Authentication VS Authorization: Understanding the key differences

Authentication VS Authorization: Understanding the key differences
Cyvatar | 03/14/2023Imagine if an intruder was free to move around your network and could use any file or resource. An instance like this is the stuff of nightmares for every organization!
This is where authentication and authorization come into play. Both of these are robust security practices in identity and access management (IAM). Even though both of these names sound similar, they are separate steps during the login process.
To implement an IAM solution successfully, it is imperative that businesses understand what they are and the difference between the two.
What is an auth?
The process of identifying and validating users is called auth or authentication. Authenticating the identity using a password is one of the most common examples of authentication. The system matches the username with the corresponding password. If the identity is valid, then they are granted access.
There are many other authentication methods: email, single sign-on, multi-factor authentication, biometrics, and OTP via email or SMS.
Authentication is used for what purpose? The very purpose of authentication is to validate the identity of the user. It is used when the server needs to know who is accessing their information.
In authentication, the user, system, or computer has to prove their identity to the server or client.
For the question ‘What is authentication in the information security context’, the answer is simple. It verifies the identity of a user, device, or process, to allow access to resources.
What is authorization?
The process of giving permission to the user to access a specific function or resource is called authorization.
Examples of authorization are providing access to department-specific files, giving role-wise access to employees, and providing someone with administrative access to an internal application.
Ideally, authorization should follow authentication. The users should prove their identity before they are given access to sensitive resources.
How is authentication different from authorization?
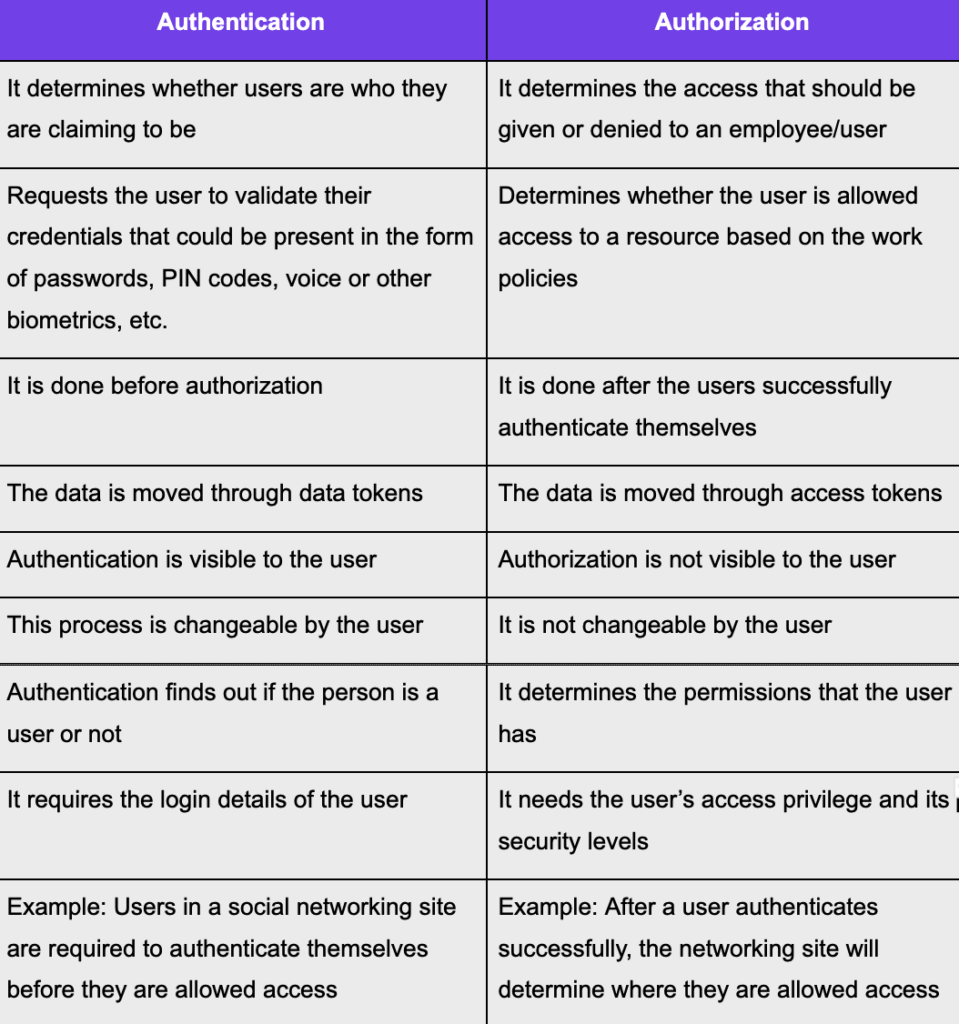
Now that we have seen the differences between authentication and authorization, let us understand the techniques used by each of them.
Authentication VS authorization: Techniques
Even though they are used interchangeably, they represent fundamentally different functions. Let us look at the different techniques in authorization and authentication.
Popular authentication techniques
We will go through the various authentication techniques that verify whether the user is the one who they claim to be.
- Password-based authentication
One of the most common methods to authenticate, passwords can be in the form of a series of numbers, letters, or special characters. Strong passwords are necessary to ensure no one gets in.
Passwords alone are not the most effective way to combat a hacking attempt. Sophisticated hackers can easily guess user credentials by going through every possible combination until they find a match.
| This is where multi-factor authentication comes into the picture. Start with the Cybersecurity Foundations plan to experience differentiated safety. |
- Certificate-based authentication
This authentication type identifies machines, users, or devices with the help of digital certificates. The certificate is an electronic document that is usually a passport or other government-issued identification card.
The certificate includes the digital identity of the user, including a public key and the digital signature of a certification authority. These certificates prove the ownership of a public key that is only issued by a competent authority.
When the users sign into a server, they provide their digital certificates. The server system verifies the authenticity of the digital signature and the certificate authority.
- Biometric authentication
It is one of the most popular authentication methods that uses unique biological identifiers of users to identify them. They can control physical access when installed on doors and gates.
They are powerful when they are a part of a multi-factor authentication (MFA) process. According to Microsoft, if you use a second factor for authentication, it can block 99.9% of all attacks.
Biometric authentication is used across the world by small businesses, enterprises, government agencies, airports, military bases, etc.
Here are the common biometric authentication methods:
- Fingerprint scanners: Matches the unique print on a person’s fingerprint. There are fingerprint scanners that can even assess the vascular patterns in fingers.
- Facial recognition: They recognize the unique facial features of an individual to provide access. When comparing faces at different angles, the results can be inconsistent.
- Voice biometric recognition: Verifies the identity of the speaker by using speech patterns. It is known for its high accuracy, high security, and low cost, and it can be done remotely, unlike every other biometric authentication method.
- Iris scanners: They project light into the eye to search for unique patterns around the pupil. They are compared with the patterns of the individual in the database.
- Token-based authentication
Here, users enter their credentials once, and they will receive a unique encrypted string of random characters. This token can be used to access protected systems. The token is proof that you have access.
- Consumer Identity and Access Management (CIAM)
CIAM manages your IT services’ external consumer identities. It enables organizations to securely capture and manage customer information. CIAM also controls customers’ access to services and applications.
56% of users have said that they will abandon an online service or account if they have a frustrating experience during the sign-in process.
It provides features such as self-service account management, consent management, preference management, customer registration, and other authentication methods.
- Single Sign-On (SSO)
By logging in to one application, the user gains access to multiple other applications. It provides a seamless experience for the user as they don’t have to remember multiple sets of credentials.
Enterprises can make this happen by identifying a central domain and then creating SSO links between resources. SSOs allow for domain-monitored user authentication, and by logging off once, you will automatically end the session for all linked applications.
Popular authorization techniques
- API Keys
An API key is a long string that’s included in the request URL or header. To utilize APIs, you need to sign up for an API key.
The API key is to identify the person performing the API call. The key for the API could be linked to a particular application you’ve registered. It is possible to get both public and private keys from APIs.
The public key is included in the request while private keys are used for server-to-server communication.
- HMAC
The Hash-based Message Authentication Code (HMAC) is a digital signature algorithm that is designed to reuse MD5 and SHA-1, the message-digest algorithm. They provide an efficient data integrity protocol mechanism.
HMAC encrypts plain text securely. They are used in the Secure Socket Layer protocol, SSL certificate, and also as a mandatory security implementation for the internet protocol.
- OAuth
The Open Access Delegation Standard is a standard that allows internet users to grant websites or applications access to information without the necessity of sharing passwords.
OAuth grants clients secure delegated access to server resources. The OAuth protocol allows an authorization server to provide access tokens to third-party clients with the resource owner’s permission.
- JWT
The JSON Web Token (JWT) is an open standard for transmitting information between parties as a JSON object. It is commonly used for authorization.
JWTs are signed with the help of a secret or a public/private key pair. After users log in, every request will require the JWT.
The JWT will allow the user to access routes, services, and other resources that the token gives access to.
- Role-based access control (RBAC)
It checks the roles of the current user to see if they can get access to the requested resource. RBAC restricts network access based on a person’s role in the organization. The roles in RBAC refer to the levels of access that employees have.
People are given access to resources based on what is necessary to get their job done. Access can be based on factors such as seniority, authority, responsibility, and competency.
When there are hundreds or thousands of employees, security is best maintained by restricting access to sensitive information.
- Security Assertion Markup Language (SAML)
Originally developed in 2001, this open standard provides both authentication and authorization.
SAML allows an identity provider to authenticate users, then pass an authentication token to another application that is known as the service provider. SAML authorization means that the user has been authorized to access a specific resource.
- Attribute-based access control (ABAC)
It grants permission to users on a granular level, that is, based on a set of specific attributes. The user attributes include the user’s name, role, organization, ID, and clearance.
Environmental attributes such as data location, time of access, and current organizational threat levels are also considered. Resource attributes such as file name, resource owner, and the level of data sensitivity are also taken into account.
ABAC is considered a more complex process than RBAC.
For example, instead of allowing managers to access employee data throughout the organization, the former is limited to viewing the data of employees under them.
Why is a strong authentication and authorization strategy important?
When you are dealing with sensitive data, authentication and authorization become extremely necessary. Without them, you are vulnerable to data breaches and access from malicious parties.
The relationship between authentication and authorization is that both of these are used in conjunction with each other when referring to security and gaining access to the system.
Since authentication confirms the identity and authorization allows access, even if one of the systems fails, it could lead to chaos.
Authentication and authorization keep your data organized and help find unauthorized activities before they become a threat.
To protect against breaches, the first step that businesses should take is to give permission only to users who have the requisite permission. By doing so, you can stop access to malicious actors.
Time to step up your cybersecurity
We now understand how important authentication and authorization are to keeping bad players at bay. To ensure complete protection of who accessed what, it’s important to have a cybersecurity service that understands the knitty gritty of cybersecurity.
Cyvatar comes with plans that are customized to various business sizes and budgets. Get in touch with cybersecurity experts to find out what your organization needs.
