks.
Regularly have passwords updated and changed so that no cybercriminal can brute force their way into your systems and data.
Lastly, and most importantly, invest in a dedicated cybersecurity team. Having a cyber security team that is separate from your IT department will allow you to monitor data and react to threats in real time, while reducing the pressure on your IT department.
Cybersecurity teams, alongside the best in cybersecurity tools, can make your organization impenetrable to most attacks. Get in touch with Cyvatar’s cyber experts and get an outcome based on effortless cybersecurity.
