Privileged Access Management (MPAM) For Your Business
your company’s data

You don’t allow users to have direct access to applications and you require multi-factor authentication. That’s a great start, but it’s not enough to protect your most critical assets.
Hackers can move deep within your company’s data through a single login using lateral movement. This technique is used in the majority of attacks and that’s why it’s critical to control the accounts that have access, when they have access, and how they have access.
When lateral movement occurs, attackers quickly jump from one system to the next, giving them access to more data and penetrating your network before you notice.
and secure your business systems.
Are you managing access properly?
Don’t let this happen to your company. Drastically reduce data breaches as a result of privileged access with Cyvatar’s managed cybersecurity solution.
You Need a Digitized Solution for a Digital Age
The Digital Age
Focus on successful logins and anomalies.
Learn how Cyvatar provides the most secure solution with cybersecurity for privileged access ›

Your Privileged Access Problem
Sophisticated hackers can easily penetrate your network without proper privileged access management.
Many users commonly use the same username and password in every application, leaving your business vulnerable to threats. It only takes one successful login from an intruder to instantaneously gain deeper access to your network.
On top of all this, you also have compliance requirements.
The biggest problem of all? You’re not assuming hackers already have your passwords; they do or they can get them.
Your Cyvatar Solution
If you’re not secured properly, highly privileged credentials can be used by attackers to steal sensitive information and compromise your systems. Additionally, compliance regulations — such as GDPR, HIPAA, and ISO/IEC27002 — are required.
We’re always keeping an eye on your data and who has access to it, and that’s CyValue: Installation, Configuration, Assessment, Remediation, and Maintenance (our ICARM Methodology).
People. Process. Technology.
When you work with Cyvatar, you get cybersecurity-as-a-service with more robust people, process, and technology than you get anywhere else.
That means not only best-of-breed technology, but the best people to put it in place and the right process to keep your cybersecurity solution running smoothly. Cyvatar encompasses people, process, and technology in one amazing package.
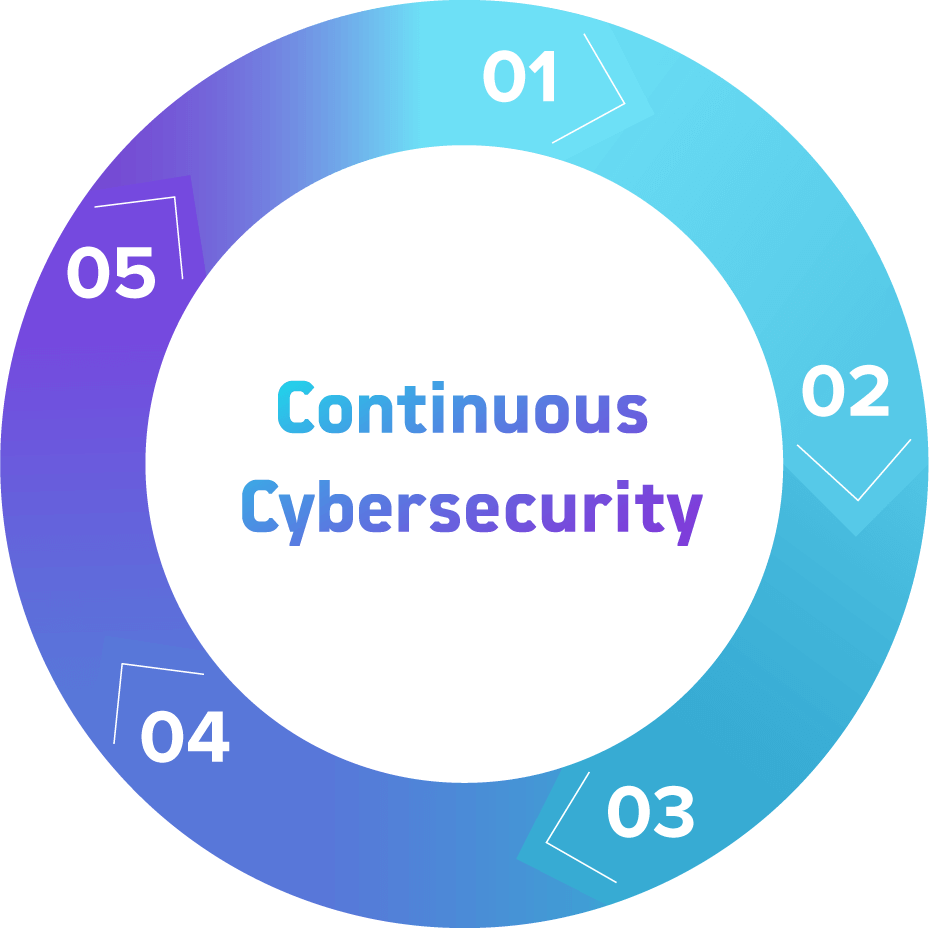
Cyvatar’s ICARM Methodology
1. Installation
The solution is implemented and installed.
2. Configuration
The technology is configured properly.
3. Assessment
An assessment is performed to identify risks.
4. Remediation
Remediation of the risks that were identified is performed.
5. Maintenance
Continuous maintenance and monitoring with monthly exclusive reporting. Repeat.
How Does Your Privileged Access Management Measure Up?
Let’s talk and we’ll help you find out.
What’s your info?