What is SOAR security orchestration and why is it important?

What is SOAR security orchestration and why is it important?
Cyvatar | 02/28/2022What is SOAR Security Orchestration?
SOAR stands for security orchestration, automation, and response. The main purpose of SOAR is to reduce the amount of strain induced on IT teams by having automated responses to a variety of events embedded in a system.
A SOAR system is dynamic in a way that it can be custom-fit to exactly what an organization needs.
This allows teams to use SOAR in different ways so as to accomplish high-level tasks and objectives, save time and reduce the amount of IT staff needed to operate.
It also benefits the current IT staff involved to work on more creative and complex projects.
In short, SOAR is a compilation of programs that strengthens an organization by collecting data and responding to security threats with minimal requirement of human assistance.
This is what makes SOAR a top to bottom threat management system.
SOAR mainly consists of three components which we will discuss below.
Components of SOAR
SOAR has three main components:
1. The SOAR Security Orchestration
The first component of SOAR, security orchestration, involves the integration of internal and external tools via the use of application programming interfaces (APIs).
This integration is usually done via built-in or custom integrations. The internal and external tools that are integrated into the system mostly pertain to:
- Firewalls
- Vulnerability scanners
- Endpoint protection products
- End-user behavior analysis programs
- Intrusion detection and prevention systems
- External threat intelligence feeds
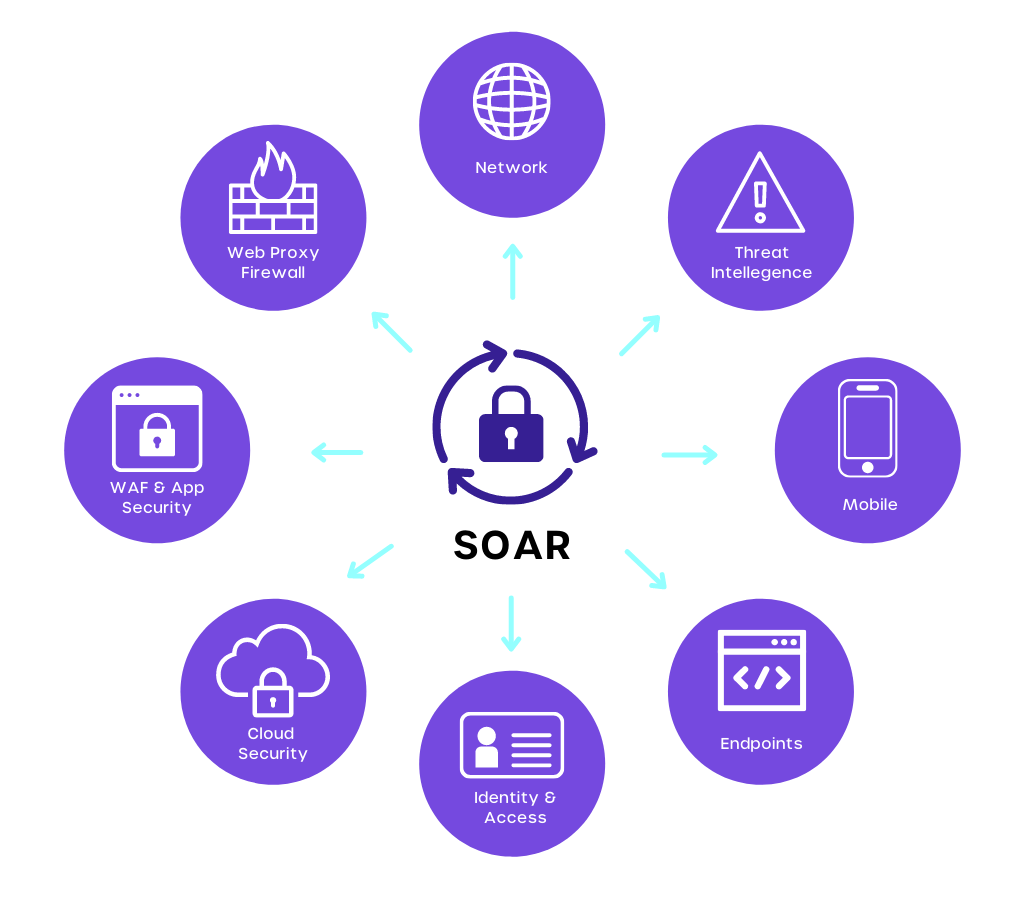
Security orchestration ensures data is constantly collected, ensuring better threat detection. The tradeoff, however, is that the system has to parse through a lot of data.
Once orchestration consolidates the data and threats, it is then handed over to automation to begin the response process.
2. The SOAR Security Automation
Based on the data and alerts provided by orchestration, the automation component begins to take action by analyzing the data and creating automated processes that will replace manual processes.
The manual processes that Security automation replaces pertain to vulnerabilities scanning, log analysis, ticket checking, and auditing – tasks that were usually performed by analysts.
All these tasks can be standardized and performed automatically by a SOAR system, reducing the amount of manpower needed to operate.
With the power of Artificial Intelligence (AI) and machine learning to help with deciphering the insights of analysts, automation can also make its own recommendations and automate responses in the future.
As a beneficial alternative, automation can also elevate threats if human intervention is required.
SOAR Security automation also makes use of playbooks. Playbooks are essential to the success of a SOAR system.
Playbooks come pre-built or customized with predefined automated actions. Also, to increase efficiency, multiple playbooks can be integrated to complete more complex tasks and actions.
How does a playbook work? A playbook is a set of predefined instructions.
If a suspicious or malicious URL is found in an employee’s email, a playbook can be used to block the email, alert the concerned employee of the potential phishing attempt and block the IP of the sender of the email, for example.
SOAR tools can even go ahead further and take advanced steps to mitigate the risks.
It can initiate investigative tasks like scanning all emails from employees to see if similar malicious content has been found and block the IP address of the potential infiltrators.
3. The SOAR Security Response
The third component of SOAR, security response, provides a single view to analysts into the monitoring, planning, and management, and reporting of actions after a security threat is detected.
The security response component also provides post-incident activities like case management, threat intelligence sharing, and reporting.
The Benefits of a SOAR System
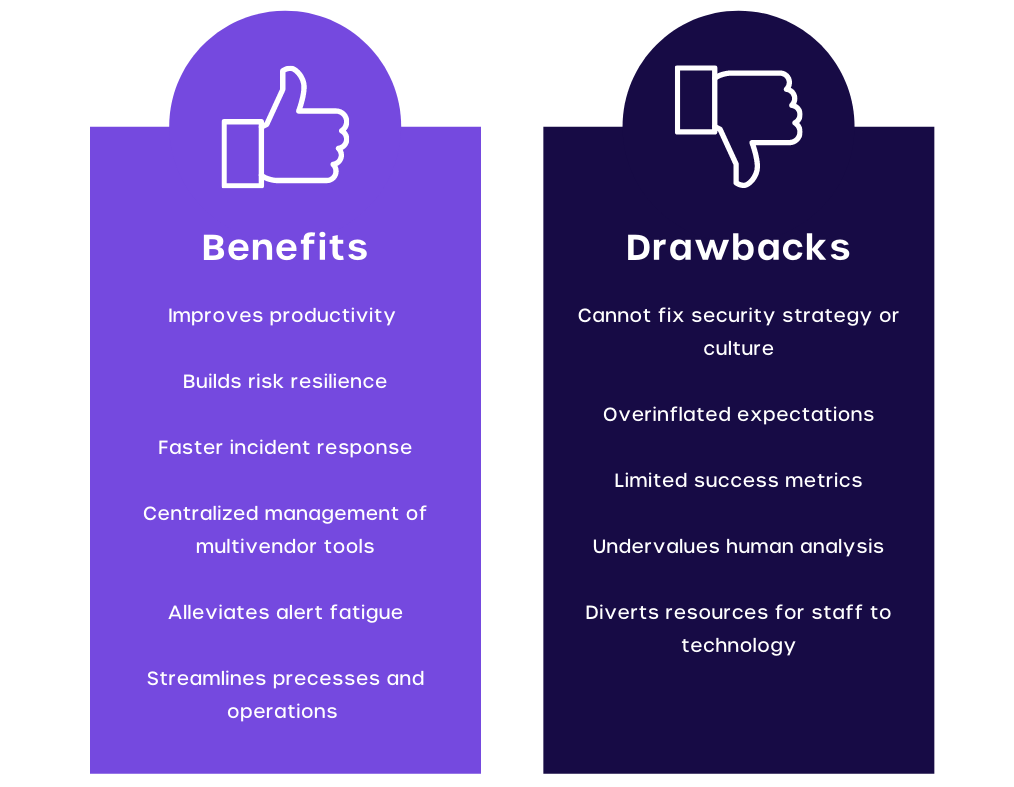
SOAR platforms are extremely beneficial to security operation teams, the major benefits are:
- Fast Reaction Times and Incident Detection
The improved data context with the combination of automation in SOAR systems ensures a lower mean time to detect and a lower mean time to respond. In an era where the volume and intensity of security threats are increasing and evolving, the ability to detect and respond to threats quickly makes SOAR an essential platform to negate threats.
- Better Threat Context
SOAR allows the integration of data from a plethora of tools and systems. This results in providing better analysis and context and up-to-date information on current threats.
- Easier Management
SOAR systems offer the benefit of consolidating many security operations into a single dashboard or interface. This allows security operation teams to better analyze and respond to threats by centralizing data and saving valuable time.
- Better Scalability
As business and operations grow so does the requirement for large security processes. Manually scaling can be quite expensive and exhausting to employees. Thankfully, SOAR’s orchestration, automation, and workflow are dynamic enough to meet any scalability requirement. This ensures lower strain on employees while providing growth and flexibility.
- Making Analysts More Productive
SOAR allows automation processes for lower-level threats. By doing so, you free up resources and time for analysts to work on bigger and more complex projects, which leads to more productivity and efficiency.
- Streamlined Operations
With the use of pre-built or custom playbooks, SOAR platforms allow streamlining of data analysis and threat management, making it easier for security operations teams to tackle multiple threats at the same time. This streamlining of operations also allows better response times when combating threats within the system.
- Lowered Costs
Investing in SOAR platforms and playbooks can be more cost-effective than hiring multiple analysts to manually perform threat analysis, detection and resolution.
Challenges of using SOAR
SOAR platforms are not a one-stop solution for handling all your business/organization security needs. It should be used as a vital part of your overall in-depth security planning.
This is because SOAR platforms are most effective when they work hand in hand with other security parties and teams.
As SOAR is more of a complementary technology instead of a replacement for security tools, it is not a replacement for human analysts. Instead, SOAR platforms can augment the skills and workflows/responsibilities of human resources for effective threat detection and response.
Besides, here are a few potential drawbacks to using a SOAR platform:
- Failure to remediate a broader security strategy
- Too many expectations combined
- Complex management and deployment of a platform
- Limited metrics provided
SOAR or SIEM?
SIEM stands for Security Information and Event Management and comes with similar functionalities.
It’s a composition of security services that helps security teams to collect and analyze security data. SIEM also allows teams to create policies and design notifications.
SIEM tools allow IT teams to:
- Utilize event logs to consolidate data from various sources.
- Allow real-time organization-wide visibility.
- Effectively add actionable intelligence to data by correlating security events from logs.
- Utilize dashboards to manage automatic event notifications.
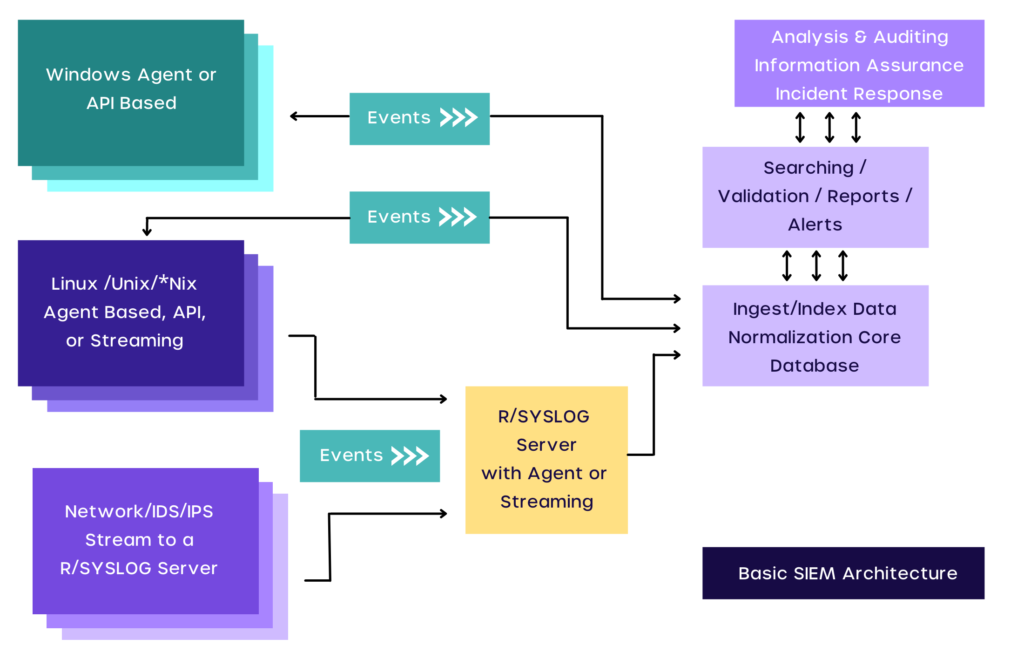
SIEM combines the management of security events and security information. This is done via real-time monitoring and system administration being provided notifications.
Both SOAR and SIEM detect security issues and provide data collection based on the nature of the threat or problem.
They both provide notifications to security personnel to help address system concerns.
However, SOAR provides much more.
| SIEM | SOAR |
|---|---|
| Alerts the analysts of some unwanted events or activity that occurred. The analysts will decide if further investigation is needed. | Alerts the analysts and automatically invokes the investigation path workflows based on the playbook, hence reducing time on resolving such alerts. |
| This calls for more human resources as it takes time to decide on the investigation of suspicious activities. | This needs minimum human intervention and hence, limited human resources are required. |
| SIEM tools are less efficient because they need regular monitoring to understand between normal and abnormal activities. | SOAR tools come with automation capabilities. In most of the situations threats are neutralized before it could create serious damage. They are inherently efficient. |
| SIEM is one of the oldest cybersecurity tools. | SOAR tools are the latest security tools that use the magic of AI and ML. |
MSOAR by Cyvatar
Cyvatar’s Managed SOAR uses a fully-managed SOAR managed detection and response plus a built-in playbook with full 24/7 monitoring.
MSOAR is a part of the Prevent Subscription Plan. MSOAR by Cyvatar helps you with:
- Threat detection scanning and monitoring
- Open ATT&CK-based alerting framework with the lowest false positive and negative rates
- Customized detection and response playbooks
- Syslog capabilities that use the ELK stack for security orchestration and automation
- Trained SOC analysts investigate likely threats and attack techniques in your environment using threat hunting playbooks
Get in touch with our cybersecurity experts to learn how MSOAR can impact your bottom line.
