What is the NIST cybersecurity framework (CSF)?

What is the NIST cybersecurity framework (CSF)?
Cyvatar | 11/30/2021Short answer (TL;DR)
NIST (National Institute of Standards and Technology) cybersecurity framework is a set of guidelines for private companies (and mandatory for government organizations) to follow to better equip themselves in identifying, detecting, and responding to ever-challenging cybersecurity threats. The guidelines also help with preventing and recovering from any cyber-attacks.
Long answer (All the details)
Companies run on their own set of rules to tackle cybersecurity threats. This brings in a situation where there is a wide gap of standards as to how cyber threats can be handled.
Various companies are using technologies, rules, languages to tackle the menace of cyberattacks such as data piracy, ransomware, hacking, etc in different ways.
This difference in the standard of implementation of cyber security services across companies creates difficulty in having a unified strategy to tackle cyber threats.
Let’s take an example. There was a malware attack in your organization and you want to discuss it with your colleague in some other organization, either seeking help in mitigating the attack or making your colleague aware and alert of the same kind of attack in the future. Now, If the organizations have NIST CSF in place, they would know what to do with the information shared and hence help each other out. Otherwise, this sharing of information wouldn’t be of much help.
This makes the implementation of the NIST cybersecurity framework more important. With a unified strategy in place, companies across the states could share information and collectively reduce the risk of cyberattacks.
NIST cybersecurity framework by Obama Administration
Seeing the common cyber threats that companies were facing, the Obama administration introduced the cybersecurity guidelines under the executive order. Later these guidelines were made mandatory for the federal agencies under the executive order signed by the previous president, Donald Trump.
For private sector businesses that generally don’t bid on government contracts, it is voluntary to comply with the NIST standards. However, given the implicit benefits that come with implementing the framework, it only makes sense to go with it. Moreover, adopting the guidelines shows that you are committed to data protection and developing strong security policies.
Read through the post and you will learn how the CISOs can simplify the implementation of NIST CSF for their organization.
Understanding the NIST cybersecurity framework
The framework core
It defines the activities you need to do to achieve certain cybersecurity results. This is divided into four different elements
Functions
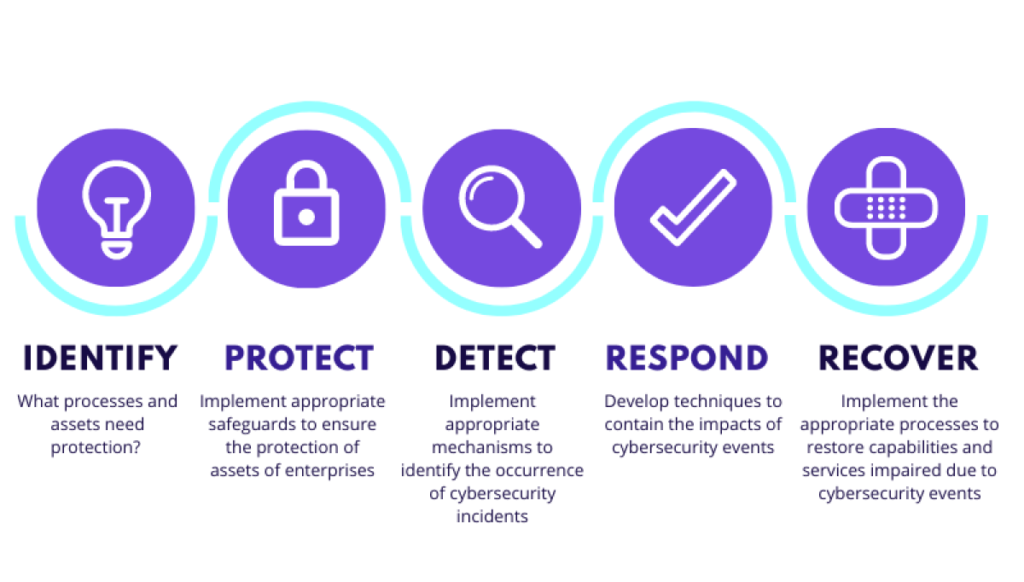
The functions are the basic core tasks to be performed in this framework. These are five core functions:
1. Identify
This lays down the foundation for an effective cybersecurity program. This assists the organization in building an overview to manage the cybersecurity risks to people, assets, and data.
The essential activities in this function can easily be summarized as:
* Define the role of business in supply chain
* Recognize the assets such as physical and software to establish the basis of an asset management program
* Understand the legal and regulatory requirements regarding the cybersecurity potential of the organization
* Recognize asset vulnerabilities
* Define the established cybersecurity policies to characterize administration program
2. Protect
This function outlines the safeguards to ensure that critical infrastructure supports the ability to contain the potential cybersecurity breach.
* Empower staff through security awareness training program
* Ensure data security protection in line with the businesses risk strategy to protect the integrity and confidentiality of information
* Protecting the organizational resources through maintenance activities
3. Detect
Detecting potential cybersecurity issues promptly is important. This function includes a set of activities to identify such issues.
* Activities to ensure anomalies are identified and their potential impact is assessed
* Continuously monitoring the cybersecurity events to measure the effectiveness of the protective measures
4. Respond
This function focuses on activities to take action in case of any cyberattack that can support the ability to contain the impact of such incidents.
* The execution of the response planning during and after the incident
* Communicating with stakeholders during and after the incident
* A thorough analysis of the event to ensure effective response and assess the impact of the attack
* Containing the incident with relevant mitigating activities
* Learning and incorporating lessons learned from the previous incidents and improvising on the current response activities
5. Recover
The recover function includes activities to renew and maintain plans and to restore any capabilities impaired by the current cybersecurity incidents. The activities of recover are very similar to that of the respond function.
* Ensuring the implementation of recovery processes for the timely restoring of the services impacted the cybersecurity incidents
* Effective internal and external communications are done during and after the recovery
* Implementing learnings based on past and current cyber incidents
Categories
For any of the five functions to happen, some categories are specific challenges or tasks that must be performed. To identify any security threats such as malware, you must install an anti-malware program, for example.
Subcategories
For each category, some sub-tasks need to be performed. For example, to install an anti-malware program, you need to remove any contradicting software.
Informative sources
These are documents that provide detailed information on how to carry out specific tasks. For instance, you must have a manual that will provide a list of software that may create hindrance with your anti-malware software. It could be another obsolete anti-malware program.
Implementation tiers
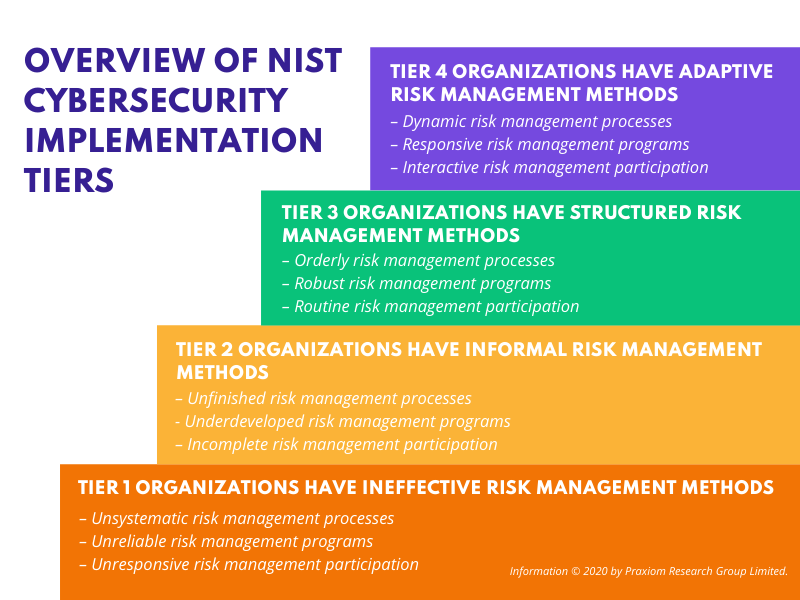
The NIST cybersecurity framework has 4 implementation tiers. This gives you an idea about what compliance your organization has. Higher the tier, the more compliant you are.
- Tier 1 organizations have for the most part ineffective risk management methods. They showcase unsystematic risk management processes, have unreliable risk management programs, and unresponsive risk management participation. They are at the lowest level of compliance and face severe security risks.
- Tier 2 organizations provide informal risk management methods. They have incomplete risk management processes, uncooked risk management programs, and incomplete risk management participation.
- Tier 3 organizations have fairly structured risk management methods. They showcase orderly risk management processes, robust risk management programs, and routine risk management participation.
- Tier 4 organizations mostly have adaptive risk management methods. They have dynamic risk management processes, responsive risk management programs, and interactive risk management participation. They are the highest level of compliance.
- Profiles
Profiles relate to both your current cybersecurity measures and your plans to be NIST cybersecurity framework compliant. These profiles help you see where you stand and fix your weaknesses.
Once the organization fixes these weaknesses, it becomes easier to move up the ladder to becoming fully compliant, eventually.
The profiles can also help CISOs see how each function, category, or subcategory can help the organization, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework.
Why should I use the NIST cybersecurity framework?
NIST frameworks are so basic for online security that anyone who uses a computer must think about the cybersecurity framework.
You should use the NIST CSF if:
- There is a grave concern about the uncertainty and vulnerability of the cyberspace
- You don’t have an accurate inventory of assets that need to be protected
- Your team has lost sense of priority and is after things that won’t have any significant impact and not after things that possess real threats
- Not all your colleagues understand the cyber risk, resulting in their ability to mitigate critical risks
- You are keen to address the risk items with the existing tools and those available in the marketplace
- You keep hearing from your board about NIST CSF compliance
How do you know if the NIST framework is for your organization?
Well, see if the answer to any of the following questions is yes.
- Do you maintain unclassified information regularly?
- Do you handle data protected by HIPAA?
- Are you planning to compete for a contract with the US federal government ever in the future?
- Do you perform any work that must be compliant with the Federal Information Security Management Act (FISMA)?
- Do you have many third-party vendors and contractors?
- Is it a possibility to enter the national security business, either as a service provider or a small business contractor?
It would be the job of your IT department to implement it; however, your employees must be trained to follow it. Business managers and CISO must take up the task to see it through to completion and make sure it’s done properly.
Now that you know that NIST CSF is for your organization, let us see what could be possible roadblocks to its implementation.
NIST cybersecurity framework implementation and roadblocks
The major roadblock in the implementation has been the huge investment.
Per a survey report on 338 IT and security professionals by Tenable Network Security, it was found that 84% of the organizations had implemented some kind of security framework.
The goal was to quantify the security framework adoption.
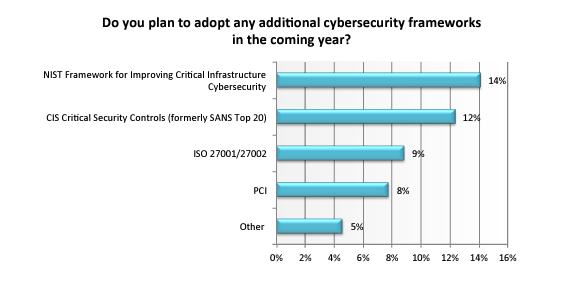
Most of the organizations that implemented the NIST framework were due to its best practices and requirements from other partners.
- 70% adopted it because they consider it to be a best practice
- 29% adopted it because the federal government contract required it
- 28% adopted it because their partner required it
Per the report, the Information Technology industry was ranked 2nd in terms of implementation.
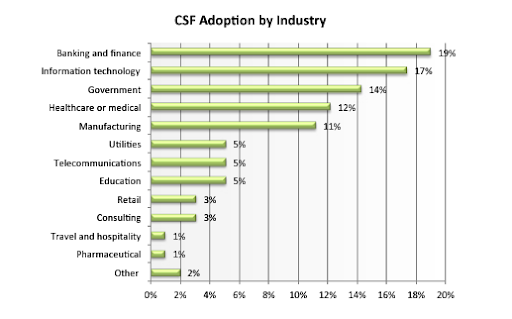
And out of those 16% organizations that didn’t have an existing cybersecurity framework, 14% insisted on a NIST framework in the future.
“Historically, CISOs have been hesitant to take full advantage of the NIST Cybersecurity Framework because of a high investment requirement and a lack of regulatory mandate,” said Ron Gula, CEO, Tenable Network Security. “This is changing as organizations begin to shift their mindset from moment-in-time compliance with frameworks like PCI DSS to continuous conformance with the NIST Cybersecurity Framework.”
More than half of the respondents admitted that the level of investment has been the major roadblock in fully conforming to the framework.
“The NIST Cybersecurity Framework is one of the most thorough and reliable cybersecurity frameworks available, but it can be challenging for CISOs to conform to these standards all the time,” said Gula.
Steps for CISOs to implement NIST cybersecurity framework
Have your NIST program align with your business goals
The best way to achieve this is to map your business objectives to NIST control families.
For example, if your organization requires maintaining the integrity of the system as the top priority then going with SI controls would better match your organization’s needs.
Focus on primary controls
Start with the subset of the control families and then make your initial control list to include vital primary controls. That way, you can implement control enhancements later when your NIST CSF program is more mature.
Implement NIST SP 800-171
Select the base framework controls using the existing profile or select the NIST SP 800-171 which includes 80% of the NIST CSF and requires 20% of the effort.
This significantly reduces the number of controls to adopt and enhances the overall security by implementing the full NIST CSF with a bit of effort.
Implement the five functions evenly
Equally, distribute your efforts across all the five functions of the NIST cybersecurity framework. This will create a balanced program.
Conclusion
Though as daunting as it may look, you cannot overlook the benefits of implementing the NIST cybersecurity framework.
Especially, in this pandemic era where WFH has become the new normal, organizations are more vulnerable to cyber attacks than ever. Implementing this framework helps mitigate the risks.
It indeed requires significant investment to implement it; however, the cost of a security breach is pretty high. Per a report by IBM, It rose to a whopping USD 4.24 Million in 2021. This calls for implementation.
Does your organization have implemented the NIST cybersecurity framework already? If not then contact our cybersecurity expert to help you secure your organization’s online presence.
