Secure Endpoint Management Plus (SEMP)
for Your Business
Next-generation AI antivirus solutions designed to prevent cybersecurity compromise

What SEMP Looks Like
- Understand your IT assets and endpoints
- Make sure the next-generation endpoint solution is installed and updated on every single endpoint
- Configure and block ransomware and other malicious attacks
- Maintain your preventative state
- Monitor 24/7
Are you ready to proactively secure your endpoints?
In cybersecurity, detecting and responding to threats simply doesn’t work, especially in a ransomware scenario. Once an incident has been detected, it’s already too late.
Ransomware is increasing because it works. Most companies are misconfigured on the endpoint, which allows ransomware to execute–the result of a flawed, reactive strategy of detecting and responding to threats.
No cybersecurity company can promise you won’t get hacked, but they should offer measurably better security and next-level antivirus solutions that will configure your environment to a preventative state that effectively stops endpoint compromise. A secure endpoint management plus solution will then maintain your locked down and preventative state so that you don’t have to deal with ransomware or any other malware-based attack.
Are You Managing Secure Endpoints?
Don’t let this happen to your company. Stop relying on a detect-and-respond mentality that allows ransomware to continue attacking your data assets.
By using the power of next generation AI software, as well as continuous management, you’ll effectively stay in a locked down and preventative state, protecting you from endpoint breaches.
You Need a Digitized Solution for a Digital Age
The Old Age
For years, cybersecurity experts have used signature-based technology to keep clients safe from malicious attacks.
However, this solution has long been understood by the hacker community and is now easily bypassed.
Even companies who use AI antivirus solutions aren’t necessarily using it effectively to help maintain your company’s cybersecurity in a locked down preventative state.
Are you susceptible to downtime resulting from unsecured endpoints? ›
The Digital Age
Continuously managed AI antivirus software is the way of the future. Configuring that software to manage and maintain secure endpoints, combined with 24/7 monitoring for attacks, gives your organization the highest level of protection.
With this solution, your company can be brought to a proactive, preventative, and locked down state, which won’t disrupt your business operations.
Learn how Cyvatar provides the most secure solution with proactive endpoint management. ›

Your Endpoint Security Problem
When there’s a data breach, there’s downtime. And that’s simply not good for business.
The obsolete detect-and-respond method does little to scan proactively for malware and can do nothing at all for ransomware attacking your endpoints and assets. While hacks will happen, they currently cause downtime for your company; and downtime means lost customers.
You’re risking downtime and lost customers — and therefore lost revenue — with ineffective endpoint security management.
Your Cyvatar Solution
Cyber attacks no longer have to mean downtime for your organization.
With Cyvatar’s Secure Endpoint Subscription, our powerful AI solutions can transition you to a locked down and preventative security state. That way, the antivirus system can block any new and malicious threats that come along.
By implementing next-generation security systems, Cyvatar can clearly demonstrate the impact of our secure endpoint solution, including drastic preventative score improvements. Then, if and when a hack occurs, you can rest comfortably knowing that the threat will be remediated immediately so you won’t lose any business during the breach.
People. Process. Technology.
When you work with Cyvatar, you get cybersecurity-as-a-service with more robust people, process, and technology than you get anywhere else.
That means not only best-of-breed technology, but the best people to put it in place and the right process to keep your cybersecurity solution running smoothly.
Cyvatar encompasses people, process, and technology in one incredible package.
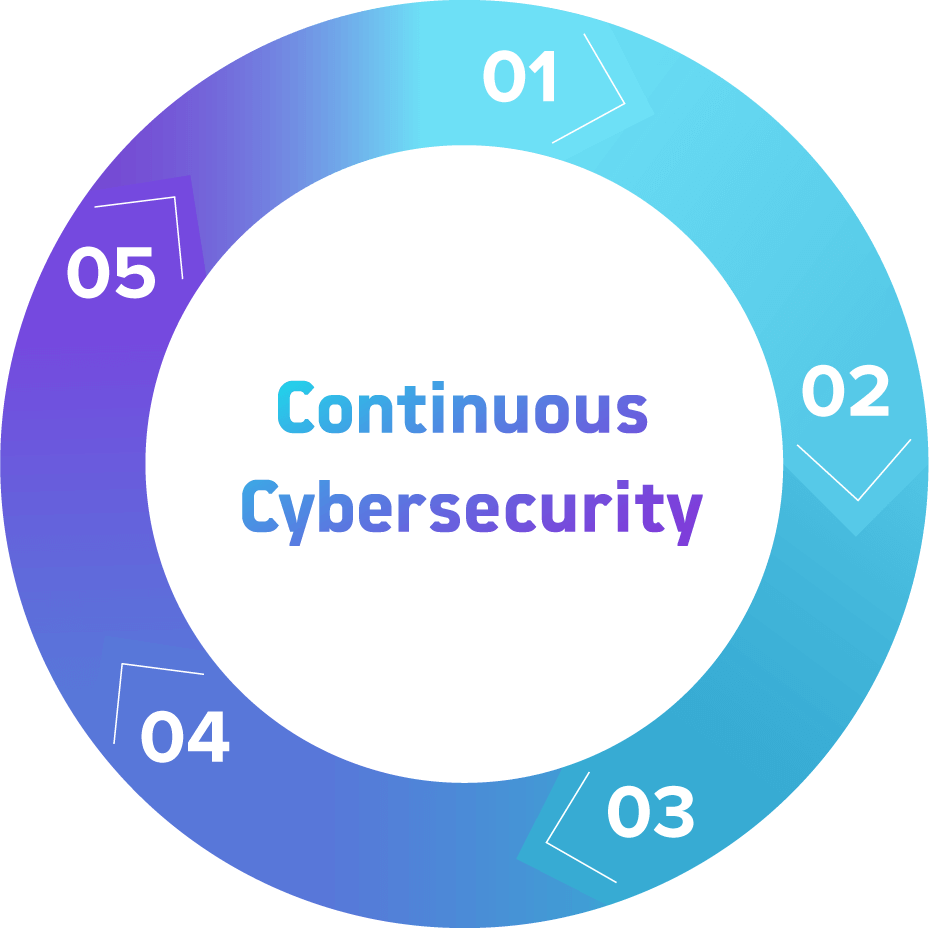
Cyvatar’s ICARM Methodology
- Installation
The solution is implemented and installed. - Configuration
The technology is configured properly. - Assessment
An assessment is performed to identify risks. - Remediation
Remediation of the risks that were identified is performed. - Maintenance
Continuous maintenance and monitoring with monthly exclusive reporting. Repeat.