What is CMMC compliance? Full CMMC compliance checklist

What is CMMC compliance? Full CMMC compliance checklist
Cyvatar | 04/19/2022The biggest US Department of Defense (DoD) contractor: Lockheed Martin Corporation has a contract value exceeding $40 billion. Can you imagine the number of checks and balances that the US government would put in place for any defense contractor?
The Cybersecurity Maturity Model Certification (CMMC) is one way to ratify a US government contractor’s cybersecurity preparedness. In this article, we will look at every single aspect of CMMC compliance, especially its compliance checklist.
What is CMMC Compliance?
CMMC is a pivotal requirement for businesses that want to work for the US government. It helps the US government determine if an organization meets the cybersecurity requirements for handling controlled or vulnerable data.
It was formally introduced on January 31, 2020, and has undergone changes. But at its core, CMMC is designed to ensure that the contractors, manufacturers, and even the small businesses involved in the defense industrial base (DIB) meet stringent cybersecurity standards.
It is expected that all new DoD contracts will contain the CMMC requirements by 2026.
What is the CMMC certification?
The CMMC certification is a program initiated by the US Department of Defense to measure the contractor’s capabilities and preparedness in cybersecurity.
It is a collection of frameworks and processes that borrow from existing cybersecurity standards such as Federal Acquisition Regulation (FAR), Defense Federal Acquisition Regulation Supplement (DFARS), and the National Institute of Standards and Technology (NIST).
The goal of the certification is to improve the security of Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) which the federal contractors will be handling when they work with the US government.
CMMC 2.0 aims to further improve the existing cybersecurity standards of the federal agencies dealing with the defense.
Who needs the CMMC Compliance certification?
It is required by organizations that work with DoD data. The CMMC compliance requirement applies to main contractors, subcontractors, and every vendor across the supply chain.
The CMMC compliance levels are based on the kind of information that they handle. If it is not classified information, then they only need a Level 3 clearance or below.
If the organization handles high-value information, it would require a Level 4 certification or higher.
The DoD contract will specify the level of compliance that the individual contractor is supposed to meet.
With CMMC certification, the organization can pursue government contractors and will be in a position to deal with privileged information.
How do you get CMMC Compliance certification?
Government contractors and those who work with government entities have to be ratified by a third party. They will audit the cybersecurity measures that the contractors have put in place, identify their level of maturity, and their preparedness to handle any untoward incidents.
The contractors will have to go through a thorough audit before they can attempt to certify themselves.
Cyvatar platform can help go through the CMMC framework and guide them across the changes that they can make and get them ready for the certification process.
Even if you are not working with government agencies, you can still get CMMC certification.
To be CMMC compliant is to be ratified that you follow the most rigorous cybersecurity best practices.
What are the CMMC Certification Levels?
The DoD states: ”The model is cumulative whereby each level consists of practices and processes as well as those specified in the lower levels.”
So, Level 5 companies will fulfill Level 5, Level 4, Level 3, Level 2, and Level 1 requirements.
Each level has a set of processes and best practices that range from following basic cyber hygiene to advanced cybersecurity levels. As you go up each level, it indicates a higher level of protection for sensitive information.
For the organization to achieve a specific CMMC level, they need to clear the lower levels.
The CMMC maturity levels comprise all 171 practices spanned across 17 domains listed in the following image.
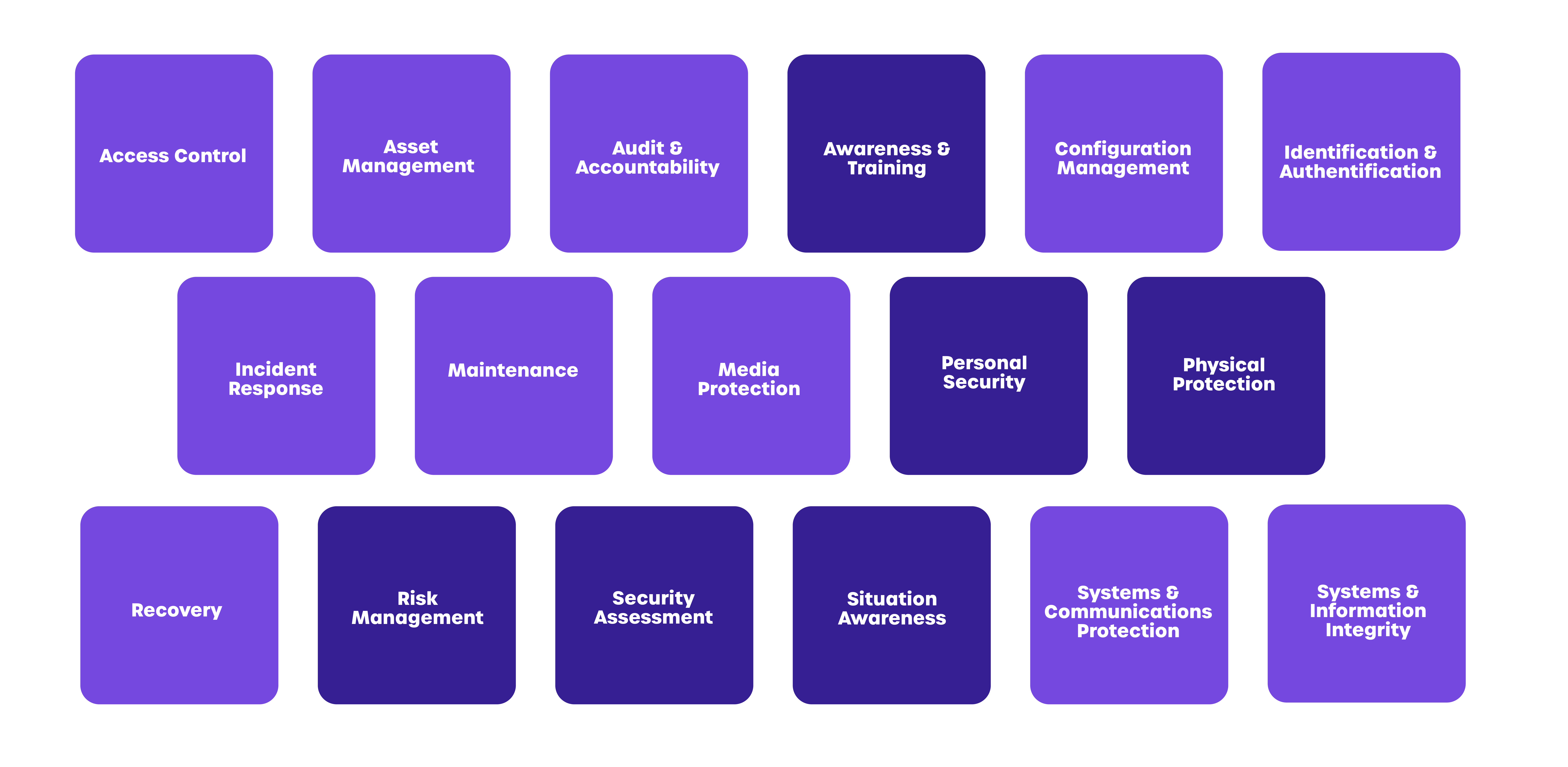
The following summary will give you an overview of the appropriate CMMC levels for your business.
CMMC Level 1 (Basic Cyber Hygiene)
At this level, the organization is required to perform specific practices in an ad-hoc manner. Process maturity isn’t assessed at this level, and they may or may not rely on documentation.
Level 1 focuses on basic cyber hygiene and the requirements here are similar to the ones specified in 48 CFR 52.204-21, which is a contract clause to the Federal Acquisition Regulation (FAR) for “the basic safeguarding of contractor information systems that process, store or transmit Federal contract information.”
QUICK POINTS
| ➤ 17 practices ➤ Equivalent to all practices in Federal Acquisition Regulation (FAR) 28 CFR 52.204.21 |
CMMC Level 2 (Intermediate Cyber Hygiene)
The organization must establish and document policies and practices to guide the CMMC implementation.
Documenting these practices enables them to be replicated at ease, and develop mature capabilities. Level 2 consists of a subset of requirements specified in NIST SP 800-171 and other standards.
QUICK POINTS
| ➤ 72 practices ➤ Comply with the FAR ➤ Includes a select subset of 48 practices from the NIST SP 800-121 r1 ➤ Includes an additional 7 practices to demonstrate intermediate cyber hygiene |
CMMC Level 3 (Good Cyber Hygiene)
In level 3, the organization has to establish, maintain and resource a plan to demonstrate the set of activities required to implement CMMC.
The plan includes information on resourcing, project plans, missions, objectives, training, and stakeholder buy-in.
Level 3 focuses on CUI and includes all the security requirements specified in NIST SP 800-171 and 20 additional practices.
QUICK POINTS
| ➤ 130 practices ➤ Comply with the FAR ➤ Includes all practices from the NIST SP 800-121 r1 ➤ Includes an additional 20 practices to demonstrate good cyber hygiene |
CMMC Level 4 (Proactive Cyber Hygiene)
In this stage, the organization should review and measure practices for effectiveness. At this level, the organizations should be able to take corrective action by themselves when necessary and inform the management if issues persist.
Level 4 focuses on protecting CMMC CUI from APTs and should adhere to enhanced security requirements from Draft NIST SP 800-171B and other cybersecurity best practices. By doing so, organizations will be in a position to adapt to the changing tactics, techniques, and procedures (TTPs) used by Advanced Persistent Threats (APT).
QUICK POINTS
| ➤ 56 practices ➤ Comply with the FAR ➤ Includes all practices from the NIST SP 800-121 r1 ➤ Includes a select subset of 11 practices from Draft NIST SP 800-171B ➤ Includes an additional 15 practices to demonstrate proactive cyber hygiene |
CMMC Level 5 (Advanced Cyber Hygiene)
At this stage, the organization is expected to standardize and optimize processes across the organization. There is increased focus on the protection of CUI from APTs.
Following the practices required in CMMC level 5 increases the depth and sophistication of cybersecurity capabilities.
QUICK POINTS
| ➤ 171 practices ➤ Comply with the FAR ➤ Includes all practices from the NIST SP 800-121 r1 ➤ Includes a select subset of 4 practices from Draft NIST SP 800-171B ➤ Includes an additional 11 practices to demonstrate advanced cyber hygiene |
CMMC Compliance Checklist
Organizations that are preparing for CMMC certification have little leeway for error. They require full compliance at the time of submission. Organizations that make a CMMC compliance checklist will be better prepared to handle the vagaries associated with certification.
Here is the CMMC Compliance Checklist that businesses need to keep in mind:
- Assess your CMMC CUI capabilities
- Identify stakeholders
- Leverage Federal Frameworks
- Compliance with NIST Special Publication 800-171
- Finding third-party assessors
- CMMC Assessment Guide
- Create the System Security Plan (SSP)
- Build Plan of Action and Milestones
- Identify Gaps
- Have a centralized repository for the documents
- Conduct frequent mock assessments
- Start your CMMC Checklist
- Assess your CMMC CUI capabilities
The CMMC model aims to cover controlled unclassified information (CUI) in non-federal IT systems. CUI covers a variety of information related to tax, sensitive intelligence, intellectual property, legal actions, legal enforcement, and so on.
Understand which data is subject to CMMC and bring it under full compliance before you submit for CMMC certification.
- Identify stakeholders
There will be a few stakeholders who will drive this initiative. Find out who will act as the executive sponsor, who is in charge of providing proper oversight, execution, maintaining activities, and funding.
The information technology and information security department will do the majority of the work. You can also identify a registered provider organization (RPO) who will assist your organization in becoming CMMC compliant.
- Leverage Federal Frameworks
Organizations seeking CMMC certification should see how they can leverage the existing cybersecurity frameworks.
CMMC was developed through existing frameworks and there is an overlap with many of them.
It includes the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), CERT Resilience Management Model (RMM), and several NIST publications among others.
Some of the certifications that would help with the CMMC transition are as follows:
- FedRAMP
- FISMA
- ISO 27001
- Risk Management Framework
- NIST Special Publication 800-171
- Compliance with NIST Special Publication 800-171
It addresses the use of CUI in non-federal IT systems. For contractors that want level 3 certification, adhering to this is a must.
By being compliant with it, they will be able to meet 110 controls covered by CMMC. Since the CMMC framework includes only 20 more controls than SP 800-171, it is easier to be fully level 3 compliant if you can check this off your list earlier.
- Finding third-party assessors
You can complete your CMMC certification through a certified CMMC third-party assessment organization (C3PAO).
A good partner can help you with a smart strategy to meet your compliance requirements. Find a partner who can guide you through the CMMC process.
- CMMC Assessment Guide
Review your CMMC framework and appendices. These documents help you understand the controls CMMC establishes, their intent, and how each of these controls is defined.
The DoD has also provided assessment guides on understanding the five levels of CMMC.
- Create the System Security Plan (SSP)
NIST 800-171 mandates organizations working with the US government to document and update SSPs.
The update should also include network diagrams, compliance issues, relationships with other systems, and so on.
- Build Plan of Action and Milestones
The plan of action and milestones documents the remediation project plan and helps assess the timelines and resources necessary to be fully compliant.
Once you complete this, you will ensure compliance with CMMC NIST 800-171 and existing contracts, making you better prepared for the CMMC certification.
- Identify Gaps
If you need a level 1 certification, FAR 52.204-21 lists 15 controls, and you will need to provide evidence that you are performing these activities.
The 15 FAR controls align with 17 practices in NIST 800-171, for which you need documentation for its policies and processes.
For a maturity level 2 certification, the number of controls becomes 110.
- Have a centralized repository for the documents
Manage different versions of the document in a central repository. It shows your process maturity for the assessment team.
Process maturity isn’t only about documenting processes and policies. Making objective evidence available to C3PAO will reduce costs too.
By providing the documents in advance, the assessment team wouldn’t have to spend valuable time waiting for these documents.
- Conduct frequent mock assessments
Hire a service provider organization to help with CMMC compliance. Conduct a mock assessment with their assistance. The mock assessment offers a variety of benefits:
- An expert will be looking at the documents you have prepared
- The interviews will validate if the organization meets the requirements set by the US DoD.
You can check with a registered C3PAO consultant to conduct the mock assessments.
- Start your CMMC Checklist
Beginning your CMMC certification journey might seem like an insurmountable task, but creating a framework and a checklist to do is your way to success.
A CMMC checklist helps you identify the controls that an organization needs to implement.
How to get started with CMMC Compliance?
Organizations that are looking to start their CMMC compliance journey should start by meeting the 110 controls in CMMC NIST 800-171.
Preparation for this can take more than a year. Although the CMMC requirements have begun, all DoD vendors are given time till 2025 to obtain certification.
Getting CMMC certification is an uphill task, and it takes time. The waiting period between application and certification is a minimum of six months.
The National Defense Magazine estimates the annual CMMC costs for each maturity level accordingly:
➤ Level 1: $1,000
➤ Level 2: $28,050
➤ Level 3: $60,009
➤ Level 4: $371,786
➤ Level 5: $482,874
These estimates are based on the vendors being fully NIST 800-171 compliant, apart from meeting additional CMMC requirements.
Compliance Starts With Auditing
When you are going for CMMC compliance, one of the important aspects that you need to factor in is the right third-party partner with a trusted and approved third-party assessment organization (C3PAO).
Cyvatar helps defense contractors with their CMMC compliance journey by making them meet its stringent requirements. Get in touch with our cybersecurity experts.
