What is vishing? Tips & examples to spot and avoid voice scams

What is vishing? Tips & examples to spot and avoid voice scams
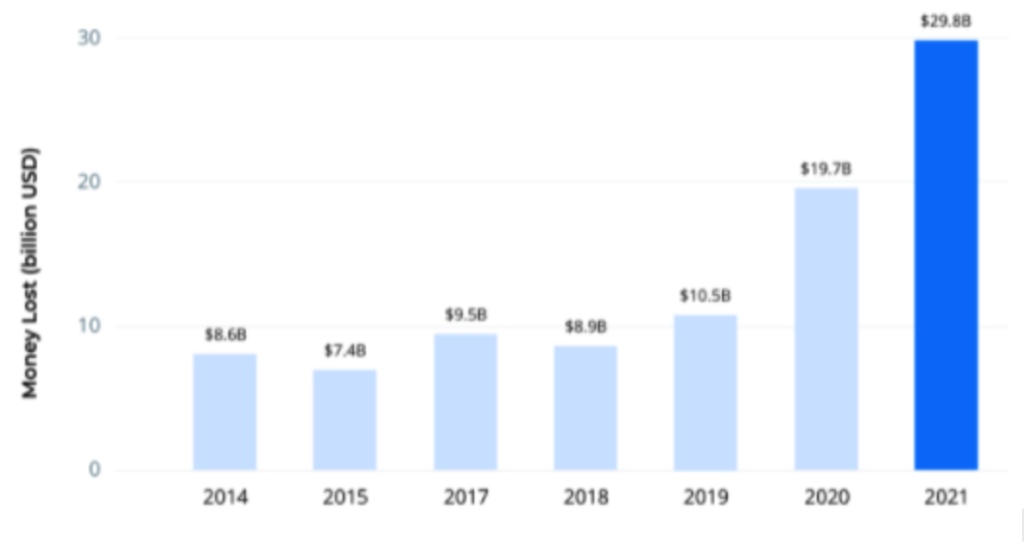
Cyvatar | 04/29/2022Nearly 1 in 3 Americans have fallen victims to a phone scam. According to a report from Truecaller, 59.4 million Americans have lost a total of $29.8 billion to phone scams in the last year.
Cybercriminals are getting sophisticated, they equip themselves with the latest technologies and leverage social engineering tactics to swindle their unsuspecting victims into becoming a vishing victim.
What is vishing?
Short for voice phishing, a person disguises themselves on the telephone to steal sensitive information from victims. Cybercriminals use clever social engineering tactics to persuade the victims to give up their private information.
In most vishing scams, callers will pretend to be calling from the victim’s bank, tax department, government office, and so on.
The victim will be led to believe that they are doing the right thing since the language used by the cybercriminal is convincing and laced with threats that make the former feel as if they have no option but to give up the information.
Cybercriminals attack both individuals and organizations. They use the CEO’s identity and will call an employee to persuade them to transfer funds to a particular account, while making them believe that the transfer was made at the behest of the CEO.
Cisco’s 2021 Cybersecurity Threat Trends report says that phishing accounts for more than 90% of data breaches.
Vishing, smishing, and pharming are considered the most prevalent threats. Vishing scams are becoming mainstream, and they are incredibly easy to orchestrate. This is what makes vishing attacks a terrifying affair.
What is the objective of a vishing attack?
The main objective of a vishing attack is to gain access to sensitive financial information or the personal data of an individual. Vishing attacks are easier to commit than in-person attacks. Why?
Because in a face-to-face attack, the chances of verifying the authenticity of the other person increase. You can ask the person to show their ID cards, verification badges, or any access cards.
That’s exactly why vishing attacks are easier to perform, as the scammer can use a lot of methods to con the victim.
What does a vishing scam look like?
You can identify a vishing scam based on the context of the call. The communication can be assumed to be like this:
- You get a phone call. The number you see on the screen is either from your area code or represents a business that you are familiar with.
- You assume you know where the call is coming from and attend the call.
- The voice on the other end tells you that your bank account has been hacked or you filed your taxes incorrectly.
- They ask for personal or financial information so that they can verify your account.
- They want you to immediately follow the steps they outline so that your bank account can be secured or you can be let off without a jail term for lying on your taxes.
Most of us know someone who has been duped in this way. On average, Americans receive almost 31 spam calls per user per month. These are worrying numbers as the livelihoods of people are at stake here.
What are the common vishing techniques?
Let us look at some of the most common vishing techniques so that one can identify a vishing attack if they receive one.
1. Voice over Internet Protocol (VoIP)
VoIP technology makes the creation of fake numbers easy. Cybercriminals can create fake numbers that are difficult to track.
They are made to appear local, or even come with a 1-800 prefix. Sophisticated cybercriminals will also create their VoIP numbers in such a way that they look as if they are coming from a legitimate government account or their bank.
2. Caller ID Spoofing
Just like VoIP-enabled vishing, cybercriminals use fake phone numbers by spoofing the caller ID. They pretend to be a caller from the government, the IRS, the police department, or a fraud-investigating agency.
Since the modus operandi of these criminals usually entails making them look as if they are a figure of authority so that the victims can share their private information, spoofing caller ID to make the number look legitimate is pivotal.
3. Wardialing
In this, hundreds or thousands of automated calls are made to hundreds or thousands of numbers. Their intended victim may get a recording threatening them to call back the scammers.
The vishers will say that they are calling on behalf of the tax department or the victim’s bank. Wardialing usually focuses on a specific area code.
4. Dumpster Diving
The attackers collect the phone numbers by digging into the dumpsters behind banks and other organizations. Using information gathered from this exercise, they deliver a targeted vishing attack against the victim.
| Cyvatar detects and fixes vulnerabilities before attacks reach networks. See what Cyvatar’s Cyber Prevention & Cloud plan can do for your business. |
Examples of vishing attack
These are some of the ways in which vishing attacks take place. Being aware of this helps people from falling prey to such scams.
1. IRS Tax Scam
The victim will receive a pre-recorded message. They will be told that there is something wrong with your tax return, and if they don’t call back immediately, an arrest warrant will be issued.
IRS doesn’t:
- Call directly asking you to pay bills immediately. Instead, they would send you the bills through the email
- Demand that you pay the taxes that you owe without the freedom to question the tax amount
- Threaten to bring in immigrant officers, local cops, or any law enforcement authorities to arrest you for non-payment
- Threaten to cancel your driving license, business license, or immigration status. IRS cannot do it
2. Unsolicited offers
The victims get an offer to invest in an ‘exciting’ project or obtain a loan at a lower interest rate.
Since these kinds of transactions require financial information, the vishers convince the victim to give up personal financial information.
If the visher convinces the victim that it is a genuine offer, then the latter wouldn’t hesitate to share information.
3. Medicare/Social Security Scam
Unfortunately, most vishing victims are the elderly. Their operation involves using the victim’s condition to con them into giving up their personal data. In return for their cooperation, they get a promise for a discount or a refund.
4. Compromised bank account
Since the vishers are hoping to gain access to the bank accounts of their victims, the smartest way to con them would be to pose as an official from the bank.
By using the bank’s routing number (easily found online) and the victim’s account number, the attacker can transfer funds to their account. All they need is the credit card number, expiry date, and security code to make purchases online or over the phone.
How do you spot a Vishing Scam?
It is not easy to recognize a vishing scam as the victims are not made to feel as if they are being conned. But if you are aware about how to spot a vishing scam, you might be able to save yourself.
Here are a few tips on spotting vishers:
- They claim to represent the government/IRS/bank
No federal agency will contact you directly unless you’ve requested contact and will never ask you for your financial information.
In fact, anyone who calls you asking for your personal or financial information is a scammer.
- They ask you to confirm your information
The caller will pretend that they are doing an audit or that they have to verify your information for ‘official’ purposes.
They will ask you to confirm your date of birth, name, address, bank account information, social security number, and other personal-identifying information(PII).
To make themselves look legit, they will already possess some of this information and share it with you. Their objective is to get the rest of the information.
- They tap into your fears
Vishers use threats of an impending arrest if you do not comply with their demands. They will say that you have not paid your taxes or use fear to persuade you to do something.
If you ever get a call like this, keep yourself calm and hang up to investigate if the call was from a genuine source. It is most likely that it was a scam.
Let us look at commonly used vishing messages:
- Your bank account has been hacked
- A charity is requesting funds for Covid-19 support
- Your laptop has been compromised
- You have won a free vacation to the Bahamas
- You are eligible for a free trial (for a product that you didn’t even request)
- Your loved one was in an accident
- Your friend or family member needs money immediately to get out of a dangerous situation
How to Prevent Vishing?
While it is important that everyone knows how to spot a vishing attack, it is even more pertinent that one takes the steps to prevent it from happening.
Let us look at a few ways you can prevent vishing.
1. Sign up with the National Do Not Call Registry
It is free to add your personal or home number to this registry. By doing so, you will stop getting unsolicited calls from telemarketers.
2. Don’t respond to prompts
When you receive an automated message that asks you to press buttons on your phone, do not do it.
Cybercriminals will use this technique to identify people who are susceptible to such targeting. They may even record your voice and use it to navigate voice-automated phone menus.
3. Verify their identity
Do not hesitate to ask the caller to identify themselves. Alternatively, you can also use the internet to search for the caller, the company they represent and ask them for any other information that can be used to verify their identity.
4. Think twice before you offer any information
If you receive a call from an unknown person, do not offer them any personal or confidential information.
Even information as simple as the name of your high school could be a security question that your bank asks to verify your identity. Scammers will try to sound nice to get access to your information, do not give in.
5. Hang up if you have a suspicion
If you think that the caller might not be from a trustworthy source, then hang up immediately. You can also check for the correct number of the organization they claimed to be from and cross-verify it.
6. Look for social engineering language
Listen to the caller carefully and analyze whether they are using social engineering techniques such as using urgency, punishment, or fear to make you give up critical information.
7. Don’t respond to unsolicited calls/emails
Another simple but highly effective step to not becoming a phishing victim is to avoid responding to any unsolicited emails, outreach messages, or marketing communications.
8. Ask questions
If the caller says that they are giving you a free prize, ask them for proof by asking for information to verify the same.
Make sure you ratify the identity of the caller before you proceed to give even the tiniest of information.
9. Educate yourself and others
Falling prey to a vishing scam can be devastating mentally and will even result in loss of resources, usually money. Educate yourself, your loved ones, and colleagues as to how they can stay safe from vishing scams.
How to recover from a vishing attack?
If you have shared your personal or financial information recently, and you suspect that it might be a vishing call, then inform your financial institution or the government agencies.
There are multiple agencies, such as the Federal Trade Commission (FTC), Better Business Bureau (BBB), and the Internet Crime Complaint Center (IC3) that are working against vishing scammers.
Here is what you can do after a vishing attack:
1. Report the calls
If the vishing attacks have happened in an organization, then create a procedure where employees are asked to report the calls. The report should include the following information:
- Phone number details
- Details of the phone conversation
- What was the information that they tried to get from the victim?
- Did the customer/employee share the information?
- Where did they make the call to?
- Who was the victim’s telecom carrier?
2. Educate the customers
Create a plan where your call center staff educate the customers about the plan of action they could follow when they receive such calls.
Let the customers know that the bank will never call, text, or email, asking them to provide their debit or credit card information.
If they receive such calls, they should immediately hang up. Remind them that one can easily spoof caller IDs.
3. Inform the authorities
Ask the customers to identify the area codes that they were requested to call. Inform the local FBI authorities or report it online so that they will handle it.
FBI authorities can get the phone line shut down immediately, thereby preventing someone else from being defrauded.
You can also report the vishing calls to the Federal Trade Commission online.
Prevention is better than recovery
Why bother recovering when you can prevent vishing attacks in the first place? Cyvatar was built on the concept of preventing attacks before they even hurt you.
The best way to prevent vishing attacks from succeeding is to avoid sharing sensitive information over the phone. However, with Cyvatar’s end-to-end prevention, you can stop the vishing attacks even before they happen.
Cyvatar protects your endpoints, preventing any data exfiltration, ensuring the phone numbers of clients and employees remain safe within each endpoint of your network. This helps prevent the attackers from getting the phone numbers needed to launch the vishing attack.
Should things go south, Cyvatar and Cysurance’s cybersecurity guarantee has your back and covers up to $100,000 in breach-related costs.
