What is network segmentation? | Best Practices

What is network segmentation? | Best Practices
Cyvatar | 04/07/2022What is Network Segmentation?
Don’t put all your eggs in one basket. Likewise, do not keep your network unsegmented, exposing your entire network should there be a breach or cyberattack.
Businesses and organizations begin to grow larger in scale over the course of time. The larger the business, the bigger and more complex its infrastructure and network.
As networks grow larger and more complex, they get more difficult to maintain and secure.
Network segmentation is an architectural approach to divide large networks into smaller segments or subnets, each acting as its own individual network. Doing so allows better protection and management of data.
Also, network segmentation allows network managers to control the flow of information and traffic, greatly improving the efficiency of threat detection, localization of threats, and performance increase.
Why is Network Segmentation necessary?
Network segmentation allows you to segregate sections of your network. In an event where there is a data breach or hack, intruders will be isolated to only the segment they’ve breached and cannot access the rest of the data stored in other segments in the network.
This also allows IT and cybersecurity teams to narrow down the targeted network and negate the threat or intruder with higher efficiency.
Hackers and cybercriminals now utilize bad actors and malware that can spread like wildfire once inside your network. Segmentation helps prevent that.
Why should you consider network segmentation for your organization and network?
Well, according to IBM Cost of Data Breach Report 2020, it takes about 280 days on average to locate a data breach within a network and shut it down.
Implementing network segmentation can greatly reduce the damage of a data breach and make it much easier for recovery as well!
Still not convinced? According to the 2021 Cost of Data Breach report by IBM, data breach costs have risen from $3.86 million to $4.24 million USD, the highest average in the last 17 years!
The costs will only continue to rise and with the implementation of remote work, cybersecurity has become a top priority for almost every organization in 2022.
With network segmentation, the security personnels have a powerful tool at their disposal to prevent unauthorized users, be it malicious attackers or curious insiders from gaining access to valuable organizational assets in the form of data and high confidential intellectual property.
This could be spread across the hybrid and multi-cloud environments; public clouds, private clouds and software-defined networks (SDNs). All of this needs to be protected against attacks.
It becomes very important to understand the trust assumption concept to understand the security.
The Trust Assumption
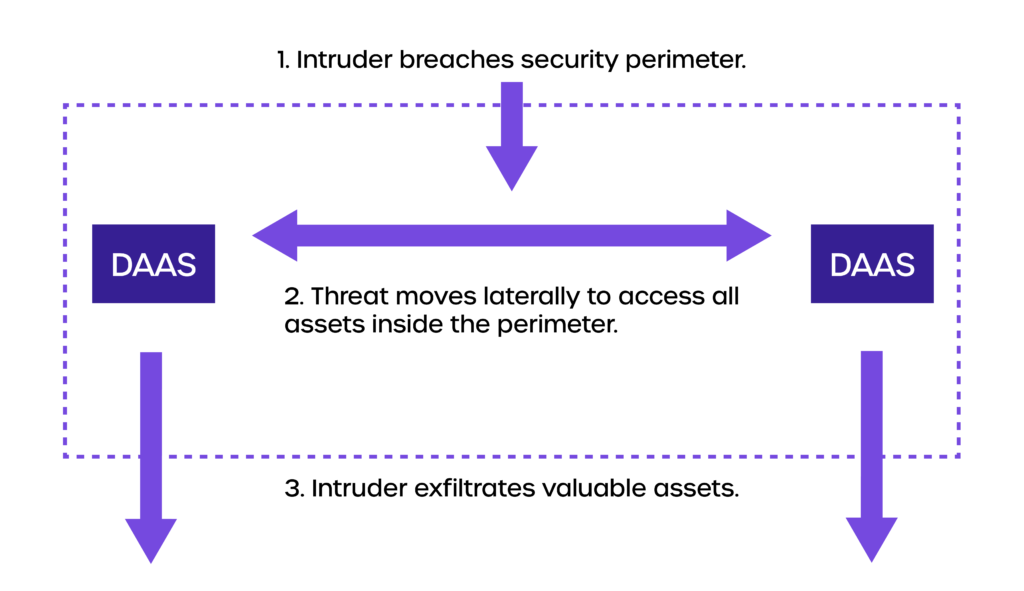
We come with the inherent trust assumption that most people are trustworthy, if not all. This leads to fewer restrictions leading to security breaches.
Thanks to the trust assumption, once the threats penetrate the perimeter, they are free to move laterally in the unsegmented network leading to access virtually any data or Desktop-as-a-Service (DaaS).
The Zero Trust Response
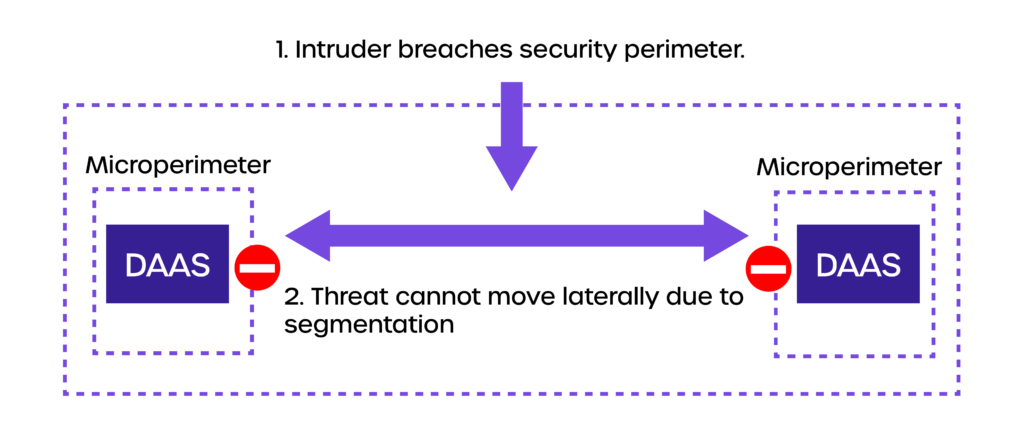
Because of the inherent fragility of the assumed trust, many organizations have started to embrace zero trust strategy. Zero trust comes with an assumption that nobody is trustworthy.
Zero trust leverages on the principle of “protect surface” built around organization’s most valuable and critical DAAS.
Since it contains what is critical for operations, the protect surface is of the order of magnitude much smaller than the attack surface of the full network perimeter.
This is where network segmentation plays a significant part. Using network segmentation, architects can construct microperimeter around the protect surface, essentially creating a second line of defense.
Per the Cost of Data Breach 2021 report by IBM, the zero truth approach helped reduce cost. The average cost of a breach was USD 1.76 Million less at organizations with the zero trust approach compared to the ones without it.
Network Segmentation Strategy
There are different architectures and methods to set up network segmentation for your network. Usually, network segmentation utilizes a combination of firewalls, Virtual Local Area Networks (VLAN), and software-defined networking (SDN).
Here are the three most common types of network segmentation:
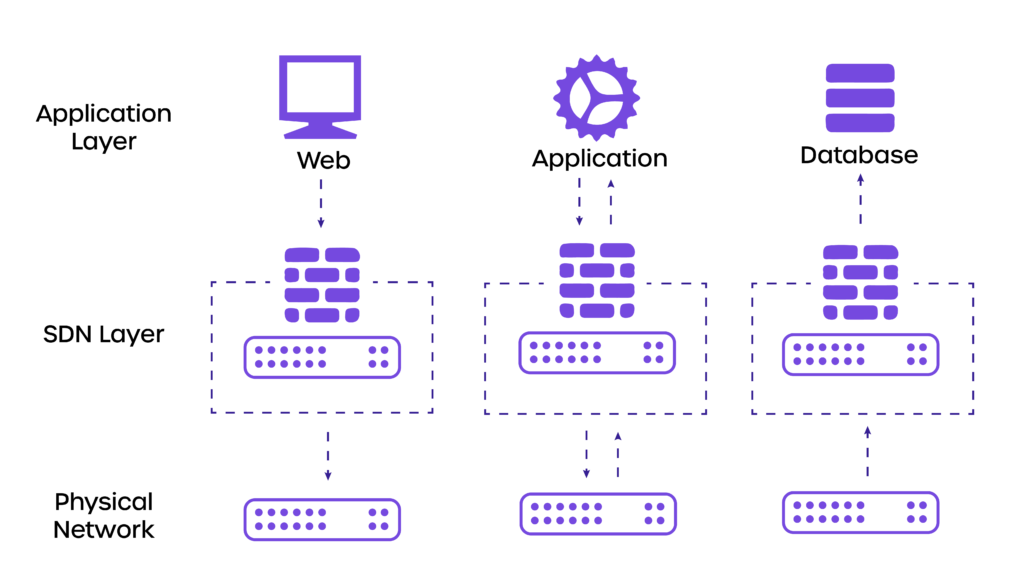
1. SDN Segmentation
SDN (Software Defined Networking) is a networking technology that separates the Control and Data Planes and handles all networking functions (routing, switching, load balancing, and so on) entirely in software.
A more modern approach to segmentation employs an SDN-automated network overlay. One disadvantage of this approach is the level of complexity required for successful micro-segmentation.
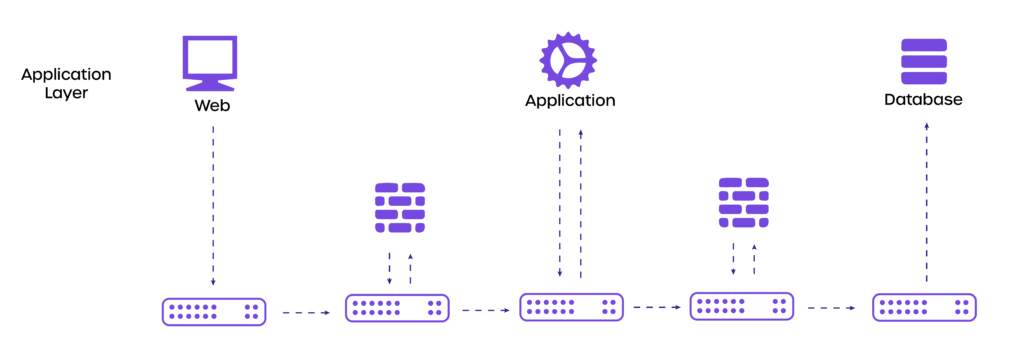
2. Firewall Segmentation
Firewalls are an alternative method to implement segmentation within a network. By deploying firewalls within the internal zones of your network, segmentation can be created between one functional partition of your network from another.
To create internal zones, firewalls are deployed inside a network or data center. This helps segment functional areas from each other to limit attack surfaces, in turn, confining threats to a zone.
No matter how effective they may seem, there are some inherent disadvantages that come along:
- When a firewall is used in internal segmentation, it brings its fair share of complexity. Thanks to the thousands firewall rules needed to segment internal networks.
- Misconfigurations of firewalls could break an application and affect the business.
- Huge costs. Since they come in pairs for multiple sites, it could cost in millions.
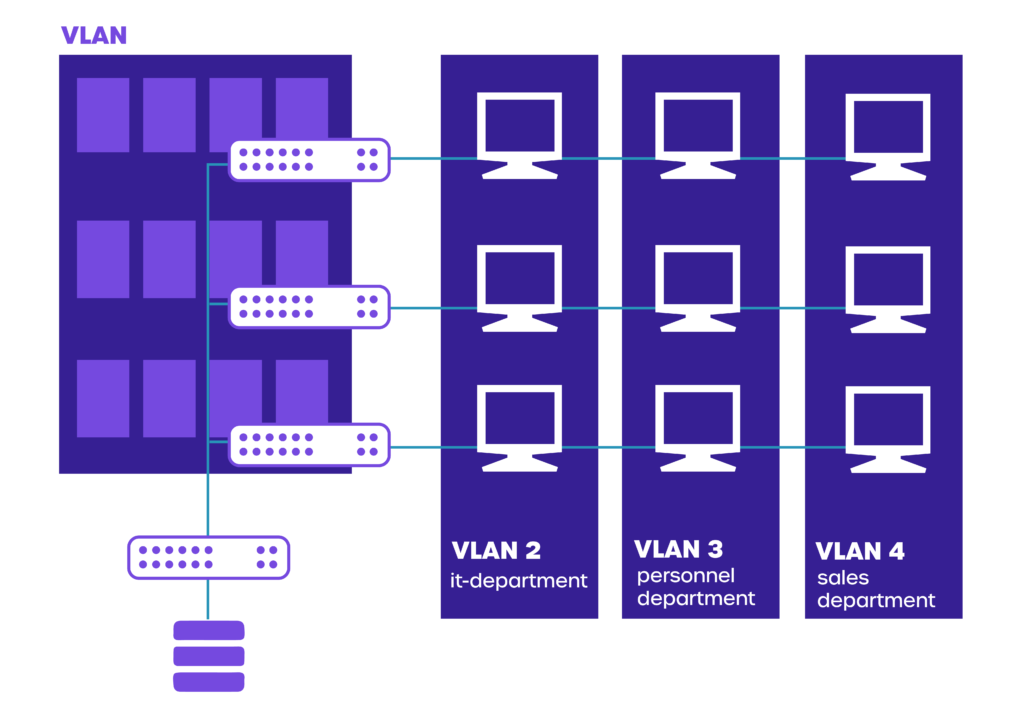
3. VLAN Segmentation
VLANs or subnets are commonly used to segment networks. VLANs divide networks into smaller segments that connect hosts virtually.
Subnets, which are connected by networking devices, use IP addresses to segment the network.
Although these approaches effectively segment the network, they frequently necessitate extensive re-architecting and can be difficult to maintain.
Network Segmentation Best Practices
When it comes to network segmentation and segregation, a certain amount of proactivity needs to be present in order to maintain high levels of efficiency and security.
This is also necessary for ensuring compliance with regulatory bodies like the PCI for example.
Here are the best practices you can commit to ensuring the best results from a segmented network.
- Implement Low Privilege
When you implement network segmentation and segregation, it is important that you ensure employees and personnel have limited access to the network.
By minimizing who has access to what parts of the network based on their responsibilities and needs, you strengthen your overall security posture.
This also makes it easier for you to monitor and maintain traffic within your network.
- Third-party access limitations
When having your network segmented, it’s always better to minimize the amount of access third-party apps and teams have into your network.
This will entail reducing the number of entry points for potential attacks via third-party access points.
“Providing remote access to third parties without implementing the appropriate security safeguards is almost guaranteeing a security incident and a data breach involving sensitive and confidential information,” said Dr. Larry Ponemon, Chairman and Founder of Ponemon Institute.
“It is important that organizations assess the security and privacy practices of the third parties that have access to their networks and ensure that they have just enough access to perform their designated responsibilities and nothing more.”
Per a recent report by Security magazine, 51% of data breaches in networks were solely from third-party access and breaches. Food for thought!
Another method to negate breaches from third parties is by creating isolated segments or portals solely for your third-party apps!
- Regular Monitoring and Auditing
The first step in developing a strong segmentation strategy is to segment your network. The next step is to constantly monitor and audit your network to ensure that the architecture is secure and to identify any gaps in your subnetworks that could be exploited.
Monitor your network to quickly identify and isolate traffic and security issues. Then, on a regular basis, conduct audits to identify architectural flaws.
| Get continuous monitoring & scanning for your org’s network with remediation included. Learn about Cyvatar’s prevention plans. CYBERSECURITY PREVENTION PLAN |
This is especially important as your company evolves and grows; as your company changes, your network architecture may no longer meet your requirements.
Regular audits can help you determine when and where your network segmentation design needs to be tweaked for optimal performance and security.
- Map Legitimate paths over Illegitimate network paths
Pay attention to how you plot access and what paths users will take to connect to your network when evaluating and planning your architecture design.
While it is critical to create- secure access points for your users, keep in mind how bad actors may attempt to gain unauthorized access to those same subnetworks.
Assume you have firewalls between your vendors and the data they need to access, but only some of these firewalls can block bad actors.
If this is the case, you should reconsider your architecture. To improve security, design your network so that legitimate paths are easier to navigate than illegitimate paths.
- Don’t Oversegment or Undersegment
Projects involving segmentation can be challenging. A successful segmentation strategy includes a few necessary and distinct subsections.
Too many can become overly complicated. Too few can jeopardize the security of your system.
This is why it is critical to understand who requires which data.
You may end up over-segmenting or under-segmenting if you don’t have a good understanding of your users and what they require to do their jobs.
This is a common problem, which means you may have to go in and change the entire network.
Gartner discovered a few years ago that over-segmentation required the redoing of more than 70% of segmentation projects.
Keep in mind that you must create policies that define what can and cannot be accessed between each pair of zones. As a result, the more zones you create, the more policies you must manage.
Oversegmenting your security management can quickly expand the scope of your security management, making it costly and inefficient.
Consider this: While you want to group similar network resources, keep in mind that you should “build a fence around the car park, not a fence and gate around every car.”
Network Segmentation Examples and Use Cases
1. Healthcare Organizations
They must protect PHI data while complying with the healthcare cybersecurity compliance framework.
Network segmentation is one of the key security controls that must be implemented besides isolation of sensitive systems, accurate mapping and network connection control.
| Using Network Access Control (NAC) to Build VLANs and Set Access Control Lists (ACLs) Network Access Control (NAC) solutions provide access management and network visibility through policy enforcement on network devices and users. Once medical devices have been identified and profiled, you can use the NAC to assign different switch ports to VLANs. After your VLANs are defined, you can define ACLs to restrict specific communications to and from the VLAN and all devices within it. A NAC can reduce the security risks inherent in legacy infusion pumps by segmenting the network and applying defined access policies for the pumps. The process is as follows: 1. Identify and profile pumps — find IV pumps and assign risk impact scores based on usage and criticality. 2. Pinpoint vulnerabilities — identify device-specific vulnerabilities and tag device IP addresses. 3. Configure access control rules in the NAC — segment the devices on a seperate VLAN to isolate vulnerable IV pumps from the rest of the network and allow only necessary communications. 4. Monitor communications — all communications should be monitored to guarantee continuous service and ensure devices adhere to policy before pushing configuration to the NAC. |
2. PCI DSS Compliance
PCI DSS ensures that the credit card information of customers is stored and processed securely online by merchants and businesses.
Network segmentation makes sure that the system components within the cardholder data environment (CDE) are isolated.
3. User Group Access
Many large enterprises segment their network into smaller subnets each corresponding to different internal departments.
The subnets have authorized group members and DaaS to do the job.
4. Public Cloud Security
Cloud service provides ‘n’ number of services to their customers. These customer services sit on top of cloud infrastructure and need their own protection from customers besides the overall cloud security.
It’s important to segment the public applications in the cloud from a hybrid cloud environment. Network segmentation helps achieve just that.
5. Guest Wireless Network
Using network segmentation, an organization can ensure WiFi to public or guest users at a relatively lower risk.
In a segmented network, a guest user always logs in to a microsegment that just provides Internet access and nothing else.
Benefits of Network Segmentation
We have already discussed how network segmentation is a better strategy than having a flat network. Here are some of the benefits of network segmentation detailed:
- Stronger Security
Network segmentation reduces security risks by establishing a multi-layered attack surface that prevents lateral network attacks.
As a result, even if an attacker breaches your first line of defense, they are confined to the network segment they access.
- Better Network Monitoring
IT teams and cybersecurity teams can better monitor the system when it is divided into segments.
You can even divide your teams to monitor specific sections of the network based on your preference. This increases responsiveness during threats and the overall efficiency of both your network and teams.
- Increased efficiency
Traffic is restricted to specific zones based on necessity. This reduces the number of hosts and users on any given subnet, reducing congestion and improving overall performance.
- Easy Adherence to Compliance
Network segmentation separates regulated data from other systems, making it easier to manage compliance and apply policies in a targeted manner.
If vulnerabilities alone are not enough for you to segment the network, then these benefits sure would entice you to give a thought to network segmentation.
Cyvatar’s 3 fully managed security subscriptions come with inherent network segmentation and continuous monitoring. Take a look to see if they are a solution for your network segmentation needs and contact us to learn more.
