Introduction to SP 800 30 revision 1

Introduction to SP 800 30 revision 1
Cyvatar | 12/01/2021The NIST SP 800 30 provides guidance for conducting risk assessments of information systems and organizations. It further amplifies the guidance in SP 800-39.
The NIST 800 30 is designed in such a way that it can translate complex cyber threats in a language easy to understand for the board and the CEO.
Any organization, be it private or public is heavily dependent on information systems to successfully carry out its day-to-day operations. Information systems may include a plethora of entities from office networks to personnel systems to very specialized systems.
Information systems are always prone to online threats that can have adverse effects on an organization and its assets by exploiting vulnerabilities to compromise the integrity and confidentiality of the information stored and transmitted by such systems.
Hence, CEOs, CFOs, and other leaders must understand their share of responsibility in managing information security risks to safeguard the interests of missions and business functions of their organizations.
Risk assessment
The NIST SP 800 30 is used to do a risk assessment within the parameters of the NIST framework to identify, estimate and prioritize risk to the operation of organizations.
The purpose of risk assessment is to inform the decision-makers and support their risk responses by knowing:
- Both internal and external vulnerabilities
- Relevant threats to the organization
- Impact on their organization
- Likelihood of harm to occur
This eventually results in the determination of risks.
Risk assessments are part of a risk management process. These assessments are carried out at all three tiers of the risk management hierarchy, in turn, providing deep insights to senior management to take necessary actions in response to identified risks.
In particular, SP 800-30 guides execute the following steps of the risk assessment process.
- Preparing for the risk assessment
- Conducting the assessment
- Communicating the results of the assessment
- And maintaining it
Special publication 800 30 also guides on identifying specific risks to monitor on an ongoing basis (This helps an organization to determine if the risks have gone over a threshold value that is beyond the organization’s risk tolerance) and different courses of action to be taken.
Implementing NIST SP 800-30 in your organization
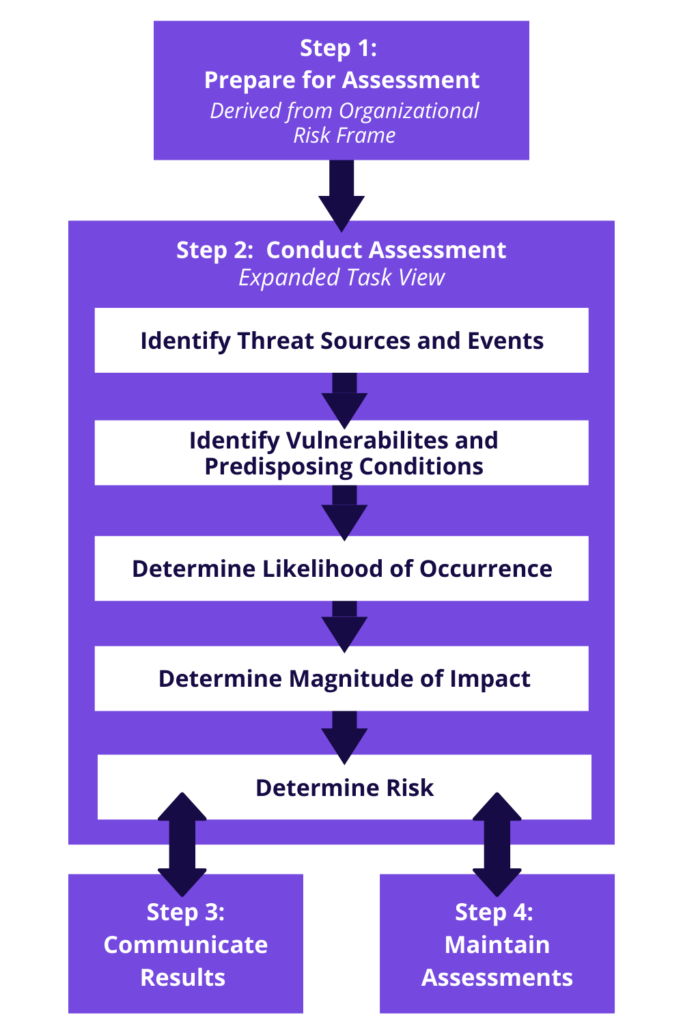
The implementation of SP 800 30 involves preparing and conducting risk assessments; communicating the assessment results; and maintaining the assessment.
Preparing for risk assessment
The first step towards risk assessment is to prepare for the assessment. The objective here is to build the context for the risk assessment.
That said, the purpose of the risk assessment is primarily influenced by two factors:
- An initial risk assessment
- A follow-up risk assessment from the previous triggered from the risk response or monitoring steps in the risk management
To prepare for the assessment, you need to identify:
- The purpose of the assessment
- The scope of the assessment
- Assumptions and constraints associated with
- The sources of the information for the assessment to be used as inputs
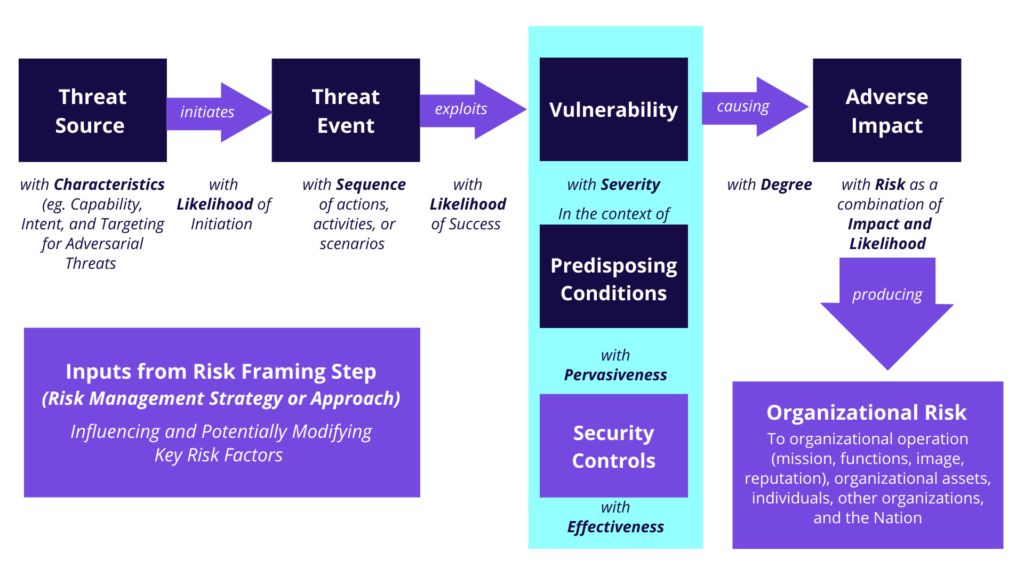
- Analytic approaches and risk model (See the pic below) to be employed during the assessment
STEP 1:
Let’s see how to prepare for risk assessment with the tasks.
- IDENTIFY PURPOSE
Task 1: Identify the purpose in terms of information the assessment needs to produce and the decisions it needs to support.
The purpose of the risk assessment is to ensure that it produces enough information to support the intended decisions.
- IDENTIFY SCOPE
Task 2: Identify the scope in terms of organizational applicability, time frame, and technology considerations. The scope determines what will be a part of the risk assessment.
The scope plays a key role in determining what will be covered in the assessment process. Creating the scope helps organizations to determine:
- The tiers that the risk assessment addresses
- The parts of the organization affected and in what way
- The decisions that the assessment results support
- How long the results of the assessment are relevant
- The factors that affect the need to update the assessment
- IDENTIFY ASSUMPTIONS AND CONSTRAINTS
Task 3: Identify certain assumptions and constraints based on which you conduct the assessment.
- IDENTIFY INFORMATION SOURCES
Task 4: Identify the sources of threat, vulnerability, descriptive and impact information to use in the assessment. Descriptive information sources allow organizations to identify the relevance of the threat and vulnerability information.
- IDENTIFY ANALYTIC APPROACH AND RISK MODEL
Task 5: Identify the analytic approach and risk model to use in the risk assessment.
Conducting the risk assessment
The next step is about conducting the risk assessment. This becomes an important factor in implementing an effective SP 800-30.
The objective here is to produce a list of risks that can be prioritized based on the risk level and later used to inform risk response decisions.
While conducting the risk assessment, you need to carry out the following tasks:
- Identify threat sources relevant to organizations
- Identify threat events that such sources could induce
- Finding vulnerabilities that could be exploited by threat sources using the threat events and further triggered by the predisposing conditions that may to successful exploitations
- Find the probability of identified threat sources initiated threat events and their probability of being a success
- Find the adverse impact on the organization’s operations and its assets.
- Determine information security risks
STEP 2:
Let’s see how to conduct risk assessments with the tasks.
- IDENTIFY THREAT SOURCE
Task 1: Identify the threat source, its intent, capability, and targeting features for adversarial threats.
- IDENTIFY THREAT EVENTS
Task 2: Identify the threat sources, their relevance, and other sources that could initiate the threat events.
- FIND VULNERABILITY AND PREDISPOSING CONDITIONS
Task 3: Identify the predisposing conditions and vulnerabilities that impact the likelihood that concerned threat events result in adverse impacts.
- DETERMINE LIKELIHOOD
Task 4: Determine the possibility of concerning threat events resulting in adverse impact, taking into account:
- Nature of the threat sources that could initiate the threat events
- The predisposing conditions/vulnerabilities identified
- The organizational susceptibility
- DETERMINE IMPACT
Task 5: Determine the adverse impact from the concerned threat events taking into account:
- Nature of the threat sources that could initiate the threat events
- The predisposing conditions/vulnerabilities identified
- The organizational susceptibility
- DETERMINE RISK
Task 6: Determine the risk of the concerned threat events taking into account:
- The impact that would result from such events
- The likelihood of occurrence of events
Communicate and share results
The third step involves communicating the results and sharing the risk-related information. The objective is to ensure that the concerned decision-makers across the organization have enough risk-related information to make informed risk decisions.
The following tasks are involved to achieve that:
- Communicating the risk assessments results
- Sharing information generated in execution of the risk assessment to support other risk management activities
Let’s see how to communicate and share results using the tasks.
STEP 3:
COMMUNICATE RISK ASSESSMENT RESULTS
Task 1: Communicate the assessment results to the concerned decision-makers of the organization to support risk response.
SHARE RISK-RELATED INFORMATION
Task 2: Share the information produced during risk assessment with the concerned person.
4. Maintaining the assessment
The fourth and last step is to maintain an assessment for an organization. The objective is to keep current and specific knowledge of the risk the organization incurs.
To support the ongoing risk management decisions’ review, organizations keep and maintain assessments to incorporate any changes discovered through risk monitoring.
The risk monitoring process provides an organization with the means to:
- Find effectiveness of risk responses
- Find risk-impacting changes to the information system of the organization
- Verify compliance
While maintaining risk assessments, you need to carry out the following tasks:
- Keep an eye on risk factors identified during the risk assessment process and their possible impact on the organization.
- Update the components of the assessment reflecting the monitoring activities
STEP 4:
Let’s see how to maintain the risk assessment.
MONITOR RISK FACTORS
Task 1: Conduct an audit and monitoring of the risk factors that add up to the changes in the risk to the operations and assets of the organization.
UPDATE RISK ASSESSMENT
Task 2: Update the existing assessment using the results from the current monitoring of the factors.
Summary
To satisfy NIST 800 30, you must report the complete IT system of your organization. This includes the hardware and software; the data on all the systems; how sensitive that information is; who has access to the system, and the threat history of the system with the previous and current vulnerabilities.
Previous assessment plays a key role in understanding the vulnerabilities and assisting in with the current requirements. This whole exercise helps with understanding the weakness of the information system which one can use as a starting point to improve upon.
The following step is to understand the possibility of exploitation of information systems’ weaknesses by various cyber threats. Impact analysis can help understand the result of an event happening and the losses incurred.
Henceforth, to mitigate risks, one needs to create recommendations, and implementation plans This helps with reducing the likelihood of a threat and hence mitigating the risk impact of a cyber event.
All this might look like some intimidating tasks that are hard to implement. However, Cyvatar’s managed security services will not only help you with compliance with NIST CSF but also create a risk assessment and mitigation plan for your organization. You are just a message away. Get in touch.
