Writing Snort Rules with Examples and Cheat Sheet

Writing Snort Rules with Examples and Cheat Sheet
Cyvatar | 01/27/2022What are Snort Rules and their examples?
Let us get ample clarity upfront because, for all we know, the term Snort implies more than just one meaning.
In the business world, the Web and Cybersecurity, Snort refers to IDS– Intrusion Detection System. Because such detection helps you get proactive and secure the best interests of your business it is also known as IPS– Intrusion Prevention System.
If we drew a real-life parallel, Snort is your security guard. Snort Rules are the directions you give your security personnel. A typical security guard may be a burly man with a bit of a sleepy gait. With Snort and Snort Rules, it is downright serious cybersecurity.
By now, you are a little aware of the essence of Snort Rules. That should help when you imagine this scenario:
Your business is running strong, the future looks great and the investors are happy. All of a sudden, a cyber attack on your system flips everything upside down and now you wonder (/snort in anguish) What, Why, Damn! If only!
- “Why the **** with my goddamn business?!”
- “If only we had a proper Intrusion Prevention System in place!”
“Not me/ Not with my business” is such a common, deceptive belief with so many of us. In the same vein of ambiguity, many of us may still wonder if we need to know what Snort Rules are at a deeper level.
Well, there is no way out.
We know there is strength in numbers. But man, these numbers are scary!
In 2021, on average, there were 2200 cyber-attacks per day (that’s like an attack every 39 seconds!).
Before we discuss the snort rule with examples, and the different modes in which it is run, let us lay down the important features.
Important Features of a Snort Rule
Trigger Alerts
Alerting a malicious activity that could be a potential threat to your organization, is a natural feature of a snort rule. Crucial information like IP Address, Timestamp, ICPM type, IP Header length, and such are traceable with a snort rule.
There are multiple modes of alert you could generate: Fast, Full, None, CMG, Unsock, and Console are a few of the popular ones. Each of which is unique and distinct from one another.
For instance, if you need a full report that includes comprehensive details, the rule would look like the following:
Output alert_full: alert.full
And suppose you need a quick report that doesn’t need to be as elaborate as the full report, you could choose to get it with the following rule
Output alert_fast: alert.fast
Flexible Usage
As may be evident from the above examples, a snort rule is a single line code that helps to identify the nature of traffic. However, modern-day snort rules cater to larger and more dynamic requirements and so could be more elaborate as well.
Also, once you download Snort Rules, it can be used in any Operating system (OS). There is no limitation whatsoever. Be it Linux, Unix, Windows, Ubuntu or whichever for that matter, Snort secures your network just the same.
Since it is an open-source solution made to secure businesses, you may download it at no cost whatsoever. Just in case you needed the link to download:
Identifies Fraud
Snort is the most popular IPS, globally speaking. The open-source IDS – Intrusion Detection System helps to identify and distinguish between regular and contentious activities over your network.
Snort Rules refers to the language that helps one enable such observation.
It is a simple language that can be used by just about anyone with basic coding awareness.
It combines 3 methods to detect a potential cyber fraud:
Method #1
Signature: Signature-based IDS refers to the identification of data packets that have previously been a threat.
It identifies historic patterns or popular and malefic sequences and detects the same when a similar event is on the cards.
Method #2
Protocol: In this method, Snort detects suspicious behavior from the source of an IP – Internet Protocol.
Every computer has a unique IP and the data that is sourced from a distrustful IP is detected and notified in real-time.
Besides high-level protocols like HTTP, Snort detects skeptical user behavior from 3 types of low-level Protocols – TCP, UDP, and ICMP.
Apparently, we may even be able to analyze data packets from different sources like ARP, IGRP, GRP, GPSF, IPX in the future.
Method #3
Anomaly-based Inspection: There is a palpable difference between Signature/ Protocol-based IDS and Anomaly-based inspection.
While the other 2 rely on previous or historic behavior, Anomaly-based IDS detects and notifies of any type of behavior that can be viewed with a veil of suspicion.
Suspicious activities and attempts over Operating System (OS) Fingerprints, Server Message Block (SMB) probes, CGI attacks, Stealth Port Scans, Denial of Service (DoS) attacks etc are negated instantly with Snort.
We have touched upon the different types of intrusion detection above. It would serve well to be aware that Snort rules can be run in 3 different modes based on the requirements:
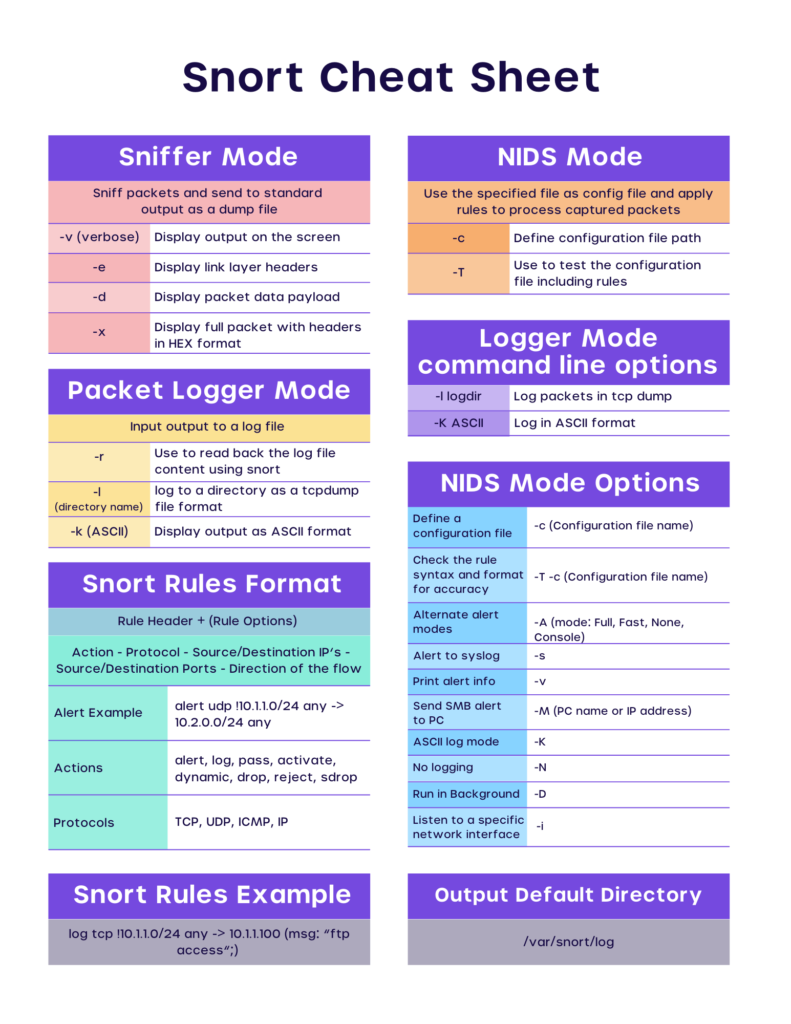
3 Modes of Snort: Sniffer, Logging and NIDS
- Sniffer Mode: Sniffer mode helps with your IDS objectives in the following instances if:
- You only need to print out data: ./snort -v
- There is a need to see the data in transit and also check the IP and TCP/ICMP/UDP headers: ./snort -vd
- You need slightly elaborate information about data packets: ./snort -vde
- To list the command lines exclusively: ./snort -d -v -e
- Logging Mode: Just like the term ‘logging’ implies, when you need to log/record the data packets you may designate a logging directory. Understandably, the data packets are recorded in the directory.
Here’s the line that logs the data in an assumption that you have created a directory called ‘log’ : ./snort -dev -l ./log -h 192.168.1.0/24
- Network Intrusion Detection System (NIDS) Mode: When you/ or your network administrator is specific about logging a specific kind of data packet/s, you may run Snort in NIDS mode. You may also define the action you want to take upon detection of malicious data packets while you write the rule.
Now that we are aware of the essence of Snort rules and their modes, let’s get down to writing them. If you are a coder, please excuse the over-simplification. If you are a novice in this subject, you are welcome, hey!
Writing Snort Rules | Examples and Cheat Sheet
We are getting closer to understanding what snort rules are and their examples. So far so good with understanding the essence, features, and the different modes of Snort.
Frankly speaking, the examples and the cheat sheet to write snort rules that we will have later is why we are having this conversation in the first place.
However, doing so without getting familiar with these terms would be somewhat like playing basketball without knowing how to dribble the ball. So here it goes:
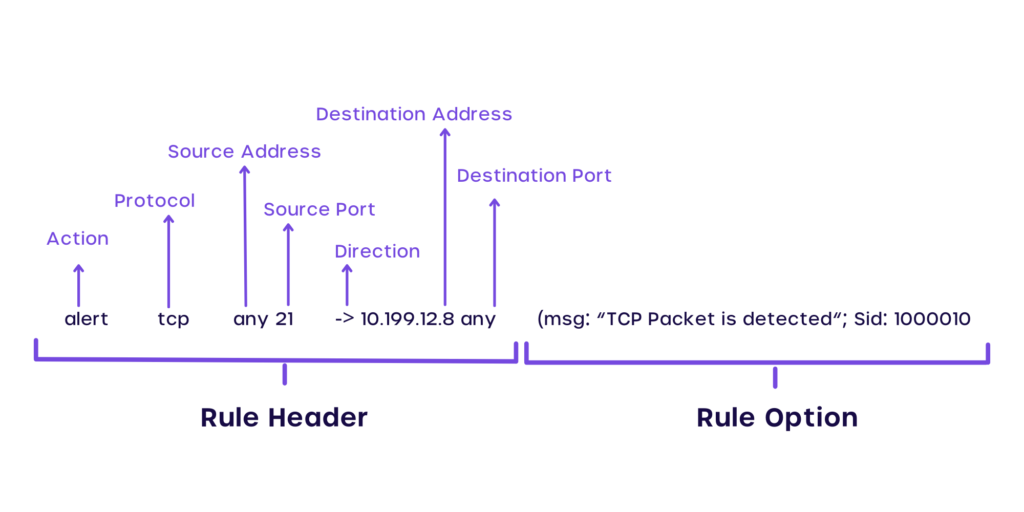
Rule Header
- Rule Action: There are 5 rule actions by default while you run a typical Snort rule: Alert. Dynamic, Pass, Log, or/and Activate. The most common rule action is ‘alert’ which understandably alerts the network administrator upon detecting a potential threat.
- Protocol: As discussed previously, the protocol is the unique address of a computer. While writing the rule, you may key in the Protocol address that you need to be wary of gathered from previous mishaps / historical data.
- Source IP Address: Let’s assume that your threat is from Mr Jack. The IP address or in some cases, his network ID is the source IP address. In case you need to get alerts from any and every source, you may just key in ‘any’ in this particular part of the rule.
- Source Port: This is like the facilitator that communicates messages between two or more computer networks. Computers generally have 65,536 TCP Ports and if you wish, you may again key-in ‘any’ to define all such ports in the rule.
- Flow: In Snort Rules, flow refers to the direction of the traffic. This keyword/symbol helps us apply rules only to the specific parts of the traffic. It is denoted with the arrow (</>) symbol.
- Destination IP Address: Where do the network packets from Source IP address channeled through Source Port and Destination Port go to? No prizes for guesses. They go to the Destination IP Address. So obvious, isn’t it?
- Destination Port: Just like the source port which facilitates communication between the source ports, the Destination port does the same with Destination TCP/ UDP.
Options
Popular ‘options’ include Content, Offset, Content-List, Flags etc. Each of these options is entered towards the end of the rule line and largely defines the essence and the output derived from the rule.
Now, please believe us when we say, we are ready to write the rules!
We talked about over-simplification a few moments ago, here’s what it was about. This reference table below could help you relate to the above terms and get you started with writing ‘em rules.
| Rule Header | Options | ||||||
|---|---|---|---|---|---|---|---|
| Rule Action | Protocol | Source IP Address | Source Port | Flow | Destination IP Address | Destination Port | Message |
| alert | top | any | 21 | > | 10.199.12.8 | any | (msg: “TCP Packet Detected” nd: 1000:610) |
For the uncomplicated mind, life is easy. Why should writing Snort rules get you in a complicated state at all? Just why!
After such a scintillating 🙃 tour de Snort, you could be keen and ready to download Snort right away and rock the keyboard. Well, you are not served fully yet. Here’s the real meal and dessert.
Snort Rules Examples and Cheatsheet
Case 1: Securing Email Server With Snort Rules:
alert tcp 192.168.1.0/24 any -> 131.171.127.1 25 (content: “hacking”; msg: ”malicious packet”; sid:2000001;)
Case 2: Detecting TCP SYN Floods
Alert tcp any any -> 192.168.10.5 443 (msg: “TCP SYN flood”; flags:!A; flow: stateless; detection_filter: track by_dst, count 70, seconds 10; sid:2000003;)
Case 3: Securing your Network against Conficker A Worm
alert tcp any any -> any 445 (msg: “conficker.a shellcode”; content: “|e8 ff ff ff ff c1|^|8d|N|10 80|1|c4|Af|81|9EPu|f5 ae c6 9d a0|O|85 ea|O|84 c8|O|84 d8|O|c4|O|9c cc|IrX|c4 c4 c4|,|ed c4 c4 c4 94|&<O8|92|\;|d3|WG|02 c3|,|dc c4 c4 c4 f7 16 96 96|O|08 a2 03 c5 bc ea 95|\;|b3 c0 96 96 95 92 96|\;|f3|\;|24|i| 95 92|QO|8f f8|O|88 cf bc c7 0f f7|2I|d0|w|c7 95 e4|O|d6 c7 17 f7 04 05 04 c3 f6 c6 86|D|fe c4 b1|1|ff 01 b0 c2 82 ff b5 dc b6 1b|O|95 e0 c7 17 cb|s|d0 b6|O|85 d8 c7 07|O|c0|T|c7 07 9a 9d 07 a4|fN|b2 e2|Dh|0c b1 b6 a8 a9 ab aa c4|]|e7 99 1d ac b0 b0 b4 fe eb eb|”; sid: 2000002; rev: 1;)
Case 4: Alerts of Buffer Overflow in BIND
alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg:”FTP wuftp bad file completion attempt [“;flow:to_server, established; content:”|?|”; content:”[“; distance:1; reference:bugtraq,3581; reference:bugtraq,3707; reference:cve,2001-0550; reference:cve,2001-0886; classtype:misc-attack; sid:1377; rev:14;)
Case 5: Preventing Bug Bear Variants and Content Generalization
alert tcp any any -> any any (msg:Possible BugBear B Attack FuzzRuleId cor(\’||?| 63 e7|\’); content:||?| 63 e7|; regex; dsize:>21;) alert tcp any any -> any any (msg:Possible BugBear B Attack FuzzRuleId cor(\’|3b |?| e7|\’); content:|3b |?| e7|; regex; dsize:>21;)
alert tcp any any -> any any (msg:Possible BugBear B Attack FuzzRuleId cor(\’|3b 63 |?||\’); content:|3b 63 |?||; regex; dsize:>21;)
Case 6: Generalization by Rule Inversion
alert udp any any -> any 69 (msg:TFTP GET Admin.dll; content: |0001|; offset:0; depth:2; content:admin.dll; offset:2; nocase; classtype:successful-admin; reference:url, www.cert.org/advisories/CA-2001-26.html; sid:1289; rev:2;)
alert udp any any -> any 69 (msg:TFTP GET Admin.dll; content: |0001|; offset:0; content:admin.dll; offset:2; nocase; classtype:successful-admin; reference:url, www.cert.org/advisories/CA-2001-26.html; sid:1289; rev:2;)
Now, No Snorting
There are thousands of stock rules and so many more you can write depending on the need and requirements of your business. Shall we discuss them all right away? Or, figure out the ones which could save you the M?
By the way, If numbers did some talking within context…(source: welivesecurity)
- The average cost of a data breach in 2021 was $4.24 million, the highest in 17 years.
- Phishing attacks affected 36% of the breaches while Social Engineering accounted for close to 70% of the breaches in public administration.
- Kaseya, an IT Management company, was demanded a whopping $70 million in ransomware fee in July 2021.
Simple things like the Snort itself for example goes such a long way in securing the interests of an organization. So many organizations with hundreds and thousands of years of collective human capital have gone down to dust due to the treachery of cyber fraud in the recent past.
Perhaps why cybersecurity for every enterprise and organization is a non-negotiable thing in the modern world. Coming back to Snort, it is an open-source system which means you can download it for free and write the relevant rules in the best interest of your organization and its future.
| Need Help With Snort? Talk to our CyberSecurity Expert |
