How HTML smuggling is targeting the banking sector

How HTML smuggling is targeting the banking sector
Cyvatar | 04/04/2022What is HTML smuggling?
HTML smuggling is an infamous technique in which security devices are bypassed through the use of malicious HTML code after passing through firewalls while still being within the endpoint of a web browser.
The HTML Smuggling technique uses HTML5 and Javascript features to circumvent traditional network security solutions such as email scanners, proxies, and sandboxes.
This is accomplished by smuggling an encoded malicious code within the well-crafted HTML attachment or a link to an external web page containing the encoded malicious code.
Once the encoded code makes it through the firewall, the user’s browser decodes the malicious scripts and assembles the payload on the host device, mostly in the download folder.
Using the conventional security solutions, there is nothing for the firewall and security systems to detect as there is no malicious code transferred over the wire.
| Using cloud-based responsive cybersecurity solutions help mitigate the HTML smuggling risks. |
The sole purpose of HTML smuggling is to carry over malicious software to a target device via the use of downloads and data URLs or by creating a Javascript blob with a MIME trigger which then initiates a download onto the target device.
Below is a visual explanation of how HTML Smuggling occurs.
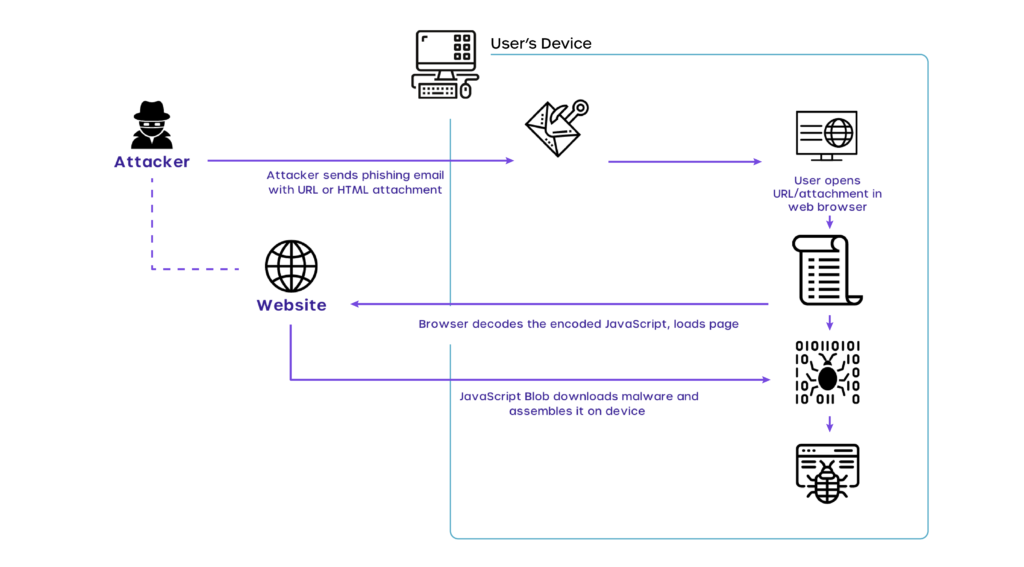
How does HTML smuggling work? Some HTML smuggling techniques
The HTML5 ‘download’ attribute for anchor tags enables HTML smuggling. When a user clicks on the HTML link, the file referenced in the href tag is downloaded. As an example:
| <a href=”/malware/evil.docx” download=”innocent.docx”>Click</a> |
When the user clicks the link in the email, the browser saves ‘evil.docx’ on the device and renames it to ‘innocent.docx.’
Javascript can accomplish the same thing:
var myAnchorElement = document.createElement(‘a’);
myAnchorElement.download = ‘innocent.doc’;
When working with Javascript, a Javascript blob can be used to create the file to be downloaded. A JS blob is a raw data representation that can be passed to a Javascript API that expects a URL.
Instead of providing a URL link to the file to be downloaded, it can be created from a blob within the Javascript itself.
var myEvilBlob = new Blob([myEvilFile], {type: ‘octet/stream’});
Finally, we simulate the user clicking on the link and starting the file download by creating a URL with the URL.createObjectURL command and then invoking the click action from within the Javascript:
var myInnocentUrl = window.URL.createObjectURL(myEvilBlob);
myAnchor.href = myInnocentUrl;
myAnchor.click();
Why is this technique so effective? Simply put, the firewall and security systems in place see the expected traffic. Not only that, Javascript can be obfuscated to hide the malicious contents of the blob.
HTML smuggling in the banking sector
HTML Smuggling is a highly evasive malware delivery technique as it ditches most of the usual security measures.
It is frequently and increasingly used in email campaigns to deploy banking malware, Remote Access Trojans (RATs), and other types of malware payloads to cause attacks.
Since the malicious script runs directly via the phishing page on the victim’s browser, it can easily evade email gateways, web proxies, and other techniques blocking malicious attachments.
The most recent case regarding HTML smuggling can be traced back to July of 2021 when a spear-phishing/ banking malware campaign known as Mekotio attacked banking institutions from Brazil, Mexico, Spain, Portugal, and Peru.
The Mekotio campaign had attackers send in emails with malicious links. Below is a sample email from the campaign.
When a user clicks the unassuming HTML link, the entire smuggling process initiates.
For a better understanding of how the Mekotio campaign works follow the infographic below:
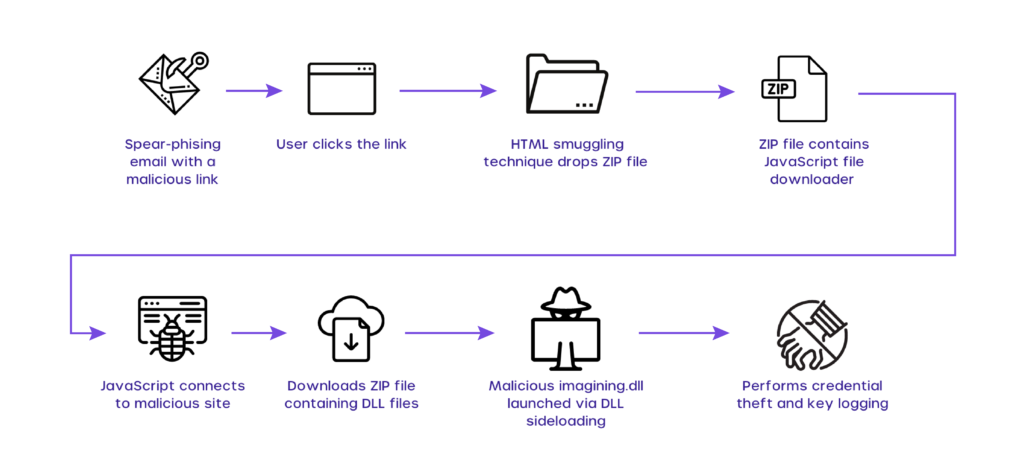
A malicious website, hxxp:/poocardy[.]net/diretorio/, is used in this campaign to implement the HTML smuggling technique and drop the malicious downloader file.
When rendered in a browser, the image below depicts an HTML smuggling page.
The Mekotio campaign’s HTML smuggling page. To download the malicious ZIP file, the “href” tag refers to a JavaScript blob of an octet/stream type.
Note: Researchers at checkpoint.com have found a new attack flow of the Mekotio.
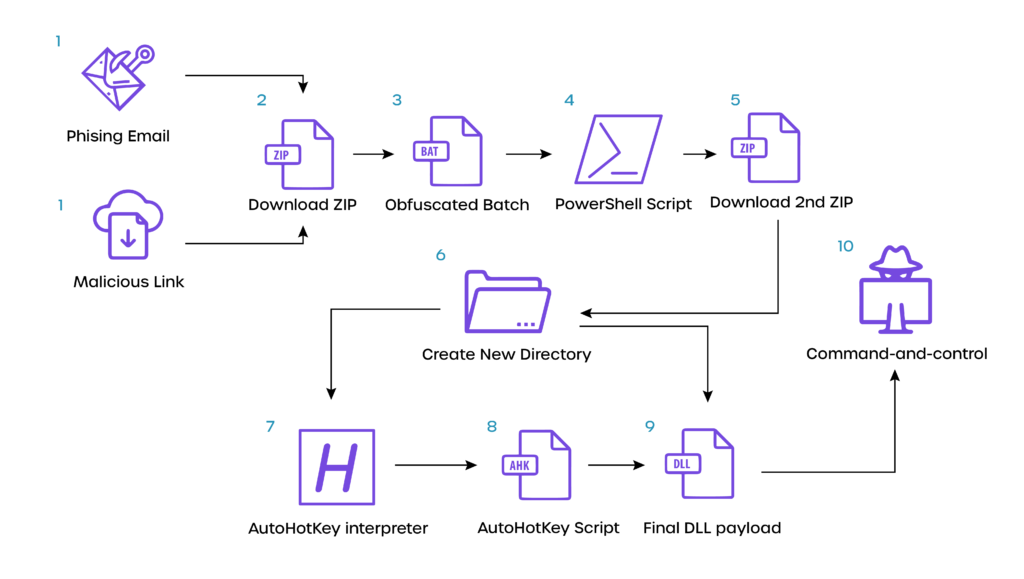
HTML Smuggling is on the rise and you should be worried. Here’s Why
While HTML Smuggling is feared for being a constantly evolving banking sector threat, innovation and evolution by cybercriminals have made it more than just a malicious financial cripple tool.
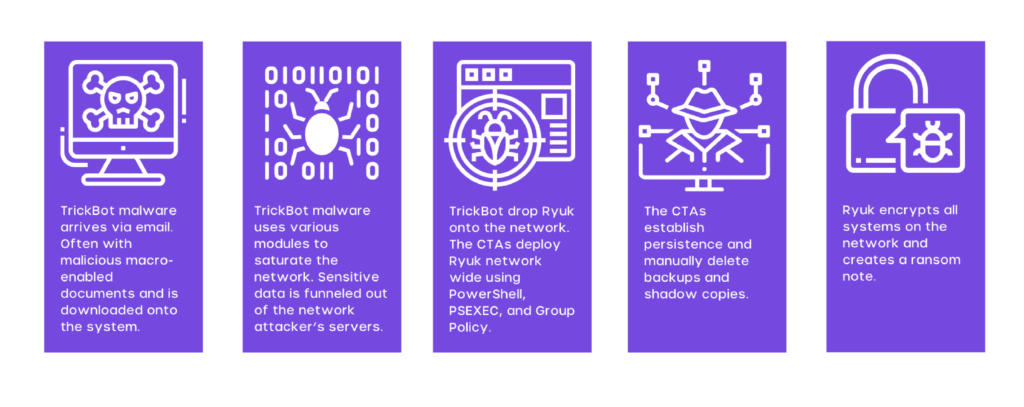
The most imminent and latest threat to plague the internet is the TrickBot campaign. The highly evasive loader technique & tool has been reported and recognized as dangerous by Microsoft itself.
Let’s take a look at the origins of TrickBot and its various iterations over the years.
TrickBot is a distant descendant of the ZeuS financial Trojan, which first appeared in 2005, but is most commonly linked to the Dyre or Dyreza banking Trojan, which was shut down in 2015.
It first appeared in 2016, repurposing some of Dyre’s code and keeping its banking credential harvesting and web injection infrastructure.
TrickBot has grown into a malware behemoth with a slew of plugin modules, crypto mining, persistence capabilities, and a growing link to ransomware attacks.
Since June 2019, the MS-ISAC has noticed a growing link between initial TrickBot infections and subsequent Ryuk ransomware assaults.
TrickBot drew the attention of both government and business sector entities in the fall of 2020 when it was announced that the US Cyber Command and private sector partners had taken steps to limit TrickBot’s reach and lower the likelihood of it spreading.
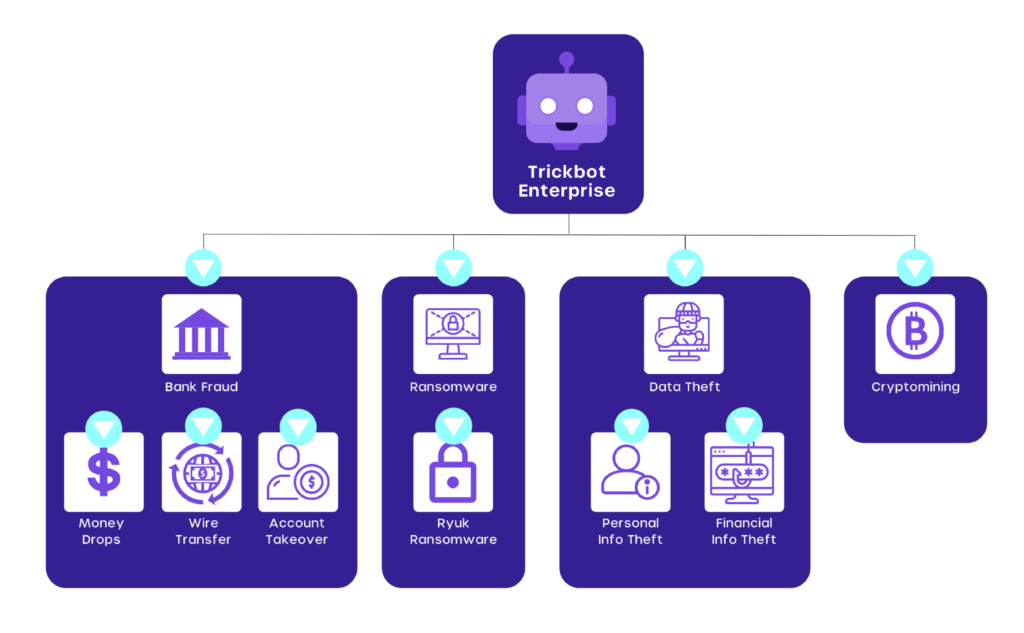
Though TrickBot may have been dumped by a precursor infection, the more serious issue is the likelihood of a subsequent ransomware attack.
Cyber threat actors (CTAs) are likely to install a ransomware strain such as Conti or Ryuk across the impacted business if they judge the hacked environment as a worthy target.
How do you defend against HTML smuggling?
While the most obvious answer to defending HTML smuggling is to disable Javascript, completely taking that route is unfeasible and highly unlikely.
This is because browsers and many applications rely on Javascript for proper functioning. What can be done, however, is strengthening your organization’s network and cybersecurity.
Here are a few ways to bolster your protection from HTML smuggling attacks:
* Using a NextGen Firewall
Using an external or NextGen Firewall allows you to block the source IP address from where the smuggling or phishing attack is occurring from.
A NextGen firewall will have an updated database of malicious sources which can be used to detect HTML files from dangerous sources and prevent entry into the target device or network.
* Security Awareness Training
The process of HTML smuggling always involves actions from the unsuspecting user. Be it downloading the suspicious attachment to opening or launching the payload.
In order to negate this from happening, you can implement security awareness training for all your employees and staff.
Doing so will allow them to be wary of suspicious links and spot malicious payloads and content before clicking on them.
You can also bolster your security by investing in a dedicated cybersecurity team to monitor your network and systems in real-time.
Doing so helps in faster reaction times when it comes to a threat and the ability to have regular internal checks to ensure the prevention of breaches before they can even occur.
* Network Segmentation
Having a flat network can be a recipe for disaster as once there is a data breach or malicious software is in your system, it has access to data from the entire network.
In such cases, ransomware can hold your entire network and business at stake as you will be locked out of every system until you pay the ransom or risk losing all the data.
Network segmentation segregates sections of your network into their own silos, so in the case of a data breach, the malware can only infect one section of the network and the remainder of your network is intact.
This also allows you to narrow down the threat and minimize damage.
* Configure Endpoint Security Products
Your organization may be using a third-party application or source, this can leave you vulnerable as they too have entry points that aren’t usually accounted for.
So in order to bolster security in these sections, you need to configure your endpoint security products to block
- JavaScript or make sure VBScript can’t start running a downloading executable file automatically.
- Scripts that could be obfuscated
- Execution of programs “Unless they meet a prevalence, age, or trusted list condition.”
How Cyvatar saves the day
Going by traditional security means, it becomes quite a challenge to avoid homogeneous threats such as HTML smuggling which camouflages well and makes it difficult to understand if an HTML resource is a malicious code in disguise.
Cyvatar intends to change this with its responsive cloud protection coupled with advanced AI and machine learning techniques.
Try a risk-free 30 days trial to experience the difference.
