What is multi-factor authentication and how to enable MFA using Cyvatar?
What is multi-factor authentication and how to enable MFA using Cyvatar?
Cyvatar | 03/03/2022Before we could dwell deep into the nitty-gritty, let’s start with the multi-factor authentication definition.
What is MFA?
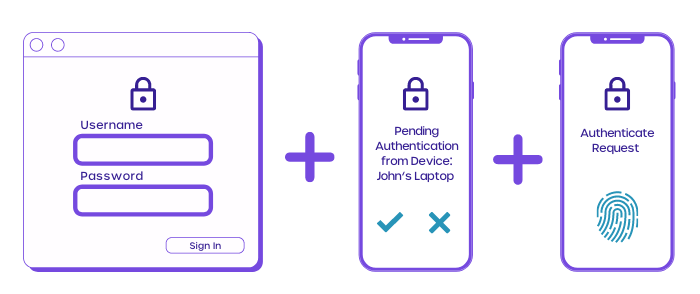
Multi-factor authentication (MFA) in simple words is a security technology that requires a user to authenticate their identity in multiple methods so as to offer bolstered security to an account.
Multi-factor authentication requests the user for two or more credentials to gain access, an example would be: A password the user knows, and biometric authentication (fingerprints, facial recognition, etc).
Its goal is to build a layered defense that makes it more difficult for an unauthorized person to gain access to a target, such as a physical location, computing device, network, or database.
If one of the factors is compromised or broken, the attacker still has one or more barriers to overcome before successfully breaking into the target.
Why do you need Multi-Factor Authentication?
The reason why multiple-factor authentication is a necessity in today’s times is that cybercriminals and hackers can easily gain access to accounts by hacking or acquiring passwords.
A single layer of authentication isn’t enough to protect your accounts anymore.
As hackers can use methods like brute-forcing or password cracking apps to gain access, the traditional authentication method of a username and password isn’t the best way to go for security.
Even though there are added precautionary measures like locking accounts after multiple login attempts, there are many methods that hackers have developed to circumvent that added protection.
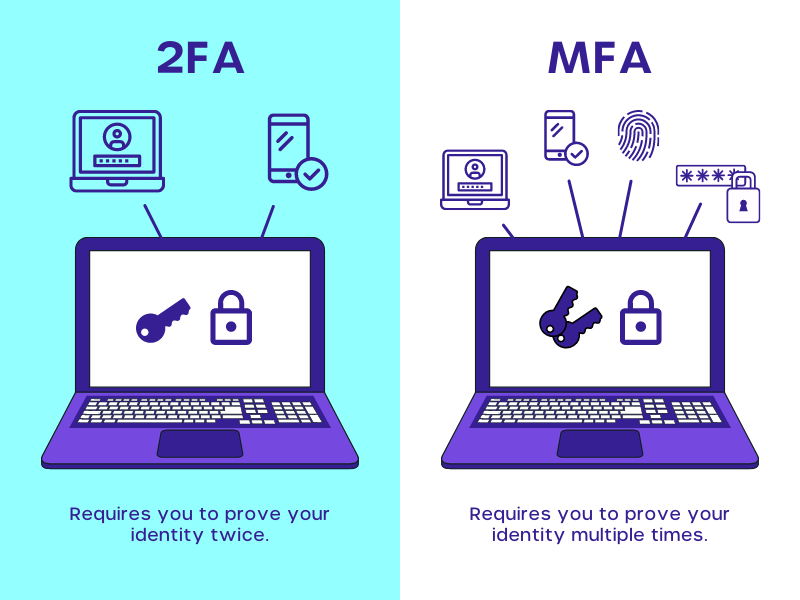
2 Factor Authentication (2FA) or Multi-Factor Authentication (MFA)?
2 Factor authentication as the name suggests provides a two-step authentication process when it comes to accessing an account.
2FA can be considered as the predecessor to MFA as it was initially created as a secure yet seamless authentication process.
An example of 2FA authentication was implemented at Automated Teller Machine cards (ATM) where users would have to first present their bank card and then had to further authenticate with a PIN.
Unfortunately, hackers have figured out ways to gain access to this data through debit/credit card skimming, rendering the authentication process less effective.
This is why one needed a more bolstered and multilayered authentication process.
How does Multi-Factor Authentication work?
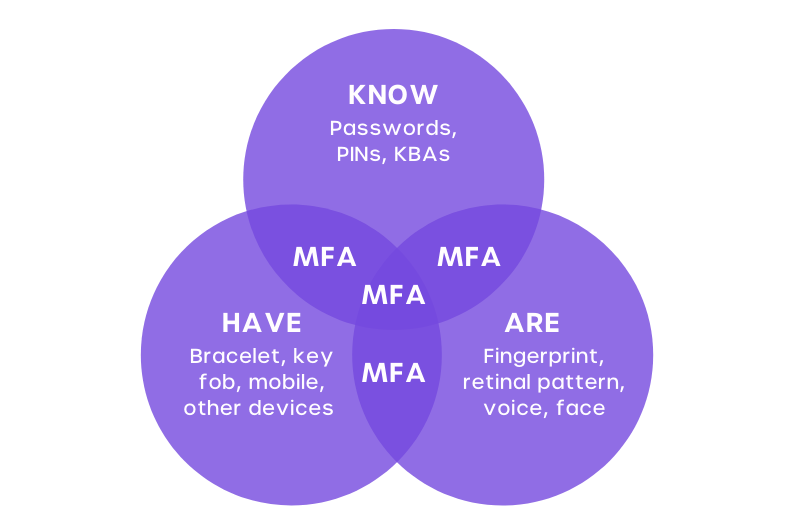
Multi-factor authentication works by requiring a minimum of two of the user’s credentials or factors. There are many multi-factor authentication methods that broadly come under 3 categories:
1. Knowledge Factor (What You Know)
The most common example of the knowledge factor is the password, but it could also take the form of a PIN or even a pass-phrase that only you know.
Some organizations tend to implement knowledge-based authentication, such as security questions (e.g., “What is your first dog’s name?”), however, the hackers frequently discover basic personal information via research, phishing, and social engineering, making it less than ideal as an authentication method on its own.
Passwords, four-digit personal identification numbers (PINs), and one-time passwords are examples of knowledge factor technologies (OTPs). The following are examples of typical user scenarios:
- Swiping a debit card and entering a PIN at the grocery store.
- Downloading a VPN client with a valid digital certificate and signing in to the VPN client to gain network access.
2. Possession Factor (What You Have)
Because a hacker or a cybercriminal is much less likely to have stolen your password and then stolen something physical from you, the possession factor confirms that you are in possession of a specific item.
Mobile phones, physical tokens, key fobs, and smartcards are all included in this category of credentials.
Depending on the item, there are a few ways for this authentication to work, but some common methods include:
- Confirming via a mobile app or pop-up notifications from your smartphone
- Typing a unique code generated by a physical token like a USB drive or wireless tag
- Inserting an embedded card (eg, at an ATM or a SIM to your mobile)
3. Inheritance Factor (What You Are)
A fingerprint scan on your mobile phone most commonly validates the Inheritance factor. That said, validation also includes anything that would be a unique identifier of a physical person, such as a retinal scan, voice, facial recognition, or any other type of biometrics.
Currently, here are some of the biometrics one can analyze by inheritance technologies:
- Retina or iris scan
- Fingerprint scan
- Voice authentication
- Hand geometry
- Digital signature scanners
- Facial recognition
- Earlobe geometry
There are numerous options available in each of these three categories, and different authentication mechanisms may be preferable for different businesses based on their specific needs and use cases.
An organization can find the best combination for them and their users by evaluating the relative strengths, costs, and benefits to both IT and users.
Why is Multi-Factor Authentication important?
Multi-Factor Authentication was created for the sole purpose of making it harder for hackers and imitators to gain access to accounts and data of an organization/individual.
By the usage of different forms of credentials, MFA security tightens login security and is a more personalized security measure for the organization/individual.
The downside to Multi-factor authentication, however, is…. Human error.
The reason behind this is that users may not always remember multiple sets of credentials.
With users having to keep track of answers to personal questions, Personal ID tokens, and passwords, MFA can prove to be a hurdle.
Nevertheless, the benefits of MFA outweigh the downsides.
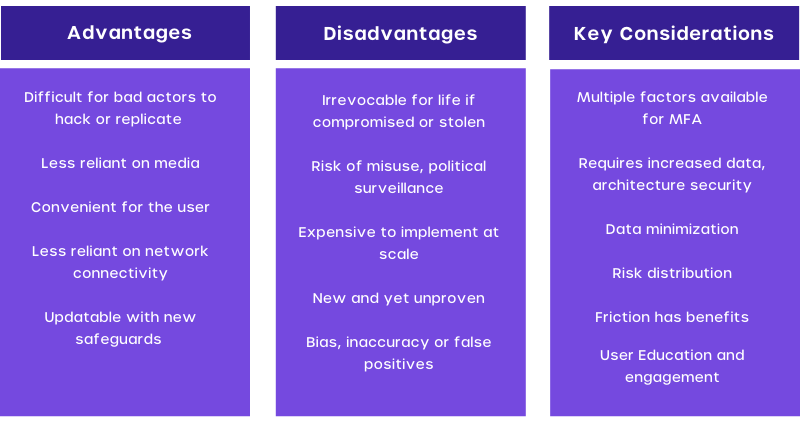
Let’s compare the pros and cons:
| Pros of MFA | Cons of MFA |
|---|---|
| * Adds security layers at the hardware, software, and personal ID levels * Can use OTPs sent to phones that are generated at random in real-time and are difficult for hackers to crack * Can reduce security breaches by up to 99.9% when compared to passwords alone; users can easily set it up * Allows businesses to restrict access based on time of day or location; and has scalable costs, as there are expensive and highly sophisticated MFA tools as well as less expensive ones for small businesses | * A phone is required to obtain a text message code * Hardware tokens can be misplaced or stolen * Phones can be misplaced or stolen * MFA algorithms’ biometric data for personal IDs, such as thumbprints, are not always accurate and can result in false positives or negatives * If there is a network or internet outage, MFA verification may fail; and MFA techniques must be constantly upgraded to protect against criminals who work tirelessly to break them |
How can Multi-Factor Authentication be simplified?
Multi-factor authentication adds a lot of security measures to an account but can be quite a hindrance to users who have to remember multiple passwords and PINS etc.
To circumvent this, there are three multi-factor authentication methods:
1. Push Authentication
It is an automated mobile device authentication technique in which the security system sends a third, one-time identification code to the user’s mobile device.
Users who want to access a secured system, for eg, enter their user ID and password, and the security system generates a third, one-time identification code for their mobile device.
To gain access, users enter that code into the system. Push authentication simplifies MFA by providing users with a third code that they don’t have to remember.
2. Single Sign-On (SSO)
It is a one-stop authentication method that users can use to maintain a single account that automatically logs them into multiple applications or websites via a single ID and password.
Single Sign-On works by determining the user’s identity and then sharing it with each application or system that requires it.
3. Adaptive Multi-Factor Authentication
It involves the application of knowledge, business rules, or policies to user-specific factors such as device or location
For example, a corporate Virtual Proxy Network knows that it is acceptable for a user to sign on from home because it can determine the risk of misuse or compromise based on the user’s location.
An employee who connects to the VPN from a coffee shop, on the other hand, will trigger the system and be prompted to enter MFA credentials.
How to enable Multi-Factor Authentication via Cyvatar.ai
Cyvatar provides MFA services as a part of its 3 different subscription packages. The Multi-Factor Authentication management by Cyvatar:
- Provides multi-layered security protection
- Reduces the risk of unauthorized access
- Gives you the ability to restrict user access based on location
- Streamlines access based on user profile
- Provides configuration and management of MFA
Hop on to our risk-free 30 days trial to feel the unique security with Cyvatar’s MFA.
