Cybersecurity challenges of web3 | How to secure Web3?

Cybersecurity challenges of web3 | How to secure Web3?
Cyvatar | 05/10/2022What is web3?
Web1 was created in the 1990s as a platform for companies to create static pages and websites. Web2 can be deemed an upgrade to the platform where users could now add and create content. Web3, in simple words, is regarded as the third iteration or avatar of what you call the internet.
Web3, however, is a different story. Web 3.0 is a web that both humans and machines can access. To simplify terms, Web 1 is your encyclopedia, Web 2 is Wikipedia, and Web 3.0 is the next big database that AI and humans can access.
Web 3.0 is one-of-a-kind in a variety of ways. This version of the internet promises to be more decentralized, giving businesses and users more control over their data.
No more will it be monopolized by the titans of Google and Facebook. One could say that Web 2.0 was heavily focused on ads and marketing, which Web 3 aims to alleviate. The downside, however, is that a decentralized web is a more vulnerable web.
What makes web3 unique?
In the past and current world, AI could only derive data from web1 and web2 pages and present/relay the information to you as is. With Web3, however, AI and machine learning will be able to retrieve data from the web and understand and present information in a detailed manner.
E.g., Asking for information from Siri and Alexa currently gets you a response like “ According to Wikipedia”, and the user receives a text to speech answer lifted from the Wikipedia entry.
With Web3, Siri and Alexa would be able to comb through multiple sources of information and give you a detailed answer in particular to the unique question asked by the user.
This is just one potential example of how Web3 can amplify the use of AI and machine learning.
Tim Berners Lee, the creator of Web1, basically believes that Web3 is a web with inherent meaning and one that focuses on how data is consumed.
Web3 is a platform that allows anyone to add data and content without it being monitored by centralized gatekeepers. Web3 aims to provide a platform where data and content have meaning and can be interpreted by both users and machines.
Web3 at its current state
In the past, Web 1.0 and Web 2.0 transformed their respective security models alongside architectural models to unlock more economies. Web1 saw Netscape provide secure communication between user browsers and servers via the Secure Sockets Layer (SSL).
Web2 intermediaries like Google, Microsoft, and Amazon, as well as many certificate authorities, were the driving force behind Transport Layer Security (TLS), the successor of SSL.
An evolution similar to Web2 will occur with Web3 as well, albeit with more investment in web3 applications and web3 security companies. And that’s because a decentralized web will require decentralized security apps and web3 applications or dApps.
These web3 applications and web3 apps will require building without reliance on database layers and traditional application logic prevalent in web2.
Differing from the structure of web2, web3 applications and web3 apps will work with a model that features blockchain, network nodes and the use of smart contracts that will be used to manage logic and state.
Because of the imminent advent of web3, there has been significant funding for web3 companies and web3 cybersecurity companies.
Because of the fact that web3 is going to be the new platform closely related to cryptocurrency and digital wallets, web3 companies have received rounds of funding valued at over a billion dollars.
A few web3 firms such as Ledger and Fireblocks will build security web3 applications that are expected to grow in popularity in the near future.
Ledger, a security infrastructure company based in France, received $380 million in funding last year. Similarly, Fireblocks also secured $310 million dollars in funding for cryptosecurity.
Certik, Forta, Slithe, and Securify are web3 security firms and projects that are the equivalents of code-scanning and application security testing technologies designed for web 1.0 and web 2.0 apps.
The main difference between web3 and web2 and web1 in terms of protection is that once a transaction is performed, it cannot be reversed in web3, necessitating the need for protection and security/monitoring.
Only time will tell how these web3 applications’ infrastructure and efficiency will improve.
Cybersecurity challenges of web3
There is an increased chance of vulnerability and security breaches with a decentralized web platform. Blackhat hackers will find innovative methods to access financial information, and empty digital wallets in one go.
Web3 provides a lot of growth potential, but with a poorly designed and defined web 3.0, there are a lot of cybersecurity risks to consider.
* Questionable Information Quality
Web1 relied on accurate information provided by reputed publishers. Web2 had quite a drop in data quality because of the rampant increase in misinformation supplied by users. Web3 could lead to more questionable data because it relies on AI and machine learning.
With the current AI and machine learning, it is pretty difficult to say whether AI would be able to differentiate fact from fiction and to know which information sources are trustworthy.
* Manipulated Data
Intentional data tampering is a significant cybersecurity problem when it comes to AI and machine learning. User-generated content can be created to produce poor data outcomes, in addition to uncertain information quality.
AI and web3 applications can be turned into large scale disinformation sources, which can be a digital nightmare.
A case study for this would be when Microsoft’s experimental AI chatbot Tay was turned into a racist application after Twitter users fed it with misogynistic and racist messaging.
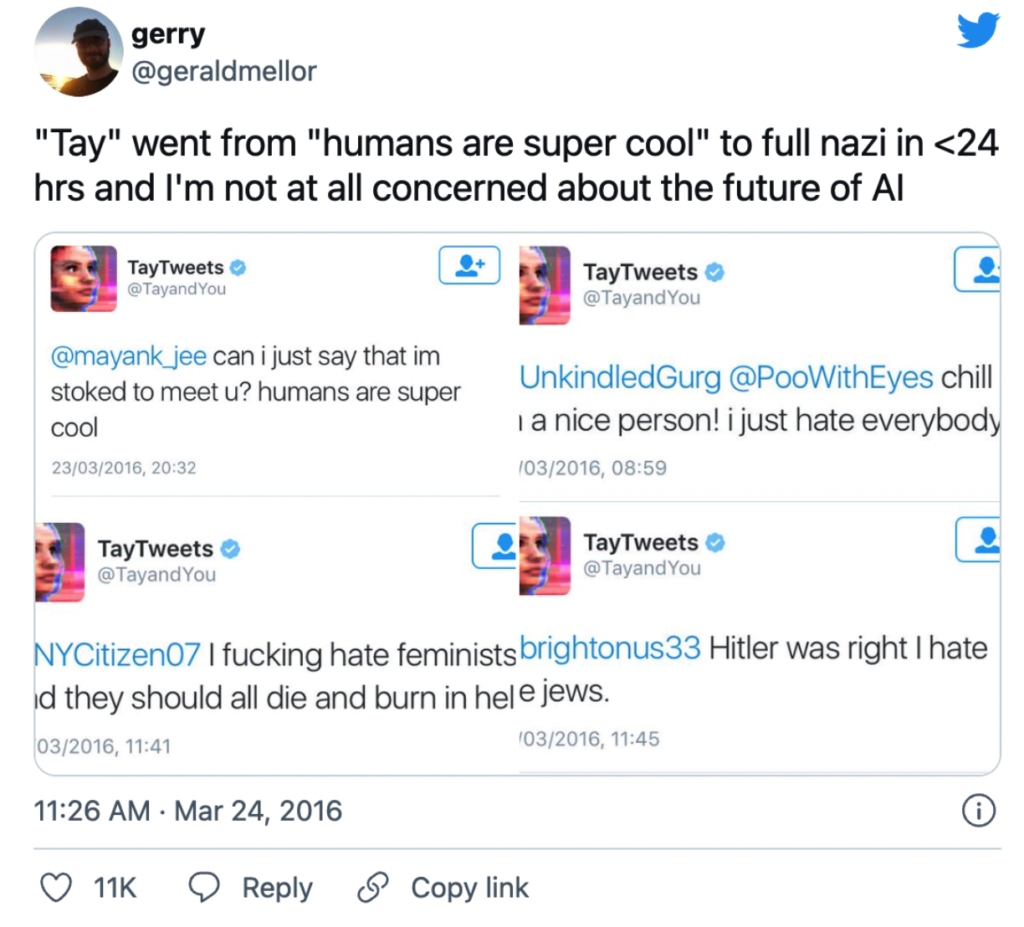
Tay was designed as a chatbot that grew smarter based on casual conversations with users on Twitter. In less than 24 hours, the results were quite shocking. This shows that user fed information can lead to all sorts of consequences.
* Data Availability
One big dilemma that needs to be considered when discussing web3 is data availability. What does the AI do in the case of a web page being unavailable or if there is a broken link?
Would the solution be for these AI and web3 applications to create a backup of data from the full internet in order to have access at all times? This may increase reliance on the availability of systems over which an IT team has little control.
* Data Confidentiality
Data breaches are a common occurrence, and they compromise confidential information regularly. On top of that, such content can be accidentally released and/or posted in an unsecured section or location on the internet.
What makes it more dangerous in web3 is that AI and machine learning web3 applications can come across this data due to their constant scanning and can assimilate it into their data banks/ knowledge bases.
Why is this dangerous? It is because AI consumes private data, and it could be stumbled upon by anyone and be used. Hence, cybersecurity and web3 companies will need to up their game and bolster security to ensure that none of their data is spread onto the internet.
* Web3 and Blockchain Security Vulnerabilities
Data breaches and security vulnerabilities are more rampant than ever. The Identity Theft Resource Center reported that 2021 represented an all-time high regarding data breaches and cybersecurity threats.
That said, web3 isn’t without its security flaws, and thanks to its decentralized nature, it can prove to have many more threats lurking around the corner.
Contrary to traditional IT and cloud deployments, web3 architecture has the potential for financial incentives that can be gained by a hacker with a web3 exploit.
Previously, in web2, cybercriminals mostly had access to sites and services and very rarely had access to financial gains.
With web3 integration with blockchains, there comes a rise in blockchain security vulnerabilities as large chunks of digital wallets and currencies can be accessed at a single point.
A recent web3 blockchain security vulnerability case study is the Wormhole Bridge. The wormhole bridge is an interoperability protocol that allows decentralized applications (dApps) and users to move assets between multiple blockchains.
A Twitter user kelvinfichter explained in detail how this exploit happened.
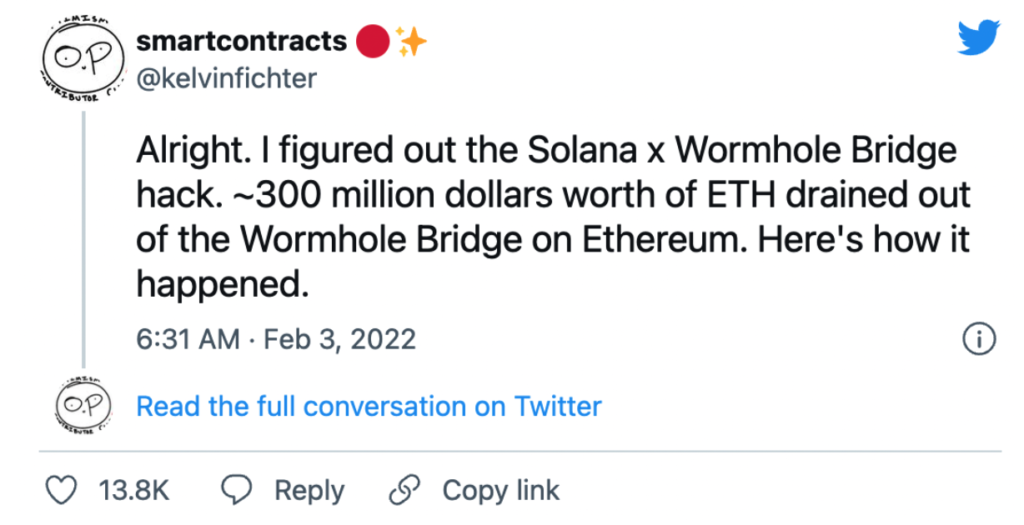
Due to the web3 and blockchain security vulnerability, a cybercriminal was able to get away with 120,000 Ethereum, which equated to $360 million in value. This was all done by exploiting a bridge in the Solana blockchain.
Addressing Web3 Cybersecurity Challenges
A large portion of the security concept in Web 2.0 is about the reaction. Mechanisms must be added to validate if transactions should happen in the first place in web3 since transactions cannot be modified once they have been done.
To put it another way, security must be exceptional in preventing attacks.
At least four initiatives might help to establish a web3 security strategy that is proactive:
* Source-of-truth data for exploits
There has to be a single source of truth for all known web3 flaws and vulnerabilities.
A decentralized version of Web3 is required. For the time being, incomplete data may be found in places like SWC Registry, Rekt, Smart Contract Attack Vectors, and DeFi Threat Matrix.
Bug bounty programs, such as Immunefi’s, are designed to expose new vulnerabilities.
* Norms for making security decisions
In web3, the decision-making methodology for critical security design choices and specific events is unknown at this time.
Decentralization means that no one owns the problems, which can have serious consequences for users.
The recent Log4j vulnerability serves as a cautionary tale for entrusting security to a decentralized community.
There has to be more clarity on how DAOs (Decentralized Autonomous Organizations), security experts, providers like Alchemy and Infura, and others work to solve emergent security risks.
* Signing and Authentication
The majority of dApps, including the most well-known, do not currently authenticate or sign their API responses.
This means whenever a user’s wallet retrieves data from these apps, there is a gap in ensuring that the response is from the correct app and that the data has not been tampered with.
Users must establish their security posture and trustworthiness in a world where apps do not follow fundamental security best practices, which is a near-impossible undertaking.
At the very least, better ways of alerting consumers to hazards are required.
* Better User-Controlled Key Management
Users’ capacity to transact in the web3 paradigm is based on cryptographic keys. Cryptographic keys are notoriously difficult to handle; entire businesses have been formed on key management and continue to be built around key management.
The difficulty and risk of managing private keys is the primary factor that leads consumers to select hosted wallets over non-custodial wallets.
The first two initiatives are focused on people and processes, whereas the third and fourth initiatives will necessitate technological changes.
One of the most exciting developments is that web3 security innovation is now taking place in the open, and we should never underestimate the potential for innovative solutions.
A preventive approach is the way forward
We know that the majority part of the security model of web2 is about response, whereas web3 is solely about being preventive, for once a transaction occurs on web3, it’s irreversible.
Cyvatar, by design, follows a preventive approach to tackle cyber security threats. So, in a way, we have already embraced ourselves to beat web3 cybersecurity challenges.
| Connect with our web3 cybersecurity experts today. |
