Cybersecurity Policies
Streamline Your Cybersecurity with Ready-to-Use, Customizable Policy Templates
Why continue paying for cybersecurity policies when the future of streamlined security compliance is here at Cyvatar? Access our comprehensive suite of 34 ready-to-implement policy templates, each pre-customized with your company’s name. These templates are designed to ensure compliance with industry standards and foster a secure organizational culture, all at no cost to you under our freemium model.
Tailored for Immediate Implementation
Our policy templates offer immediate benefits by streamlining the complex process of establishing and maintaining robust cybersecurity measures. They are crafted to help you enforce rigorous, up-to-date security protocols tailored to your business needs.
List of Available Policies
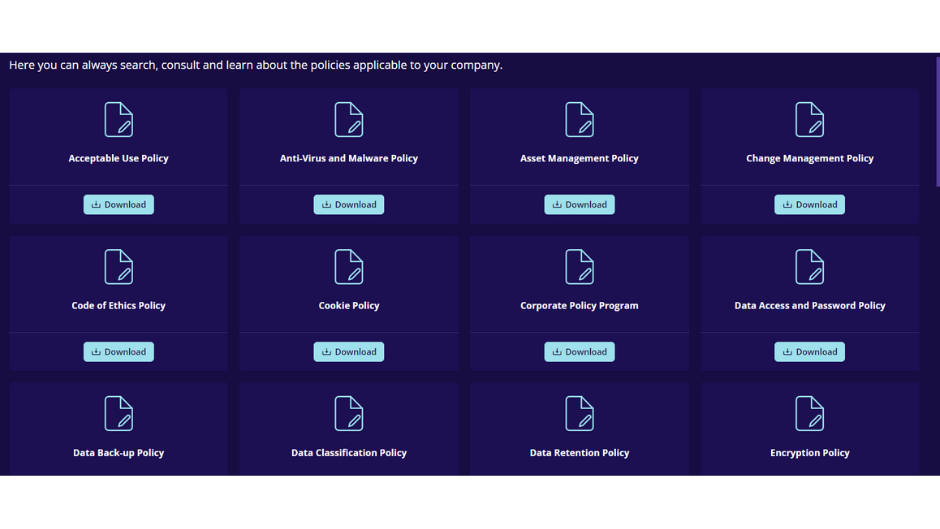
Here is a clear, structured view of all the cybersecurity policy templates we offer:
| Category | Policy Name |
|---|---|
| General Security Policies | Acceptable Use Policy |
| Anti-Virus and Malware Policy | |
| Asset Management Policy | |
| Change Management Policy | |
| Code of Ethics Policy | |
| Corporate Policy Program | |
| Data Management Policies | Data Access and Password Policy |
| Data Back-up Policy | |
| Data Classification Policy | |
| Data Retention Policy | |
| Encryption Policy | |
| Facility and HR Policies | Facility Security Policy |
| HR Corrective Action Procedure | |
| Human Resource Security Policy | |
| Risk and Incident Management | Information Security Committee Policy |
| Information Security Risk Assessment Policy | |
| Security Incident Response Policy | |
| Compliance and Legal | Interconnection Agreement Policy |
| Privacy Policy – External | |
| Privacy Policy – Internal | |
| Service Provider Security Policy | |
| Technical and System Policies | Logging and Monitoring Policy |
| Perimeter Security and Administration Policy | |
| Software Development Policy | |
| System Configuration Policy | |
| Vulnerability Identification and System Updates Policy | |
| Telecommuting Policies | Telecommuting Assignment |
| Telecommuting Policy | |
| Telecommuting Self-Certification Safety Checklist | |
| Policy Management | Policy or Standard Exception Request Form |
| Policy or Standard Exception Request Procedure | |
| Policy or Standard Variance Request Form | |
| Policy or Standard Variance Request Procedure |
Why Choose Cyvatar?
Choosing Cyvatar means you’re partnering with a leader in cybersecurity innovation. Our freemium offerings are not just about saving costs; they’re about empowering your organization with the tools and knowledge to protect itself effectively. Join us and step into the future of cybersecurity, where your protection is guaranteed and compliance is simplified.
