IT Asset Management (ITAM) For Your Business
digital assets continuously
What’s the best way to secure your assets?
Take inventory of the assets you have, then build security around them. That way, you won’t wonder what you have or if your IT assets are secured. After all, you can’t secure what you don’t know you have.
But guess what most companies aren’t doing?
Taking inventory of the assets they have.
Asset inventory is your first cybersecurity building block.
What’s an asset exactly?
An asset can be a multitude of things; it’s more than just laptops. An application, a data source, a business unit, cloud instances, and operational infrastructure can all be classified as “assets.”
As you can imagine, in a modern organization, assets add up quickly and easily become disorganized.

Are You Effectively Managing
Your IT Assets?
Nearly 90% of security leaders say they don't have adequate visibility of the data that they are required to protect.*
Don’t let this happen to your company. Get a handle on your existing assets and continuously manage them with Cyvatar's cybersecurity-as-a-service managed cybersecurity solution.

You Need a Digitized Solution for a Digital Age
The Old Age
An “asset” used to simply include any computers in an organization. Historically, it was easy to inventory and manage physical IT assets.
Today, companies of all sizes use a huge number of technologies (from physical to digital) and quickly lose track of what they have.
The Digital Age
Assets now encompass far more than just your company computers - they include cloud, remote, and internal assets - and you need to take inventory of both applications and hardware.
Thanks to the evolution of technology, a single view of all assets can be built and managed continuously no matter what they are or where they exist.
Learn how Cyvatar provides the most secure solution with cybersecurity for your cloud-based assets ›

Your IT Asset Management Problem
You don’t know what assets your organization has and, therefore, can’t secure them.
It may not seem problematic to have poor cybersecurity asset inventory at first glance, but it’s inevitably causing you to be reactive in your cybersecurity efforts.
Asset inventory itself isn’t adequate; it’s just the start. Comprehensively managing digital assets is where proactive cybersecurity begins.
Not only do you not know about all of your assets, but managing the inventory feels overwhelming to say the least.
Your Cyvatar Solution
IT assets change quickly in the digital age and you need a cybersecurity partner who can change with them.
With continuous cybersecurity asset management, we’ll work with you to gain the insight to comprehensively identify and secure your digital assets.
People. Process. Technology.
When you work with Cyvatar, you get cybersecurity-as-a-service.
That means not only best-of-breed technology, but the best people to put it in place and the right process to keep your cybersecurity solution running smoothly.
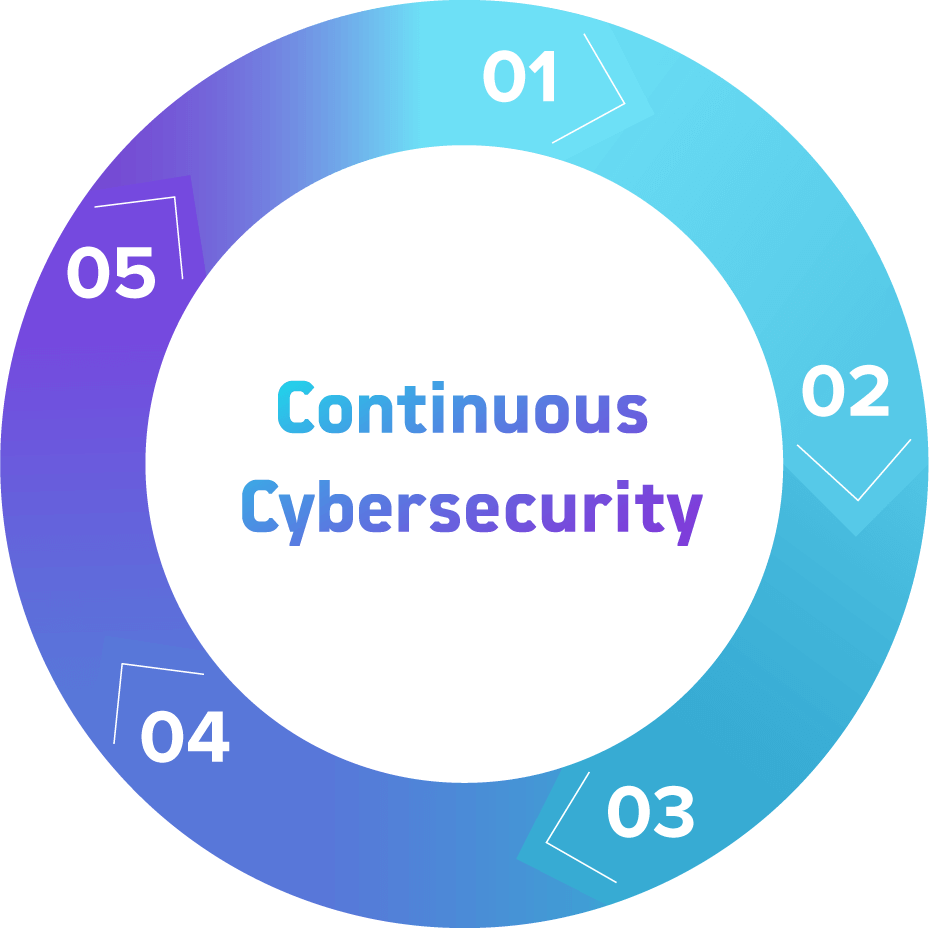
Cyvatar’s ICARM Methodology
1. Installation
The solution is implemented and installed.
2. Configuration
The technology is configured properly.
3. Assessment
An assessment is performed to identify risks.
4. Remediation
Remediation of the risks that were identified is performed.
5. Maintenance
Continuous maintenance and monitoring with monthly exclusive reporting. Repeat.