Vulnerability Scanning VS Penetration Testing: Know the main differences
Vulnerability Scanning VS Penetration Testing: Know the main differences
Cyvatar | 04/14/2022In today’s day and age, cybersecurity is a must for everyone, from startups and small new businesses to large-scale enterprises. Vulnerability Scanning and Penetration Testing are two methods that companies use to make sure their security systems are safe, but there’s a common misconception that they are one and the same. We’re here to educate you on the differences.
What is Vulnerability Scanning?
Vulnerability scanning is the act of identifying possible vulnerabilities in network devices like firewalls, routers, switches, servers, and applications. It is automated and identifies possible and known network or application vulnerabilities.
Vulnerability scanners can only identify potential vulnerabilities; they do not resolve the vulnerabilities themselves.
A vulnerability assessment is just a tool that scans for potential issues. It’s up to the cybersecurity team to decide which issues to resolve first.
Vulnerability scanning tools offer assessments that can also help you identify which flaws are most critical and need to be fixed right away.
The result of an automated vulnerability scan is what you call a vulnerability assessment. Automated vulnerability scanning tools sometimes are advanced enough to suggest methods and tools to help the cybersecurity team remediate the vulnerabilities.
Issue resolution can vary from patch management to bolstering, hardened security infrastructure, or a configuration change.
As a result, these scans are not designed to detect zero-day exploits. The scope of vulnerability scanning in security testing is enterprise-wide, necessitating automated tools to manage a large number of assets.
The Process of Vulnerability Scanning and Assessment
- The Vulnerability Scanning tool starts and then finishes an automated scan of all assets in the system environment.
- It then searches and recognizes the various vulnerabilities across your network, its applications, and the infrastructure.
- The scanner then begins to categorize the vulnerabilities found based on priority and risk (e.g., low, medium, high risk).
- The IT professionals/cybersecurity team then act to resolve the vulnerabilities via patch management, configuration changes, or installing stronger security measures.
The Benefits and Limitations of a Vulnerability Scan
A vulnerability scan is an effective method to find weaknesses within your systems and infrastructure, but it certainly isn’t a one-stop solution to solve all your security problems.
Let’s take a look at the benefits and limitations of vulnerability testing software.
Benefits of vulnerability scanning
- It provides a swift, high-level analysis of possible vulnerabilities in the system.
- It’s cost-effective in comparison to penetration testing.
- Scanning frequencies can be automated. (This can be scheduled every day, week, or month).
- Scanning is quick to complete.
Limitations of vulnerability scanning
- This can lead to a lot of false positives if the scanning software isn’t up to date.
- Organizations and businesses need to manually check every vulnerability before performing another scan.
- Vulnerability scanning cannot tell you whether a vulnerability can be exploited or not.
What is Penetration Testing?
A penetration test (AKA pentesting) imitates what a hacker would do to get into a company’s network/computer system through hands-on research and exploitation.
Actual analysts, often known as ethical hackers, look to find flaws and then try to demonstrate that they can be exploited. They use methods like password cracking, buffer overflow, and SQL injection to try to get data from a network in a non-destructive way.
A pentest organization can basically identify exploits within vendors, employees, and the physical security of your organization. These tests are usually conducted by a seasoned, technical expert.
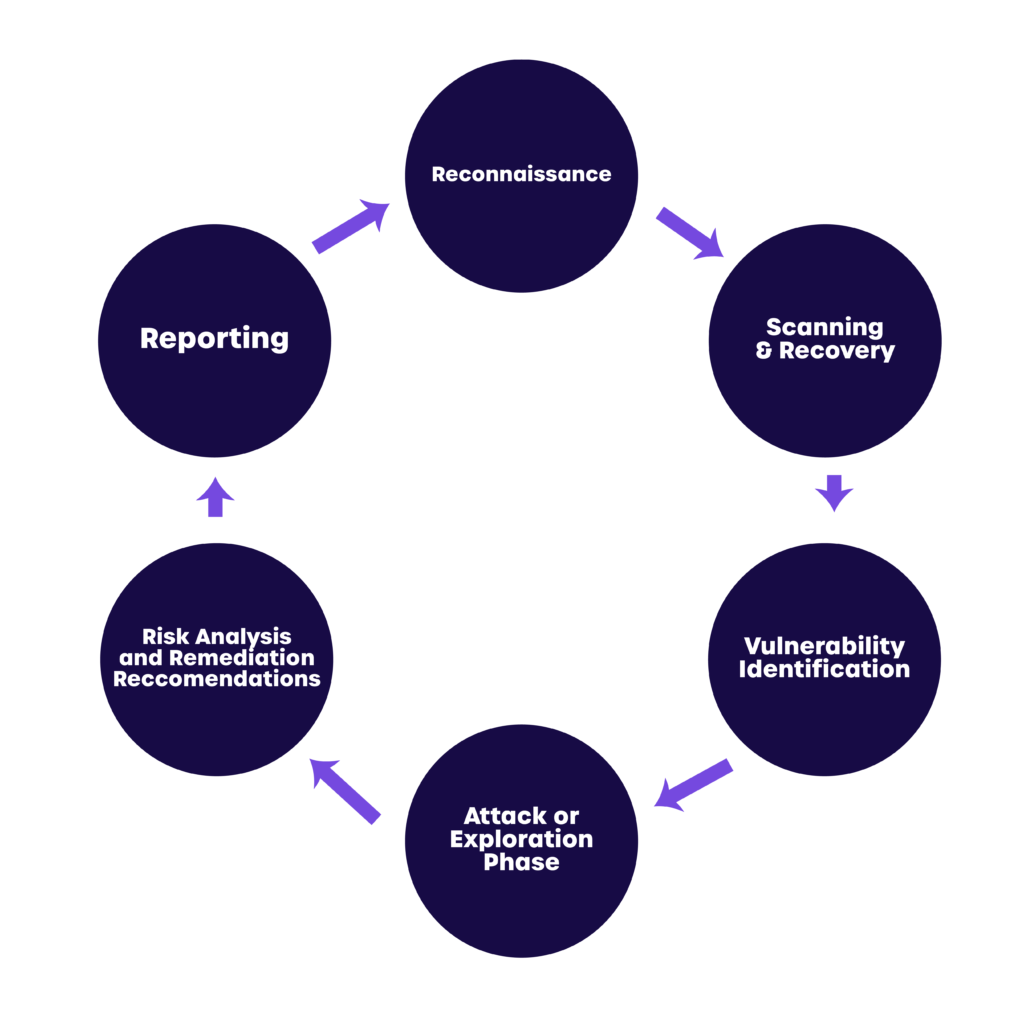
The Process of a Penetration Test
- Reconnaissance, or Open Source Intelligence Gathering
- Scanning and Discovery
- Vulnerability Identification
- Attack or Exploitation Phase
- Risk Analysis and Remediation Recommendations
- Reporting
Benefits and Limitations of Penetration Testing
Penetration testing is regarded as the best method to determine the extent of damage a vulnerability can cause if exploited.
It’s regarded as far more accurate compared to Vulnerability Scanning due to its depth and the use of human resources in the test process.
It, too, does have its drawbacks. However, it is still an essential part of cybersecurity.
Benefits of the pentest
- Live and manual tests lead to greater accuracy and much more thorough results.
- Unlike Vulnerability Scanning, Penetration Testing can weed out false positives more accurately.
- Most problems in the infrastructure can be solved with just one annual test or after a major system change.
Limitations of the pentest
- Due to the human element and the extensive testing protocols, pentests can take up to 1 to 3 weeks to compile a report.
- Due to the use of ethical hacking and a plethora of software tools, tests can be expensive and can range from $15,000 to $70,000 based on the number of IPs.
- A single pentest only provides a snapshot of that point in time. Once that pentest is complete, if the vulnerabilities are not remediated immediately, it does no good.
- New vulnerabilities can come up the day after a pentest is complete, which is why it needs to be continuous instead of a one-time job
How is Penetration Testing different from Vulnerability Scanning?
One of the key differences between vulnerability scanning and pentesting is that there are only automated vulnerability scans, whereas a pentest could be both automated and manual.
To further explain how penetration testing is different from a vulnerability scan, it is necessary to talk in terms of breadth and depth.
DEPTH OF SOLUTION
Based on a vulnerability scanning policy, a cybersecurity team gets a report that gives the broad scale of vulnerabilities that could cause possible harm to your business and system.
Penetration testing, however, goes deeper to find out the extent of damage the vulnerabilities can cause if they are exploited. Penetration testing makes use of extensive software tools to expose how much of a risk and threat a vulnerability is, by simulating a controlled cyber attack.
Ethical hackers can help with penetration testing by giving you an in-depth look at how much damage a business could suffer and what kind of data can be found in the places where it is vulnerable.
COST
Compared to penetration testing, the cost of a vulnerability scan is quite low, and it is more of a reactive approach than a preventative control like penetration testing.
Unlike a vulnerability scan, penetration testing is quite expensive and can cost a company anywhere from $15,000 to $70,000 (depending on the size and infrastructure).
| That’s why it’s recommended to go for a fully managed and continuous security solution that not only takes care of continuous pentesting, but also provides immediate remediation at an all-inclusive cost. Start with Cybersecurity Prevention |
EXECUTION TIME
Penetration testing also takes a lot more time to process in comparison to vulnerability scanning. Vulnerability scans can be done pretty quickly, but one pentest can take from one to three weeks.
A penetration test mimics a hacker seeking access to a company system by conducting a hands-on investigation and exploiting weaknesses. Actual analysts, also called ethical hackers, find flaws and then try to show that they can be exploited, which is what they do.
They seek to penetrate and harvest data from a network in a non-harmful manner using methods such as password cracking, buffer overflow, and SQL injection. The main purpose of a pentest is to show how much of a financial impact an exploit can have on a business.
An important factor to remember about penetration testing is the human element. There is no such thing as an automated penetration test, hence the reason for the slower turnover, execution, and higher expense.
An example of the human element is that penetration tests can also be conducted based on social and physical engineering tests.
RUN SIZE
Vulnerability scanning is larger in size than penetration testing. It is typically run by administrators or security personnel who are well-versed in networking.
A pentest attempt could be far more intrusive than a vulnerability scan and often leads to a denial of service.
SKILLS
To use the vulnerability scanning product effectively, product knowledge is required by the personnel.
Whereas a pentest requires a plethora of cybersecurity skills and expertise. Penetration testing involves ethical hackers probing and simulating a hack to find out the extent of damage an exploit can cause.
A pentester is well-versed in the following:
- Internal and external testing
- Front-end web development technologies
- Web application programming languages such as PHP and Python
- Web APIs such as SOAP and restful web services
- Networking protocols
- Operating Systems (OS) like Kali Linux, BackBox, and BlackArch to name a few
- Network technology such Firewalls, Intrusion Detection Systems (IDS), and Switches
- Testing tools and scripting languages
FREQUENCY
Vulnerability scans may be regularly performed on any number of assets to ensure that known vulnerabilities are found and addressed. As a result, one can quickly remove more significant vulnerabilities from your essential resources.
BASIC REQUISITE IN MANY SECURITY STANDARDS
Because of the level of detail that comes with penetration testing, it is now a requirement for a plethora of recognized security standards like PCI DSS, HIPAA, FedRAMP, SOC 2 Type 2, etc.
Which one should you use: Vulnerability Scanning or Penetration Testing?
When it comes to which method to use in terms of finding vulnerabilities within your system, we recommend using managed vulnerability scanning and continuous penetration testing in tandem.
Vulnerability scans are inexpensive and can be done fairly regularly, and a penetration test needs to be done frequently to get an extensive look at possible exploits in your system and remediate swiftly.
A good rule of thumb is that vulnerability assessments are more helpful if you are just starting and don’t know the security posture of your organization. Whereas pentesting is recommended if an organization is confident in its security posture and is looking to approve or disapprove its effectiveness.
When researching cybersecurity solutions and weighing pros and cons, it’s always better to consult with a cybersecurity expert. The team at Cyvatar can get you started at no cost with a free security assessment and guide you from there.
