What is Mitre ATT&CK | Understanding MITRE ATT&CK framework

What is Mitre ATT&CK | Understanding MITRE ATT&CK framework
Cyvatar | 01/21/2022If you have to fight a formidable and persistent foe, what do you do?
First, you identify the enemy and then try to understand the enemy. You figure out what the enemy is doing, what is their thinking, what is their behavior looking like, what tactics they use, how they mount their attacks, etc. Then you develop a plan to defend yourself against such enemies.
It is the same with cybersecurity. And this is where MITRE ATT&CK comes into the picture.
It gives you more and better information about the ways, means, and methods used by cyber attackers to better defend your organization far more successfully against them.
Understanding MITRE ATT&CK Framework
First developed by MITRE, a government-funded organization, in 2013, MITRE ATT&CK is a ”globally accessible knowledge base of adversary tactics and techniques based on real-world observations.”
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. It includes detailed descriptions of the following:
- Tactics (the various technical objectives)
- Techniques (the various methods used)
- Common knowledge (how the techniques are employed) by the various cyber attacker groups known as Advanced Persistent Threat (APT) Groups
The MITRE ATT&CK framework also gives you detailed information about the following:
- Various APT Groups
- Provides suggestions for detection and mitigation for specific techniques
- Gives an extensive list of software used in the attacks
It provides a common language for the defenders to describe and understand the behavior and activities of the threat actors.
Unlike other threat models like STRIDE, PASTA, OCTAVE, and Lockheed Martin’s Cyber Kill Chain, MITRE ATT&CK is different in the sense that it looks at cyber defense from the perspective of an attacker. By deliberately taking the attacker’s viewpoint, it helps organizations to understand how threat actors think, prepare for and execute the attacks.
As the Chinese philosopher and military strategist Sun Tzu said, “To know your enemy, you must become your enemy”.
All the information contained in the ATT&CK is collected from publicly available data sources and from professionals who are dealing with cyber attacks every day.
It is a free tool available to organizations of all sizes in the private sector, public sector, and the government and is widely used by cybersecurity professionals, penetration testers, Red Teams as a foundation for developing their own threat models and defense plans.
An Overview Of The Mitre ATT&CK Framework
Managing cybersecurity is a difficult task. After all, the attackers have to just exploit that one vulnerability to breach your network. But, as defenders, you need to secure everything.
So, detection of threats and responding to them becomes vital.
MITRE ATT&CK framework provides a common language and a tool for different groups within an organization to share information, work together, and put in place the necessary detection and response systems.
Cyber attackers set out to achieve specific goals and use various ways and means to achieve them.
These are collectively known as Tactics, Techniques, and Procedures or Common Knowledge. In short, TTPs.
- Tactics describe what objectives the attackers are trying to achieve. For instance, gaining access to a network, or maintaining that access, or establishing command and control over the victim’s network or digital assets.
Attackers use several tactics to mount an attack successfully.
- Techniques are the various methods used by attackers to achieve their tactics. Attackers may use multiple techniques to achieve their tactics.
- Common Knowledge or procedures describe how these tactics and techniques are implemented. For instance, malware, ransomware, or any other tool used.
The MITRE ATT&CK framework is built around this knowledge base of known tactics, techniques, and procedures and is organized in the form of a matrix.
It visually arranges them in a format that can be easily understood. The tactics are arranged in rows and techniques in columns.
MITRE ATT&CK Matrices
Attackers may approach each of their targets differently. For instance, they may use different TTPs to attack corporations or enterprises than for attacking mobile devices or industrial control systems.
The MITRE ATT&CK framework provides three separate matrices for dealing with each of these contexts.
| Enterprise ATT&CK | Mobile ATT&CK | Pre-ATT&CK |
|---|---|---|
| It addresses adversarial behavior on platforms like Windows, macOS, Linux, cloud, and network environments. | Describes the tactics, techniques, and procedures used to infiltrate mobile devices based on the NIST Mobile Threat Catalogue. It addresses both iOS and Android. | This matrix focuses on activities performed before an attack. It helps security professionals to understand how attackers perform Reconnaissance and plan their attacks. |
The latest version of the Enterprise ATT&CK matrix has 14 tactics listed in a logical sequence indicating the different phases of an attack. They are:
- Reconnaissance: Gathering information in preparation for an attack.
- Resource development: Creating, compromising, stealing, or buying necessary resources for mounting an attack.
- Initial Access: Gaining access to the victim’s network systems.
- Execution: Running malicious code on the compromised network or system.
- Persistence: Maintaining access to the network or system.
- Privilege Escalation: Attempts to gain further access and privileges.
- Defense Evasion: Avoiding detection.
- Credential Access: Trying to steal account names and passwords.
- Discovery: Putting together information about the compromised environment.
- Lateral Movement: Moving from one system to another within a compromised environment.
- Collection: Gathering data to mount a higher-level attack.
- Command and Control: Establishing control over the systems in the victim’s network.
- Exfiltration: Stealing victim’s data/ confidential information.
Impact: Making data, system, or networks inaccessible to the victim through damage, destruction, or denial.
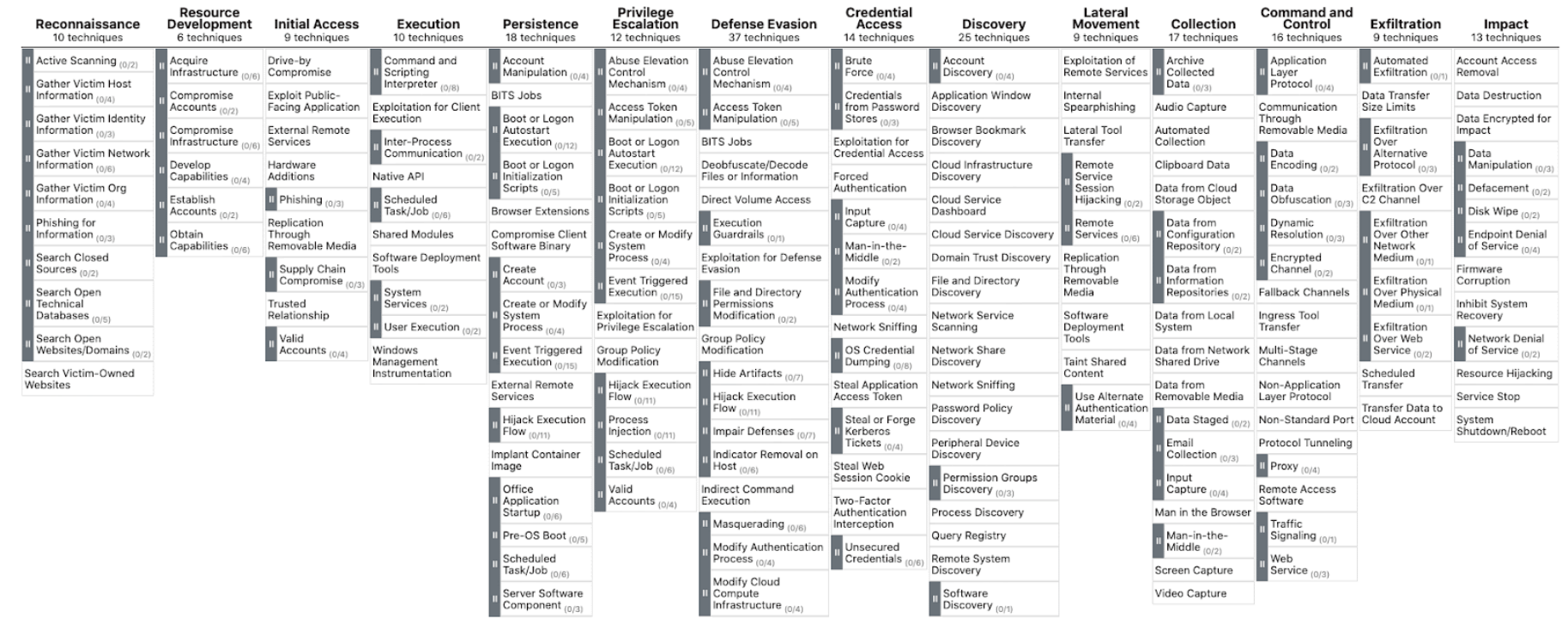
There are about 205 techniques and 379 sub techniques listed in this matrix.
Exploring The ATT&CK Matrices
The matrices provide a wealth of information with regard to the attacker’s tactics, techniques, and procedures.
Tactics like Reconnaissance, Resources Development, or Initial Access (there are 14 of them) are named at the top and below each of them are listed the various techniques and sub techniques.
Each technique is given an ID number and a description as well.
When you click on the tactic name, a detail page opens up giving you a general description of the tactic and a list of all the techniques and sub techniques used for that tactic.
When you click on the technique name, a similar details page opens up giving you a description of the technique and listing the sub techniques.
The tactics to which this technique belongs, the platforms for which this technique is applied, data sources that can be used to identify the activity, etc.
Below the description, a list of procedures, and how different APT groups have used this particular technique, ways to detect their use, and mitigations available are also given.
Sub techniques can also be explored in a similar way.
The ATT&CK matrix does not stop at just providing detailed information about the tactics, techniques, and procedures.
It provides you with additional information and resources on:
1. DATA SOURCES
These are information that can be collected by sensors/logs that are important for detecting a given attack technique or a sub technique.
The matrix lists 38 data sources.
2. APT GROUPS
ATT&CK is considered to be one of the most comprehensive and reliable sources of information on threat groups in the public domain.
It provides detailed information about the groups, both known as well as suspected ones and the specific tactics, techniques, and procedures used by particular groups.
The latest version of the MITRE ATT&CK matrix lists 129 APT groups.
3. SOFTWARE
It is a commercial or custom code, open-source software, or other tools used by threat actors.
It includes techniques that are mapped to various groups who have used such software.
The matrix lists 637 software with brief information about each of them.
4. MITIGATIONS
The ATT&CK matrix is not just about the tools of the trade used by the attackers. It also equips you with information on how to mitigate these attacks.
They are the security concepts, tools, and technologies that can be used to prevent a technique or a sub technique from being employed successfully against your enterprise.
There are 43 enterprise att&ck and 13 mobile att&ck mitigations listed in the matrix.
Benefits of Adopting MITRE ATT&CK
Here is how organizations benefit from implementing the MITRE ATT&CK.
- Adversary Emulation: It can be used to create scenarios that emulate adversary behavior to test your defenses.
- Red Teaming: To create Red Team plans (testing an organization’s cyber security defenses by identifying vulnerabilities in the system and launching an attack exploiting those vulnerabilities).
- Behavioral Analysis: ATT&CK can be used to build behavioral analytics for detecting the behavior of the adversary.
- Defensive Gap Assessment: The ATT&CK matrix can be used to assess monitoring and mitigation tools for defenses already deployed within an enterprise.
SOC Maturity Assessment: It can be used to measure how good the SCO (Security Operations Center) is at detecting, analyzing, and responding to an attack.
Other Tools & Resources
Here are a few resources that help you utilize the ATT&CK framework and derive maximum advantage from it.
- ATT&CK NAVIGATOR: It is a free tool that helps you map your defense tools and measures to attack techniques. These can be defensive measures, preventive measures, or attacker behavior. It can be used online or can be downloaded for more permanent use.
- MITRE CYBER ANALYTICS REPOSITORY: It is a large data set of analytics developed by MITRE based on its ATT&CK adversary model.
- CALDERA: It is an open-source network security framework for emulating attacks and automated responses.
It provides an automated Red team that can reduce the resources needed for routine testing and thereby utilize those resources for addressing more critical issues.
- ATOMIC RED TEAM: It is a library of simple tests that are conducted to test the cyber defenses of an organization. These tests are well structured, focused, and can be automated.
- RED TEAM AUTOMATION: An open-source tool that can simulate malicious behavior based on the tactics and techniques in the MITRE ATT&CK. It can simulate more than 50 tactics.
Challenges Faced By CISOs In Adopting The Mitre Att&Ck Framework:
The benefits of the MITRE ATT&CK frameworks are obvious. But, according to a study by the Center for Longterm cybersecurity at the University of California, Berkely-
- Less than 50% of the CISOs, CIOs and other cybersecurity professionals of large and medium-sized enterprises are confident of fully detecting all the techniques in the ATT&CK matrices.
- The biggest challenge with the implementation of the ATT&CK framework is the lack of interoperability with the security products. Many find it challenging to map the events to tactics and techniques.
- A large number of enterprises could not correlate events from the cloud, networks, and endpoints to investigate threats.
Be the PRO with Cyvatar
Staying one step ahead is for amateurs; staying two leaps ahead is for pros. Adopting MITRE ATT&CK Framework is the first step toward that direction.
With Cyvatar’s managed cybersecurity solutions, you are always a message away from being a cyber-pro organization. Be the PRO with Cyvatar, contact our cyber expert now, and get to know how we fully manage cybersecurity for SMBs and enterprises.
| Learn how you can reduce the burden of hiring cybersecurity professionals with Cyvatar’s managed cybersecurity services. GET IN TOUCH |
